Content for TS 23.434 Word version: 19.4.2
0…
6…
8…
9…
9.3…
9.3.3…
9.3.8…
9.3.13…
9.3.20…
9.3.23…
9.4…
10…
10.3…
10.3.3…
10.3.7…
10.4…
11…
12…
13…
14…
14.3…
14.3.3
14.3.4
14.3.4A…
14.3.4A.5…
14.3.4A.8…
14.3.5…
14.3.9…
14.4…
15…
17…
18…
A…
0 Introduction
1 Scope
2 References
3 Definitions, symbols and abbreviations
3.1 Definitions
3.2 Abbreviations
4 Architectural requirements
4.1 General
4.2 Deployment models
4.3 Location management
4.4 Group management
4.5 Configuration management
4.6 Key management
4.7 Identity management
4.8 Network resource management
5 Involved business relationships
...
...
0 Introduction p. 20
This document specifies a functional architecture for service enabler architecture layer (SEAL) over 3GPP networks to support vertical applications (e.g. V2X applications). This functional architecture will include common application plane and signalling plane entities. A set of common services (e.g. group management, configuration management, location management) specified in this document can be shared across vertical applications.
The SEAL functional architecture takes into consideration the common capabilities to support mission critical and other vertical applications.
1 Scope p. 21
The present document specifies the functional architecture for service enabler architecture layer (SEAL) and the procedures, information flows and APIs for each service within SEAL in order to support vertical applications over the 3GPP system. The present document is applicable to vertical applications using E-UTRAN or NR access based on the EPS or 5GS architecture defined in TS 23.401, TS 23.246, TS 23.468, TS 23.501, and TS 23.247. To ensure efficient use and deployment of vertical applications over 3GPP systems this specification for SEAL services includes the group management, configuration management, location management, identity management, key management, network resource management, notification management, network slice capability enablement, data delivery and application data analytics enablement.
2 References p. 21
The following documents contain provisions which, through reference in this text, constitute provisions of the present document.
- References are either specific (identified by date of publication, edition number, version number, etc.) or non-specific.
- For a specific reference, subsequent revisions do not apply.
- For a non-specific reference, the latest version applies. In the case of a reference to a 3GPP document (including a GSM document), a non-specific reference implicitly refers to the latest version of that document in the same Release as the present document.
[1]
TR 21.905: "Vocabulary for 3GPP Specifications".
[2]
TS 22.104: "Service requirements for cyber-physical control applications in vertical domains".
[3]
TS 23.379: "Functional architecture and information flows to support Mission Critical Push To Talk (MCPTT); Stage 2".
[4]
TS 23.280: "Common functional architecture to support mission critical services; Stage 2".
[5]
TS 23.281: "Functional architecture and information flows to support Mission Critical Video (MCVideo); Stage 2".
[6]
TS 23.282: "Functional architecture and information flows to support Mission Critical Data (MCData); Stage 2".
[7]
TS 23.286: "Application layer support for V2X services; Functional architecture and information flows".
[8]
TS 23.222: "Functional architecture and information flows to support Common API Framework for 3GPP Northbound APIs; Stage 2".
[9]
TS 23.401: "General Packet Radio Service (GPRS) enhancements for Evolved Universal Terrestrial Radio Access Network (E-UTRAN) access".
[10]
TS 23.501: "System Architecture for the 5G System; Stage 2".
[11]
TS 23.502: "Procedures for the 5G System; Stage 2".
[12]
TS 23.303: "Proximity-based services (ProSe); Stage 2".
[13]
TS 23.682: "Architecture enhancements to facilitate communications with packet data networks and applications".
[14]
TS 23.002: "Network Architecture".
[15]
TS 23.228: "IP Multimedia Subsystem (IMS); Stage 2".
[16]
TS 23.468: "Group Communication System Enablers for LTE (GCSE_LTE); Stage 2".
[17]
TS 23.246: "Multimedia Broadcast/Multicast Service (MBMS); Architecture and functional description".
[18]
TS 23.203: "Policy and charging control architecture".
[19]
TS 23.503: "Policy and Charging Control Framework for the 5G System; Stage 2".
