Content for TS 33.501 Word version: 19.1.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
6.6 UP security mechanisms
6.6.1 UP security policy
6.6.2 UP security activation mechanism
6.6.3 UP confidentiality mechanisms
6.6.4 UP integrity mechanisms
6.6.4.1 General
6.6.4.2 UP integrity mechanisms between the UE and the gNB
6.6.4.3 UP integrity mechanisms between the UE and the ng-eNB
...
...
6.6 UP security mechanisms p. 75
6.6.1 UP security policy p. 75
The SMF shall provide UP security policy for a PDU session to the ng-eNB/gNB during the PDU session establishment procedure as specified in TS 23.502.
The UP security policy shall indicate whether UP confidentiality and/or UP integrity protection shall be activated or not for all DRBs belonging to that PDU session. The UP security policy shall be used to activate UP confidentiality and/or UP integrity for all DRBs belonging to the PDU session.
The ng-eNB/gNB shall activate UP confidentiality and/or UP integrity protection per each DRB, according to the received UP security policy, using RRC signalling as defined in clause 6.6.2. If the user plane security policy indicates "Required" or "Not needed", the ng-eNB/gNB shall not overrule the UP security policy provided by the SMF. If the ng-eNB/gNB cannot activate UP confidentiality and/or UP integrity protection when the received UP security policy is "Required", the ng-eNB/gNB shall reject establishment of UP resources for the PDU Session and indicate reject-cause to the SMF. If the received UP security policy is "Not needed", then the establishment of the PDU Session shall proceed as described in TS 23.502. Only if the UE indicates that it supports use of integrity protection with ng-eNB, the ng-eNB can activate UP integrity protection.
At an Xn-handover from the source ng-eNB/gNB to the target ng-eNB/gNB, the source ng-eNB/gNB shall include in the HANDOVER REQUEST message, the UE's UP security policy. If the UP security policy is 'Required', the target ng-eNB/gNB shall reject all PDU sessions for which it cannot comply with the corresponding received UP security policy and indicate the reject-cause to the SMF. For the accepted PDU sessions, the target ng-eNB/gNB shall activate UP confidentiality and/or UP integrity protection per DRB according to the received UE's UP security policy and shall indicate that to the UE in the HANDOVER COMMAND by the source ng-eNB/gNB. Only if the UE indicates that it supports use of integrity protection with ng-eNB, the target ng-eNB can activate UP integrity protection.
If the UE receives an indication in the HANDOVER COMMAND that UP integrity protection and/or UP encryption for a PDU session is enabled at the target ng-eNB/gNB, the UE shall generate or update the UP encryption key and/or UP integrity protection key and shall activate UP encryption and/or UP integrity protection for the respective PDU session.
Further, in the Path-Switch message, the target ng-eNB/gNB shall send the UE's UP security policy and corresponding PDU session ID received from the source ng-eNB/gNB to the SMF. The SMF shall verify that the UE's UP security policy received from the target ng-eNB/gNB is the same as the UE's UP security policy that the SMF has locally stored. If there is a mismatch, the SMF shall send its locally stored UE's UP security policy of the corresponding PDU sessions to the target ng-eNB/gNB. This UP security policy information, if included by the SMF, is delivered to the target ng-eNB/gNB in the Path-Switch Acknowledge message. The SMF shall support logging capabilities for this event and may take additional measures, such as raising an alarm.
If the target ng-eNB/gNB receives UE's UP security policy from the SMF in the Path-Switch Acknowledge message, the target ng-eNB/gNB shall update the UE's UP security policy with the received UE's UP security policy. If UE's current UP confidentiality and/or UP integrity protection activation is different from the received UE's UP security policy, then the target ng-eNB/gNB shall initiate intra-cell handover procedure which includes RRC Connection Reconfiguration procedure to reconfigure the DRBs to activate or de-activate the UP integrity/confidentiality as per the received policy from SMF.
