Content for TS 23.228 Word version: 19.1.0
1…
3…
4…
4.2.4…
4.3…
4.4…
4.13…
4.16…
5…
5.2…
5.3…
5.4…
5.4.7…
5.4.8…
5.4a…
5.5…
5.5.3…
5.6…
5.6.3…
5.7…
5.7.3…
5.7.5…
5.7.8…
5.8…
5.10…
5.11…
5.11.3…
5.11.3.3
5.11.3.4
5.11.4…
5.11.5…
5.11.5.3…
5.11.6…
5.12…
5.16…
5.16.2…
5.19…
5.20…
A…
E…
E.2.2…
G…
G.5…
H
I…
J…
K…
L…
M…
M.3…
N…
P…
Q…
Q.2.5…
R…
S…
T…
U…
U.2…
V…
W…
X…
Y…
Z…
AA…
AA.3…
AB…
AC…
AC.7…
AC.7.2…
AC.7.2.2
AC.7.2.3…
AC.7.4…
AC.7.9…
AC.7.9.3…
AC.7.10…
AC.7.10.4.2…
AC.9…
AC.10…
AC.11…
AD…
AE…
AF…
AG…
AF Support for authorization, signing and verification of third party user identity information in IMS
AF.1 General
AF.2 Architecture and functions
AF.2.1 Architecture
AF.2.2 Functional entities
AF.3 Procedure for signing and verification of third party user identity information in IMS
AF.4 Provisioning of IMS user specific properties
AF (Normative) Support for authorization, signing and verification of third party user identity information in IMS |R19| p. 440
AF.1 General p. 440
This Annex describes support for authorization, signing, and verification of third-party user identity information in IMS. A third party user in this context is a user belonging to a third party network which can be e.g. an Enterprise or private network.
The format of third-party user identity information used in IMS follows the definitions in draft-ietf-sipcore-callinfo-rcd-12 [107]. This allows to associate third party user identity information in IMS with Rich Call Data (RCD) information. An RCD server in the third-party network or optionally the HSS may store third party user identity information. The IMS network can retrieve the third-party user identity information from the RCD server during IMS session establishment and include this information in the outgoing SIP INVITE request.
Based on operator policies, third party user identity information can be signed by the originating IMS network and verified by the terminating IMS network. The process of signing and verifying third party user identity information follows draft-ietf-stir-passport-rcd-26 [108]. The AS for signing and the AS for verification need to be able to sign and verify following information elements: RCD information and RCD URL.
AF.2 Architecture and functions p. 440
AF.2.1 Architecture p. 440
Figure AF.2.1-1 shows the overall system architecture to support authorization, authentication, and verification of third party user identity information in IMS.
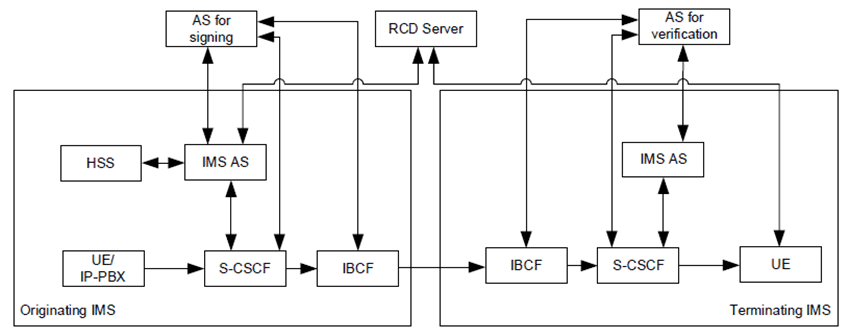
Following interfaces are added to the interfaces defined in the main clause of this document
- an interface between IMS entities (e.g. IMS AS) and the AS for signing; this interface is defined in draft-ietf-stir-passport-rcd-26 [108];
- an interface between IMS entities (e.g. IMS AS) and the AS for verification; this interface is defined in draft-ietf-stir-passport-rcd-26 [108] and TS 24.229;
- an interface between the IMS AS or the UE and the RCD server; this interface is out of scope of 3GPP.
