Content for TS 33.501 Word version: 19.1.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
6.9 Security handling in mobility
6.9.2 Key handling in handover
6.9.2.1 General
6.9.2.1.1 Access stratum
6.9.2.1.2 Non access stratum
6.9.2.2 Key derivations for context modification procedure
6.9.2.3 Key derivations during handover
6.9.3 Key handling in mobility registration update
6.9.4 Key-change-on-the-fly
6.9.5 Rules on concurrent running of security procedures
6.9.6 Security handling in registration with AMF reallocation via direct NAS reroute
...
...
6.9 Security handling in mobility p. 93
6.9.1 Void
6.9.2 Key handling in handover p. 93
6.9.2.1 General p. 93
6.9.2.1.1 Access stratum p. 93
The general principle of key handling for KNG-RAN*/NH at handovers is depicted in Figure 6.9.2.1.1-1.
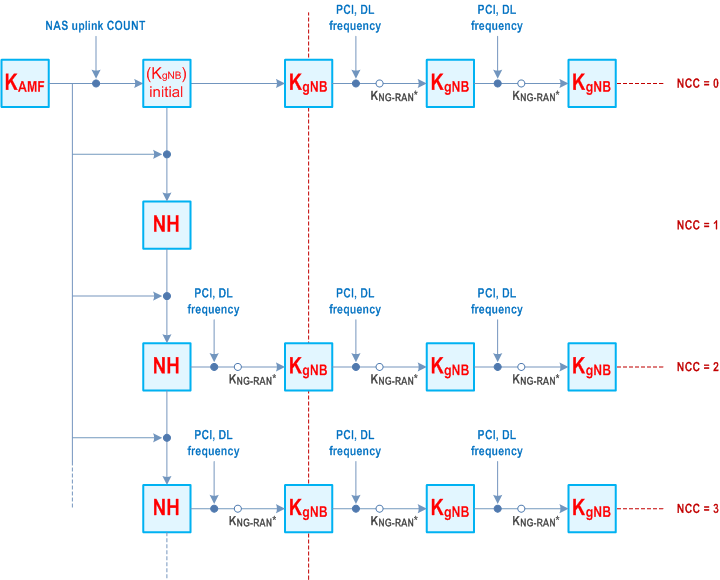
The following is an outline of the key handling model to clarify the intended structure of the key derivations. The detailed specification is provided in subclauses 6.9.2.2 and 6.9.2.3.
Whenever an initial AS security context needs to be established between UE and gNB/ng-eNB, AMF and the UE shall derive a KgNB and a Next Hop parameter (NH). The KgNB and the NH are derived from the KAMF. A NH Chaining Counter (NCC) is associated with each KgNB and NH parameter. Every KgNB is associated with the NCC corresponding to the NH value from which it was derived. At initial setup, the KgNB is derived directly from KAMF, and is then considered to be associated with a virtual NH parameter with NCC value equal to zero. At initial setup, the derived NH value is associated with the NCC value one.
Whether the AMF sends the KgNB key or the {NH, NCC} pair to the serving gNB/ng-eNB is described in detail in subclauses 6.9.2.2 and 6.9.2.3. The AMF shall not send the NH value to gNB/ng-eNB at the initial connection setup. The gNB/ng-eNB shall initialize the NCC value to zero after receiving NGAP Initial Context Setup Request message.
The UE and the gNB/ng-eNB use the KgNB to secure the communication between each other. On handovers and at transitions from RRC_INACTIVE to RRC_CONNECTED states (defined in clause 6.8.2.1), the basis for the KgNB that will be used between the UE and the target gNB/ng-eNB, called KNG-RAN*, is derived from either the currently active KgNB or from the NH parameter. If KNG-RAN* is derived from the currently active KgNB this is referred to as a horizontal key derivation (see Figure 6.9.2.1.1-1) and if the KNG-RAN* is derived from the NH parameter the derivation is referred to as a vertical key derivation (see Figure 6.9.2.1.1-1).
As NH parameters are only computable by the UE and the AMF, it is arranged so that NH parameters are provided to gNB/ng-eNBs from the AMF in such a way that forward security can be achieved.
On handovers with vertical key derivation the NH is further bound to the target PCI and its frequency ARFCN-DL before it is taken into use as the KgNB in the target gNB/ng-eNB. On handovers with horizontal key derivation the currently active KgNB is further bound to the target PCI and its frequency ARFCN-DL before it is taken into use as the KgNB in the target gNB/ng-eNB.