In case of the target ng-eNB/gNB receives both UE security capability and UP security policy, then ng-eNB/gNB initiates the intra-cell handover procedure which contains selected algorithm and an NCC to the UE. New UP keys shall be derived and used at both the UE and the target ng-eNB/gNB.
At an N2-handover the SMF shall send the UE's UP security policy to the target ng-eNB/gNB via the target AMF. The target ng-eNB/gNB shall reject all PDU sessions for which it cannot comply with the corresponding received UP security policy and indicate the reject-cause to the SMF via the target AMF. For all other PDU sessions, the target ng-eNB/gNB shall activate UP confidentiality and/or UP integrity protection per DRB according to the received UE's UP security policy. Only if the UE indicates that it supports use of integrity protection with ng-eNB, the target ng-eNB can activate UP integrity protection.
At interworking-handover from EPS to 5GS, the SMF+PGW-C provides the UE's UP security policy to the target ng-eNB/gNB via the target AMF. The target ng-eNB shall determine from the UP security policy received from the AMF together with the UE indication that it supports user plane integrity protection with ng-eNB in UE EPS security capabilities (i.e. bit EIA7), whether to activate user plane integrity protection with the UE or not. The target ng-eNB/gNB shall reject all DRBs for which it cannot comply with the corresponding UP integrity protection policy in the UP security policy and indicate the reject-cause to the source MME via the target AMF. For all other DRBs, the target ng-eNB/gNB shall activate UP integrity protection per DRB according to the used UP security policy. Only if the UE indicates that it supports use of user plane integrity protection with ng-eNB, the target ng-eNB can activate UP integrity protection. If the target AMF detects in a Registration procedure following interworking-handover from EPS to 5GS, and becomes aware of that there is a mismatch between the UE EPS security capabilities received from the source MME and the one received from the UE, and that the target ng-eNB may not have the UE capability indicating UP IP support in UE EPS security capabilities, then the AMF shall send an N2 CONTEXT MODIFICATION REQUEST message to inform the target ng-eNB about the correct UE EPS security capabilities and target ng-eNB shall take the new UE EPS security capabilities into account.
6.6.2 UP security activation mechanism p. 76
AS UP integrity protection and ciphering activation shall be done as part of the DRB addition procedure using RRC Connection Reconfiguration procedure as described in this clause, see Figure 6.6.2-1.
The SMF shall send the UP security policy to the gNB/ng-eNB as defined in clause 6.6.1.
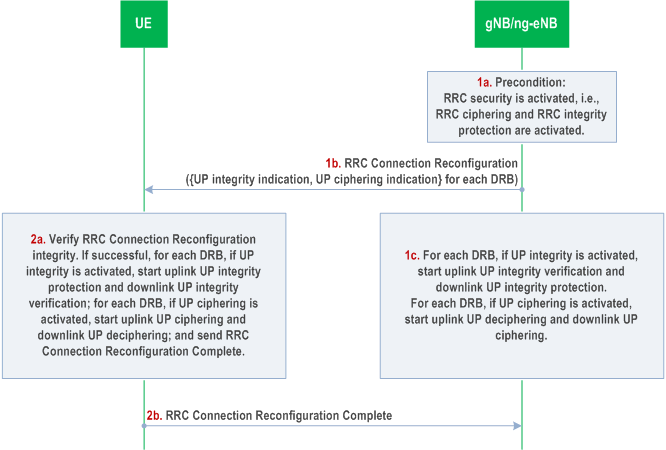
Step 1a.
If UP integrity protection is not activated for DRBs, the gNB/ng-eNB and the UE shall not integrity protect the traffic of such DRB and shall not put MAC-I into PDCP packet.
If UP ciphering is not activated for DRBs, the gNB/ng-eNB and the UE shall not cipher the traffic of such DRBs.
This RRC Connection Reconfiguration procedure which is used to add DRBs shall be performed only after RRC security has been activated as part of the AS security mode command procedure defined in clause 6.7.4.
Step 1b.
The gNB/ng-eNB shall send the RRC Connection Reconfiguration message to the UE for UP security activation containing indications for the activation of UP integrity protection and ciphering for each DRB according to the security policy.