AF.2.2 Functional entities p. 441
AF.2.2.1 HSS p. 441
HSS stores either one RCD server address or one RCD URL per IMPU or wildcarded IMPU, or it may store a limited set of RCD properties (e.g., caller name, company name, job title, and Email address), whose format shall be compliant with draft-ietf-sipcore-callinfo-rcd-12 [107], in the HSS repository data. Optionally, the RCD information, the RCD server address or the RCD URL may be provisioned per IMPU or wildcarded IMPU in the HSS repository data.
| RCD properties | Description |
|---|---|
| RCD Server Address | It refers to a server in a third party network storing IMS subscriber specific RCD information. This can be an IP address or a FQDN. |
| RCD URL | It refers to the URL from where RCD information of a specific IMS subscriber stored at an RCD server can be retrieved from. |
| RCD Information | It refers to a collection of properties associated with an IMS subscriber. Such properties can be caller name, company name, Email address, telephone number, job title. |
AF.2.2.2 IMS AS p. 441
Based on the received RCD properties from NEF, IMS AS validates the RCD information and stores the RCD information in HSS repository data by using the existing Nhss_ImsSDM_update service operation.
Originating IMS AS retrieves the RCD URL, RCD address or RCD information from the HSS. IMS AS can use the RCD server address or RCD URL to fetch the RCD information from the RCD server. Based on operator policies, IMS AS can invoke signing of the RCD information or the RCD URL.
Terminating IMS AS forwards the RCD URL or RCD information to the terminating UE after successful signature verification.
AF.2.2.3 UE and IP-PBX p. 441
Based on agreements and trust relationship between the third-party network and the IMS network, the third party network can provide RCD information or RCD URL in outgoing initial SIP INVITE requests. The IMS network, based on operator policy, may sign the provided RCD information or RCD URL.
The terminating UE may present third party user identity information of the calling-party to the called party, either received from RCD information in the SIP INVITE request or fetched from the RCD server based on the received RCD URL.
AF.2.2.4 IBCF p. 442
The IBCF, based on operator policies, can invoke signing and verification of the RCD information or the RCD URL received in SIP signalling.
AF.2.2.5 S-CSCF p. 442
For calls inside an IMS network, and based on operator policies, the S-CSCF can invoke signing and verification of the RCD information or the RCD URL received in SIP signalling.
AF.2.2.6 NEF p. 442
The NEF, in addition to its role as defined TS 23.502, is the entry point for provisioning of RCD properties by the AF via N33 reference point using the Nnef_ImsPP service operation.
An incoming provisioning request from the AF to the NEF may include RCD properties for a single IMPU or wildcarded IMPU. The NEF initiates Parameter Provisioning request to the IMS AS instance for the RCD server address, RCD URL or RCD information using the Nimsas_ImsPP service operation. The NEF may be configured with available IMS AS instances, or the NEF can discover IMS AS instances via NRF.
AF.3 Procedure for signing and verification of third party user identity information in IMS p. 442
Figure AF.3-1 depicts the procedure for signing and verification of third party user identity information in IMS.
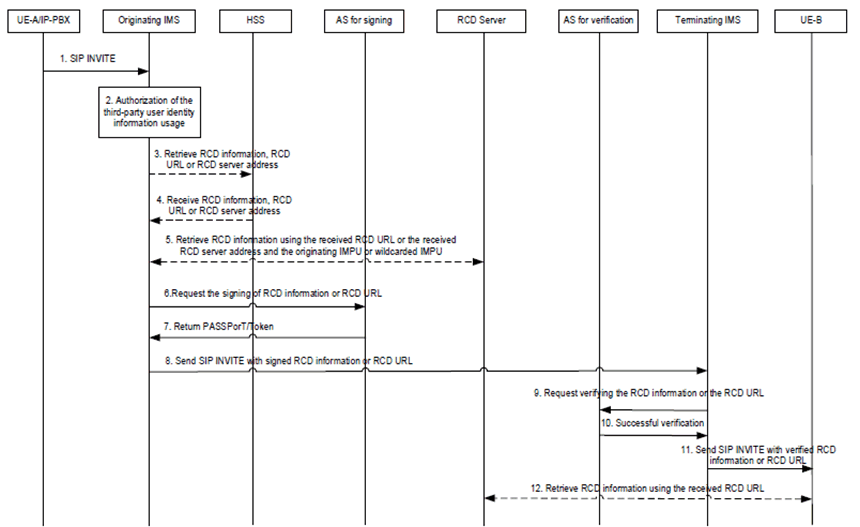
Step 1-2.