6.9.2.1.2 Non access stratum p. 94
During mobility, NAS aspects that need to be considered are the possible KAMF change, the possible NAS algorithm change at AMF change, and the possible presence of a parallel NAS connection. There is the possibility that the source AMF and the target AMF do not support the same set of NAS algorithms or have different priorities regarding the use of NAS algorithms. In this case, the target AMF re-derives the NAS keys from the existing KAMF (if unchanged) or derives the NAS keys from the new KAMF (if changed) using the NAS algorithm identities and NAS algorithm types as input to the NAS key derivation functions (see Annex A.8). When the KAMF has not changed, all inputs, in particular the KAMF, will be the same in the re-derivation except for the NAS algorithm identity. When the KAMF has changed, new NAS keys are derived irrespective of change in NAS algorithms.
In case the KAMF has changed or the target AMF decides to use NAS algorithms different from the ones used by the source AMF, the target AMF shall provide needed parameters to the UE as defined in clause 6.9.2.3.3 for N2-Handover (i.e., using NAS Container) and clause 6.9.3 for mobility registration update (i.e., using NAS SMC).
6.9.2.2 Key derivations for context modification procedure p. 94
As outlined in clause 6.9.2.1, whenever a fresh KgNB is calculated from the KAMF, the AMF shall transfer the KgNB to the serving ng-eNB/gNB in a message modifying the security context in the ng-eNB/gNB. The AMF and the UE shall compute the fresh KgNB as defined in Annex A.9 according to the rules in clause 6.9.4.4. An NCC value 0 is associated with the fresh KgNB. From the fresh KgNB, the ng-eNB/gNB and the UE shall compute the KNG-RAN* as described in Annex A.11 and Annex A.12 and then use the computed KNG-RAN* as the KgNB/KeNB as described in clause 6.9.4.4.
6.9.2.3 Key derivations during handover p. 95
6.9.2.3.1 Intra-gNB-CU handover and intra-ng-eNB handover p. 95
The gNB shall have a policy deciding at which intra-gNB-CU handovers the KgNB can be retained and at which a new KgNB needs to be derived. At an intra-gNB-CU handover, the gNB shall indicate to the UE whether to change or retain the current KgNB in the HO Command message. Retaining the current KgNB shall only be done during intra-gNB-CU handover.
If the current KgNB is to be changed, the gNB/ng-eNB and the UE shall derive a KNG-RAN* as in Annex A.11 / Annex A.12 using target PCI, its frequency ARFCN-DL/EARFCN-DL, and either NH or the current KgNB depending on the following criteria: the gNB shall use the NH for deriving KNG-RAN* if an unused {NH, NCC} pair is available in the gNB (this is referred to as a vertical key derivation), otherwise if no unused {NH, NCC} pair is available in the gNB, the gNB shall derive KNG-RAN* from the current KgNB (this is referred to as a horizontal key derivation). The gNB shall send the NCC used for the KNG-RAN*derivation to UE in HO Command message. The gNB/ng-eNB and the UE shall use the KNG-RAN* as the KgNB, after handover.
If the current KgNB is to be retained, the gNB and the UE shall continue using the current KgNB, after handover.
6.9.2.3.2 Xn-handover p. 95
In Xn handovers the source gNB/ng-eNB shall perform a vertical key derivation in case it has an unused {NH, NCC} pair. The source gNB/ng-eNB shall first compute KNG-RAN* from target PCI, its frequency ARFCN-DL/EARFCN-DL, and either from currently active KgNB in case of horizontal key derivation or from the NH in case of vertical key derivation as described in Annex A.11 / Annex A.12.
Next, the source gNB/ng-eNB shall forward the {KNG-RAN*, NCC} pair to the target gNB/ng-eNB. The target gNB/ng-eNB shall use the received KNG-RAN* directly as KgNB to be used with the UE. The target gNB/ng-eNB shall associate the NCC value received from source gNB/ng-eNB with the KgNB. The target gNB/ng-eNB shall include the received NCC into the prepared HO Command message, which is sent back to the source gNB/ng-eNB in a transparent container and forwarded to the UE by source gNB/ng-eNB.
When the target gNB/ng-eNB has completed the handover signalling with the UE, it shall send a NGAP PATH SWITCH REQUEST message to the AMF. Upon reception of the NGAP PATH SWITCH REQUEST, the AMF shall increase its locally kept NCC value by one and compute a new fresh NH from its stored data using the function defined in Annex A.10. The AMF shall use the KAMF from the currently active 5G NAS security context for the computation of the new fresh NH. The AMF shall then send the newly computed {NH, NCC} pair to the target gNB/ng-eNB in the NGAP PATH SWITCH REQUEST ACKNOWLEDGE message. The target gNB/ng-eNB shall store the received {NH, NCC} pair for further handovers and remove other existing unused stored {NH, NCC} pairs if any.