Step 1c.
If UP integrity protection is activated for DRBs as indicated in the RRC Connection Reconfiguration message, and if the gNB/ng-eNB does not have KUPint, the gNB/ng-eNB shall generate KUPint and UP integrity protection for such DRBs shall start at the gNB/ng-eNB. Similarly, if UP ciphering is activated for DRBs as indicated in the RRC Connection Reconfiguration message, and if the gNB/ng-eNB does not have KUPenc, the gNB/ng-eNB shall generate KUPenc and UP ciphering for such DRBs shall start at the gNB/ng-eNB.
Step 2a.
UE shall verify the RRC Connection Reconfiguration message. If successful:
Step 2a.1.
Step 2b.
If UP integrity protection is activated for DRBs as indicated in the RRC Connection Reconfiguration message, and if the UE does not have KUPint, the UE shall generate KUPint and UP integrity protection for such DRBs shall start at the UE.
Step 2a.2.
Similarly, if UP ciphering is activated for DRBs as indicated in the RRC Connection Reconfiguration message, and if the UE does not have KUPenc, the UE shall generate KUPenc and UP ciphering for such DRBs shall start at the UE
If the UE successfully verifies integrity of the RRC Connection Reconfiguration message, the UE shall send the RRC Connection Reconfiguration Complete message to the gNB/ng-eNB.
6.6.3 UP confidentiality mechanisms p. 78
The PDCP protocol, as specified in TS 38.323 between the UE and the NG-RAN, shall be responsible for user plane data confidentiality protection.
The use and mode of operation of the 128-bit NEA algorithms are specified in Annex D.
The input parameters to the 128-bit NEA algorithms as described in Annex D are the message packet, an 128-bit cipher key KUPenc as KEY, a 5-bit bearer identity BEARER which value is assigned as specified by TS 38.323, the 1-bit direction of transmission DIRECTION, the length of the keystream required LENGTH and a bearer specific, and direction dependent 32-bit input COUNT which corresponds to the 32-bit PDCP COUNT.
6.6.4 UP integrity mechanisms p. 78
6.6.4.1 General |R17| p. 78
The PDCP protocol, as specified in TS 38.323 between the UE and the NG-RAN, shall be responsible for user plane data integrity protection.
6.6.4.2 UP integrity mechanisms between the UE and the gNB |R17| p. 78
The use and mode of operation of the 128-bit NIA algorithms are specified in Annex D.
The input parameters to the 128-bit NIA algorithms as described in Annex D are, the message packet, a 128-bit integrity key KUPint as KEY, a 5-bit bearer identity BEARER value of which is assigned as specified by TS 38.323, the 1-bit direction of transmission DIRECTION, and a bearer specific, and direction dependent 32-bit input COUNT which corresponds to the 32-bit PDCP COUNT.
If the gNB or the UE receives a PDCP PDU which fails integrity check with faulty or missing MAC-I after the start of integrity protection, the PDU shall be discarded.
6.6.4.3 UP integrity mechanisms between the UE and the ng-eNB |R17| p. 78
If the UE supports E-UTRA connected to 5GC, the UE shall indicate support of integrity protection by setting the EIA7 algorithm bit in 5G UE Security Capability IE (see clause 9.11.3.54 of TS 24.501) to indicate that the UE supports user plane integrity protection with an ng-eNB.
If the 128-NIA algorithm is signalled by the ng-eNB to the UE, clause 6.6.4.2 applies.
If the 128-EIA algorithm is signalled by the ng-eNB to the UE, the following applies:
- The use and mode of operation of the 128-EIA algorithms are specified in Annex B of TS 33.401.
- The input parameters to the 128-bit EIA algorithms as described in Annex B of TS 33.401 are, the message packet, a 128-bit integrity key KUPint as KEY, a 5-bit bearer identity BEARER value of which is assigned as specified by TS 38.323, the 1-bit direction of transmission DIRECTION, and a bearer specific, time and direction dependent 32-bit input COUNT which corresponds to the 32-bit PDCP COUNT.