[20]
TS 26.348: "Northbound Application Programming Interface (API) for Multimedia Broadcast/Multicast Service (MBMS) at the xMB reference point".
[21]
TS 29.214: "Policy and charging control over Rx reference point".
[22]
TS 29.468: "Group Communication System Enablers for LTE (GCSE_LTE); MB2 Reference Point; Stage 3".
[23]
TS 36.300: "Evolved Universal Terrestrial Radio Access (E-UTRA) and Evolved Universal Terrestrial Radio Access Network (E-UTRAN); Overall description; Stage 2".
[24]
RFC 6733 (October 2012): "Diameter Base Protocol".
[25]
ETSI TS 102 894-2 (V1.2.1): "Intelligent Transport Systems (ITS); Users and applications requirements; Part 2: Applications and facilities layer common data dictionaryMultimedia Broadcast/Multicast Service (MBMS); Protocols and codecs".
[26]
ETSI TS 102 965 (V1.4.1): "Intelligent Transport Systems (ITS); Application Object Identifier (ITS-AID); Registration".
[27]
ISO TS 17419: "Intelligent Transport Systems - Cooperative systems - Classification and management of ITS applications in a global context".
[28]
TS 26.346: "Multimedia Broadcast/Multicast Service (MBMS); Protocols and codecs".
[29]
TS 33.434: "Service Enabler Architecture Layer (SEAL); Security aspects for Verticals".
[30]
TS 29.549: "Service Enabler Architecture Layer for Verticals (SEAL); Application Programming Interface (API) specification; Stage3".
[31]
TS 23.285: "Architecture enhancements for V2X services".
[32]
RFC 7252: "The Constrained Application Protocol (CoAP)".
[33]
RFC 8323: "CoAP (Constrained Application Protocol) over TCP, TLS, and WebSockets".
[34]
TS 23.288: "Architecture enhancements for 5G System (5GS) to support network data analytics services".
[35]
IEEE Std 802.1Qcc-2018: "Standard for Local and metropolitan area networks - Bridges and Bridged Networks - Amendment: Stream Reservation Protocol (SRP) Enhancements and Performance Improvements".
[36]
IEEE 802.1Q-2018: "IEEE Standard for Local and Metropolitan Area Networks-Bridges and Bridged Networks".
[37]
IEEE Std 802.1CB-2017: "Frame Replication and Elimination for Reliability".
[38]
TS 23.003: "Numbering, Addressing and Identification".
[39]
TS 23.247: "Architectural enhancements for 5G multicast-broadcast services; Stage 2".
[40]
TS 23.435: "Procedures for Network Slice Capability Exposure for Application Layer Enablement Service".
[41]
TS 28.531: "Management and orchestration; Provisioning".
[42]
TS 28.533: "Management and orchestration; Architecture framework".
[43]
TS 28.530: "Management and orchestration; Concepts, use cases and requirements".
[44]
TS 28.532: "Management and orchestration; Generic management services".
[45]
TS 28.552: "Management and orchestration; 5G performance measurements".
[46]
TS 28.554: "Management and orchestration; 5G end to end Key Performance Indicators (KPI)".
[47]
TS 28.104: "Management and orchestration; Management Data Analytics".
[48]
TS 23.433: "Service Enabler Architecture Layer for Verticals (SEAL); Data Delivery enabler for vertical applications".
[49]
TS 23.436: "Procedures for Application Data Analytics Enablement Service".
[50]
TS 23.273: "5G System (5GS) Location Services (LCS); Stage 2".
[51]
TS 29.572: "5G System; Location Management Services; Stage 3".
[52]
TS 23.256: "Support of Uncrewed Aerial Systems (UAS) connectivity, identification and tracking; Stage 2".
[53]
TS 37.355: "LTE Positioning Protocol (LPP)".
[54]
TS 29.122: "T8 reference point for Northbound APIs".
[55] Void
[56]
TS 23.482: "Functional architecture and information flows for AIML Enablement Service".
[57]
TS 23.586: "Architectural Enhancements to support Ranging based services and Sidelink Positioning".