If the AMF had activated a new 5G NAS security context with a new KAMF, different from the 5G NAS security context on which the currently active 5G AS security context is based, but has not yet successfully performed a UE Context Modification procedure, the sent NGAP PATH SWITCH REQUEST ACKNOWLEDGE message shall in addition contain a NSCI (New Security Context Indicator). The AMF shall in this case derive a new initial KgNB from the new KAMF and the uplink NAS COUNT in the most recent NAS Security Mode Complete message as specified in Annex A.9. The AMF shall associate the derived new initial KgNB with a new NCC value equal to zero. Then, the AMF shall use {the derived new initial KgNB, the new NCC value initialized to zero} pair as the newly computed {NH, NCC} pair to be sent in the NGAP PATH SWITCH REQUEST ACKNOWLEDGE message. The gNB/ng-eNB shall in this case set the value of keySetChangeIndicator field to true in further handovers. The gNB/ng-eNB should in this case perform an intra-gNB-CU/intra-ng-eNB handover immediately.
6.9.2.3.3 N2-Handover p. 96
Upon reception of the NGAP HANDOVER REQUIRED message, if the source AMF does not change the active KAMF (meaning no horizontal KAMF derivation) and if AS key re-keying is not required, the source AMF shall increment its locally kept NCC value by one and compute a fresh NH from its stored data using the function defined in Annex A.10. The source AMF shall use the KAMF from the currently active 5GS NAS security context for the computation of the fresh NH. The source AMF shall send the fresh {NH, NCC} pair to the target AMF in the Namf_Communication_CreateUEContext Request message. The Namf_Communication_CreateUEContext Request message shall in addition contain the KAMF that was used to compute the fresh {NH, NCC} pair and its corresponding ngKSI and corresponding uplink and downlink NAS COUNTs.
If the source AMF had activated a new 5G NAS security context with a new KAMF, different from the 5G NAS security context on which the currently active 5G AS security context is based, but has not yet performed a UE Context Modification procedure, the Namf_Communication_CreateUEContext Request message shall in addition contain an indication that the KAMF sent by source AMF to target AMF is not in sync with the current KgNB used between the UE and the source gNB (i.e., keyAmfChangeInd) which means that AS key re-keying is required at the UE. Further, the source AMF shall derive a new KgNB associated with NCC=0 using the new KAMF and the uplink NAS COUNT from the last successful NAS SMC procedure with the UE and provide the {NH= newly derived KgNB, NCC=0} pair to the target AMF in the Namf_Communication_CreateUEContext Request message.
The source AMF uses its local policy to determine whether to perform horizontal KAMF derivation on currently active KAMF. If horizontal KAMF derivation is performed, the Namf_Communication_CreateUEContext Request shall contain an indication (i.e., keyAmfHDerivationInd ) that the new KAMF has been calculated, an indication (i.e., keyAmfChangeInd) that AS key re-keying is required at the UE, and the downlink NAS COUNT used in the horizontal derivation of the sent KAMF. The ngKSI for the newly derived KAMF key has the same value and the same type as the ngKSI of the current KAMF. Further, the source AMF shall derive a new KgNB associated with NCC=0 using the newly derived KAMF and the uplink NAS COUNT value of 232-1 as defined in Annex A.9. The source AMF shall include the{NH=newly derived KgNB, NCC=0} pair and the ngKSI for the newly derived KAMF key in the Namf_Communication_CreateUEContext Request as well.
The source AMF shall always increment the downlink NAS COUNT by one after sending the Namf_Communication_CreateUEContext Request message to the target AMF.
Unlike the S10 FORWARD RELOCATION REQUEST message in EPS, the Namf_Communication_CreateUEContext Request message in 5G shall not contain data and meta-data related to old 5G security context.
If the target AMF receives the indication of horizontal KAMF derivation (i.e., keyAmfHDerivationInd), it shall derive the NAS keys from the received KAMF as specified in clause A.8 and set the NAS COUNTs to zero. The target AMF shall create a NASC (NAS Container) containing the K_AMF_change_flag, the received downlink NAS COUNT, ngKSI, selected NAS security algorithms, and NAS MAC. The K_AMF_change_flag is set to one when the target AMF receives keyAmfHDerivationInd_. Otherwise, the K_AMF_change_flag is set to zero. If the target AMF does not receive keyAmfHDerivationInd but wants to change the NAS algorithms, it shall create a NASC using the selected NAS security algorithms in the same manner as the case for the horizontal KAMF derivation. However, the target AMF shall not set the NAS COUNTs to zero.
The target AMF shall calculate a 32-bit NAS MAC over the parameters included in the NASC using the KNASint key. The input parameters to the NAS 128-bit integrity algorithms as described in Annex D.3 shall be set as follows when calculating NAS MAC.