If the third party network is providing third party user identity information in the outgoing initial SIP INVITE request and is authorized to use third party user identity information, and based on operator policies, S-CSCF, IMS AS or IBCF invoke signing of the provided third party user identity information with a signing AS.
Step 3.
The originating IMS AS may retrieve RCD server address, RCD URL, or RCD information from the HSS, based on the originating IMPU or wildcarded IMPU.
Step 4.
The originating IMS AS may receive RCD server address, RCD URL, or RCD information from the HSS.
Step 5.
If the IMS AS has retrieved an RCD URL, the IMS AS, based on configuration, may retrieve the RCD information from the RCD server using the RCD URL. The IMS AS includes either the RCD URL or, if retrieved from the RCD server, the RCD information in the outgoing SIP INVITE request.
If the IMS AS has retrieved an RCD server address, the IMS AS provides the originating IMPU or wildcarded IMPU to the RCD server, to retrieve the RCD information. The IMS AS includes the retrieved RCD information in the outgoing SIP INVITE request.
Step 6-8.
The originating IMS network invokes signing of the RCD information or RCD URL included in the outgoing SIP INVITE request with a signing AS.
Step 9-10.
Based on operator policies, the S-CSCF, IMS AS or IBCF in the terminating IMS network invoke signature verification of the RCD information or RCD URL included in the incoming SIP INVITE request with a verification AS. The S-CSCF, IMS AS or IBCF in the terminating IMS network may reject the call when the signature verification is unsuccessful.
Step 11-12.
The terminating UE may present third party user identity information of the calling-party to the called party retrieved from RCD information, if present, in the SIP INVITE request. The called party may use the RCD URL, if present, to retrieve RCD information from the RCD server to download third party user identity information.
AF.4 Provisioning of IMS user specific properties p. 443
Support for provisioning of information which can be used for an IMS user in the IMS subsystem (e.g. RCD server address, RCD URL or RCD information for a single IMPU or wildcard IMPU as described in clause AF.2.2.6) is depicted below.
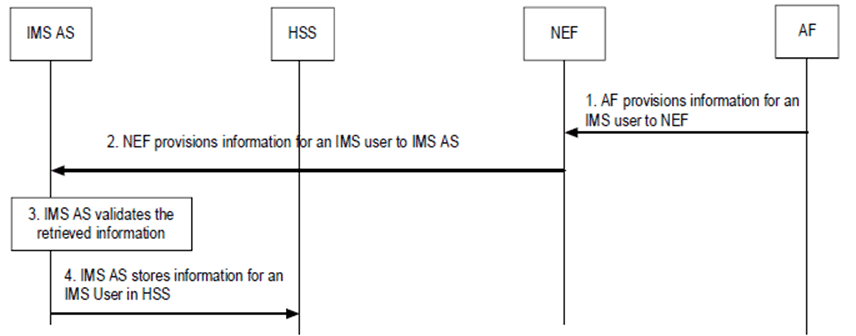
Step 1.
The AF (e.g. located in a third party network) provides information which can be used for an IMS user in the IMS subsystem, e.g. RCD server address, RCD URL or RCD information for a single IMPU or wildcard IMPU using Nnef_ImsPP_Create service operation as described in clause 5.2.6 of TS 23.502.
Step 2.
NEF after receiving the provisioning information can locate an IMS instance as described in clause AF.2.2.6 and provisions the received parameters to IMS AS using Nimsas_ImsPP_Create service operation.
Step 3.
IMS AS validates the retrieved information from NEF (e.g. check the syntax and semantics of the information).
Step 4.
IMS AS stores the IMS user information in the HSS repository data using existing Nhss_ImsSDM_Update service operation.