[58]
TS 23.437: "Service Enabler Architecture Layer for Verticals (SEAL); Spatial map and Spatial anchors".
[59]
TS 23.438: "Service Enabler Architecture Layer for Verticals (SEAL); Digital Assets".
→ to date, still a draft
[60]
→ to date, still a draft
TS 23.271: "Functional stage 2 description of Location Services (LCS) ".
3 Definitions, symbols and abbreviations p. 23
3.1 Definitions p. 23
For the purposes of the present document, the terms and definitions given in TR 21.905 and the following apply. A term defined in the present document takes precedence over the definition of the same term, if any, in TR 21.905.
VAL user:
An authorized user, who can use a VAL UE to participate in one or more VAL services.
VAL user ID:
A generic name for the user ID of a VAL user within a specific VAL service.
VAL UE:
A UE that can be used to participate in one or more VAL services.
VAL client:
An entity that provides the client side functionalities corresponding to the vertical applications.
SEAL client:
An entity that provides the client side functionalities corresponding to the specific SEAL service.
VAL service:
A generic name for any service offered by the VAL service provider to their VAL users.
SEAL service:
A generic name for a common service (e.g. group management, configuration management, location management) that can be utilized by multiple vertical applications.
SEAL provider:
Provider of SEAL service(s).
VAL server:
A generic name for the server application function of a specific VAL service.
SEAL server:
An entity that provides the server side functionalities corresponding to the specific SEAL service.
VAL system:
The collection of applications, services, and enabling capabilities required to support a VAL service.
Primary VAL system:
VAL system where the VAL user profiles of a VAL user are defined.
Partner VAL system:
A VAL system that has a business relationship with the primary VAL system such that service can be offered to primary VAL system users.
VAL group:
A defined set of VAL UEs or VAL users configured for specific purpose in a VAL service.
VAL group home system:
The VAL system where the VAL group is defined.
VAL group member:
A VAL service user, whose VAL user ID is listed in a particular VAL group.
VAL stream:
A time sensitive communication stream is used to transport a time sensitive data flow, and is defined by a stream specification (which identifies a source and destination of the data flow) and a traffic specification (which defines the characteristics of the data flow). VAL stream is identified by a VAL stream ID.
Vertical:
See vertical domain.
Vertical application:
An application catering to a specific vertical.
MBS session announcement:
Mechanism to provide the necessary information to the NRM client to enable the reception of the VAL service data via the MBS session.
For the purposes of the present document, the following terms and definitions given in TS 22.104 apply:
Vertical domain
For the purpose of the present document, the following terms given in TS 23.247 apply:
MBS session
MBS service area
MB-SMF service area
3.2 Abbreviations p. 24
For the purposes of the present document, the abbreviations given in TR 21.905 and the following apply. An abbreviation defined in the present document takes precedence over the definition of the same abbreviation, if any, in TR 21.905.
5GS
5G System
5GVN
5G Virtual Network
CAPIF
Common API Framework for northbound APIs
CNC
Centralized Network Configuration
CRUDN
Create, Retrieve, Update, Delete and Notify
EPC
Evolved Packet Core
GPSI
Generic Public Subscription Identifier
LWP
Light-weight Protocol
NEF
Network Exposure Function
NR
New Radio
NOP
Network Operator
NSaaS
Network Slice as a Service
PCC
Policy and Charging Control
SCEF
Service Capability Exposure Function
SEAL
Service Enabler Architecture Layer for Verticals
SEAL-UU
Service Enabler Architecture Layer for Verticals, Universal UE-network interface
TSC
Time Sensitive Communication
TSN
Time Sensitive Networking
VAL
Vertical Application Layer
4 Architectural requirements p. 25
4.1 General p. 25
4.1.1 Description p. 25
This subclause specifies the general requirements for SEAL.
4.1.2 Requirements p. 25
[AR-4.1.2-a]
The SEAL shall support applications from one or more verticals.
[AR-4.1.2-b]
The SEAL shall support multiple applications from the same vertical.
[AR-4.1.2-c]
The SEAL shall offer SEAL services as APIs to the vertical applications.
[AR-4.1.2-d]
The SEAL shall support notification mechanism for SEAL service events.
[AR-4.1.2-e]
The API interactions between the vertical application server(s) and SEAL server(s) shall conform to CAPIF as specified in TS 23.222.
[AR-4.1.2-f]
The SEAL server(s) shall provide a service API compliant with CAPIF as specified in TS 23.222.
[AR-4.1.2-g]
The SEAL shall leverage the satellite connectivity.
[AR-4.1.2-h]
The SEAL shall support discontinuous coverage of satellite connectivity.
[AR-4.1.2-i]
The SEAL shall support managing S&F operations regarding satellite connectivity in EPS.
4.2 Deployment models p. 25
4.2.1 Description p. 25
This subclause specifies the requirements for various deployment models.
4.2.2 Requirements p. 25
[AR-4.2.2-a]
The SEAL shall support deployments in which SEAL services are deployed only within PLMN network.
[AR-4.2.2-b]
The SEAL shall support deployments in which SEAL services are deployed only outside of PLMN network.
[AR-4.2.2-c]
The SEAL shall support deployments in which SEAL services are deployed both within and outside the PLMN domain at the same time.
[AR-4.2.2-d]
The SEAL shall support SEAL capabilities for centralized deployment of vertical applications.
[AR-4.2.2-e]
The SEAL shall support SEAL capabilities for distributed deployment of vertical applications.
4.3 Location management p. 26
4.3.1 Description p. 26
This subclause specifies the requirements for location management service.
4.3.2 On-network functional model requirements p. 26
[AR-4.3.2-a]
The SEAL shall enable sharing location data between client and server for vertical applications usage.
[AR-4.3.2-b]
The SEAL shall support different granularity of location data, as required by the vertical application.
[AR-4.3.2-c]
The SEAL shall support requests for on-demand location reporting.
[AR-4.3.2-d]
The SEAL shall support client location reporting based on triggers.
[AR-4.3.2-e]
The SEAL shall enable vertical applications to receive updates to the location information.
[AR-4.3.2-f]
The SEAL shall enable sharing the network location information obtained from the 3GPP network systems to the vertical applications.
[AR-4.3.2-g]
The SEAL shall provide a mechanism to enable vertical applications to obtain a list of UE(s), and the location information of each UE, in the proximity to a designated/requested location.
[AR-4.3.2-h]
The SEAL shall support the Geofencing.
[AR-4.3.2-i]
The SEAL shall support the location history store and retrieve.
[AR-4.3.2-j]
The SEAL shall support the UE location reporting with more information (e.g. velocity) to the vertical application.
[AR-4.3.2-k]
The SEAL shall support the stored UE location information reusing.
[AR-4.3.2-l]
The SEAL shall support the adaptive location reporting based on the UE moving trend.
[AR-4.3.2-m]
The SEAL shall enable optimizing the location service operations when the multiple UEs are sharing the same location.
4.3.3 Off-network functional model requirements |R18| p. 26
[AR-4.3.3-a]
The SEAL shall support on-demand location reporting and event-triggered location reporting within PC5 communication.
4.4 Group management p. 26
4.4.1 Description p. 26
This subclause specifies the requirements for group management service.
4.4.2 Requirements p. 26
[AR-4.4.2-a]
The SEAL shall enable group management operations (e.g. CRUDN) by the authorized users or VAL server.
[AR-4.4.2-b]
The SEAL shall enable creation of group to be used by one or more vertical applications within the same VAL system.
[AR-4.4.2-c]
The SEAL shall enable two or more groups to be merged (temporarily or permanently) into a single group by the authorized users or VAL server wherein all the group members of the constituent groups are designated as members of the merged group.
4.5 Configuration management p. 27
4.5.1 Description p. 27
This subclause specifies the requirements for configuration management service.
4.5.2 Requirements p. 27
[AR-4.5.2-a]
The SEAL shall enable configuring service specific configuration data applicable to vertical applications.
[AR-4.5.2-b]
The SEAL shall support configuring data applicable to different vertical applications.
4.6 Key management p. 27
4.6.1 Description p. 27
This subclause specifies the requirements for key management service.
4.6.2 Requirements p. 27
[AR-4.6.2-a]
The SEAL shall support secure distribution of security related information (e.g. encryption keys).
[AR-4.6.2-b]
The SEAL shall support all communications in SEAL ecosystem to be secured.
4.7 Identity management p. 27
4.7.1 Description p. 27
This subclause specifies the requirements for identity management service.
4.7.2 Requirements p. 27
[AR-4.7.2-a]
The SEAL shall enable the access to SEAL services from the vertical application layer entities to be authorized.
4.8 Network resource management p. 27
4.8.1 Description p. 27
This subclause specifies the requirements for network resource management service.
4.8.2 Requirements p. 27
[AR-4.8.2-a]
The SEAL shall enable support for unicast bearer establishment and modification to support service KPIs for VAL communications.
[AR-4.8.2-b]
The SEAL shall enable support for multicast bearer establishment and modification to support service KPIs for VAL communications.
[AR-4.8.2-c]
The SEAL shall support announcement of multicast bearers to the UEs.
[AR-4.8.2-d]
The SEAL shall support switching of bearers between unicast and multicast.
[AR-4.8.2-e]
The SEAL shall support multicast bearer quality detection.
[AR-4.8.2-f]
The SEAL shall enable support for unicast PDU session establishment and modification to support service KPIs for VAL communications.
[AR-4.8.2-g]
The SEAL shall enable support for MBS session (multicast or broadcast type) establishment and modification to support service KPIs for VAL communications.
[AR-4.8.2-h]
The SEAL shall support announcement of MBS session (multicast or broadcast type) to the UEs.
[AR-4.8.2-i]
The SEAL shall support switching of between unicast PDU session and MBS session (multicast or broadcast type).
[AR-4.8.2-j]
The SEAL shall support MBS session (multicast or broadcast type) quality detection.
5 Involved business relationships p. 28
Figure 5-1 shows the business relationships that exist and that are needed to support a single VAL user.
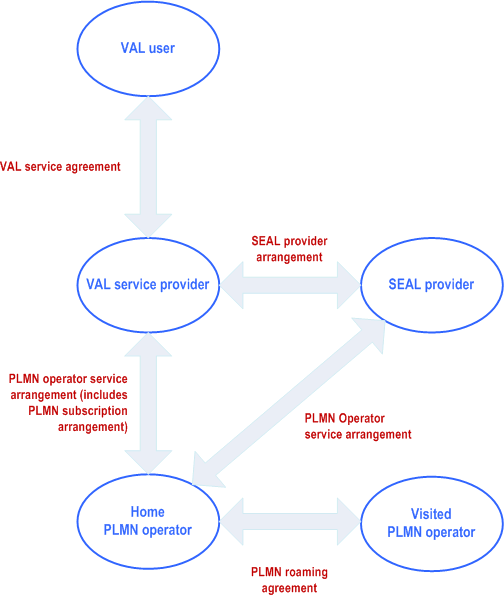
The VAL user belongs to a VAL service provider based on a VAL service agreement between the VAL user and the VAL service provider. The VAL service provider can have VAL service agreements with several VAL users. The VAL user can have VAL service agreements with several VAL service providers.
The VAL service provider and the home PLMN operator can be part of the same organization, in which case the business relationship between the two is internal to a single organization.
The VAL service provider can have SEAL provider arrangements with multiple SEAL providers and the SEAL provider can have PLMN operator service arrangements with multiple home PLMN operators. The SEAL provider and the VAL service provider or the home PLMN operator can be part of the same organization, in which case the business relationship between the two is internal to a single organization.
The home PLMN operator can have PLMN operator service arrangements with multiple VAL service providers and the VAL service provider can have PLMN operator service arrangements with multiple home PLMN operators. As part of the PLMN operator service arrangement between the VAL service provider and the home PLMN operator, PLMN subscription arrangements can be provided which allows the VAL UEs to register with home PLMN operator network.
The home PLMN operator can have PLMN roaming agreements with multiple visited PLMN operators and the visited PLMN operator can have PLMN roaming agreements with multiple home PLMN operators.