The calculation of NAS MAC shall be the 32-bit output of the selected NIA and shall use the following inputs:
- KEY: it shall be set to the corresponding KNASint;
- COUNT: it shall be set to 232-1;
- MESSAGE: it shall be set to the content of NAS Container as defined in TS 24.501;
- DIRECTION: its bit shall be set to 1; and
- BEARER: it shall be set to the value of the NAS connection identifier for 3GPP access.
6.9.2.3.4 UE handling p. 97
The UE behaviour is the same regardless if the handover is intra-gNB-CU, intra ng-eNB, Xn, or N2 with the exception that during intra-gNB-CU handover, the UE may retain the same key based on an indication from the gNB. The UE behaviour is also same in case of conditional handover, as specified in TS 38.300, i.e., the UE shall use the parameters of the selected target cell in KNG-RAN* derivations.
If the UE also receives a NASC (NAS Container) in the HO Command message, the UE shall update its NAS security context as follows:
- The UE shall verify the freshness of the downlink NAS COUNT in the NASC.
-
If the NASC indicates a new KAMF has been calculated (i.e., K_AMF_change_flag is one),
- The UE shall compute the horizontally derived KAMF using the KAMF from the current 5G NAS security context identified by the ngKSI included in the NASC and the downlink NAS COUNT in the NASC, as specified in Annex A.13.
- The UE shall assign the ngKSI included in the NASC to the ngKSI of the new derived KAMF. The UE shall further configure NAS security based on the horizontally derived KAMF and the selected NAS security algorithms in the NASC.
- The UE shall further verify the NAS MAC in the NASC as described in clause 6.9.2.3.3 and if the verification is successful, the UE shall further set the NAS COUNTs to zero.
-
If KAMF change is not indicated,
- If the verification is successful, the UE shall configure the NAS security based on the parameters included in the NASC but shall not set the NAS COUNTs to zero.
- The UE shall verify the NAS MAC in the NASC.
- The UE shall further set the downlink NAS COUNT value of the currently active NAS security context to the received downlink NAS COUNT value in the NASC.
-
If the HO Command message contained a NASC parameter with the K_AMF_change_flag set to one:
- The UE shall use the horizontally derived KAMF and the NAS COUNT value of 232-1 in the derivation of the temporary KgNB. The UE shall further process this temporary key as described in subclause 6.9.4.4.
-
Else:
- The UE handling related to key derivation shall be done as defined in clause 6.9.4.4.
- If the NCC value the UE received in the HO Command message from target ng-eNB/gNB via source ng-eNB/gNB is equal to the NCC value associated with the currently active KgNB/KeNB, the UE shall derive the KNG-RAN* from the currently active KgNB/KeNB and the target PCI and its frequency ARFCN-DL/EARFCN-DL using the function defined in Annex A.11 and A.12.
- If the UE received an NCC value that was different from the NCC associated with the currently active KgNB/KeNB, the UE shall first synchronize the locally kept NH parameter by computing the function defined in Annex A.10 iteratively (and increasing the NCC value until it matches the NCC value received from the source ng-eNB/gNB via the HO command message. When the NCC values match, the UE shall compute the KNG-RAN* from the synchronized NH parameter and the target PCI and its frequency ARFCN-DL/EARFCN-DL using the function defined in Annex A.11 and A.12.
6.9.3 Key handling in mobility registration update p. 98
The procedure shall be invoked by the target AMF after the receiving of a Registration Request message of type mobility registration update from the UE wherein the UE and the source AMF are identified by means of a temporary identifier 5G-GUTI.
The protocol steps for the source AMF and target AMF performing context transfer are as follows:
- The target AMF sends a message to the source AMF, this message contains the 5G-GUTI, the Access Type and the received Registration Request message.
-
The source AMF searches the data of the UE in the database and checks the integrity protection on the Registration Request message. The source AMF uses the 5G NAS security context corresponding to the Access Type to perform the integrity check.
-
If the UE is found and the integrity check succeeds, when the source AMF does not change KAMF according to its local policy, the source AMF shall send a response back that:
- shall include the SUPI, and
- may include any current 5G security context it holds.
-
If the UE is found and the integrity check succeeds, when the source AMF changes KAMF according to its local policy, the source AMF shall send a response back that:
- shall include the SUPI,
- keyAmfHDerivationInd, and
- may include a new 5G security context it derives from the current one it holds.
-
If the UE is found and the integrity check succeeds, when the source AMF does not change KAMF according to its local policy, the source AMF shall send a response back that:
- If the target AMF receives a response with a SUPI, it creates an entry and stores the 5G security context that may have beenreceived . If the target AMF receives a response indicating that the UE could not be identified, it shall initiate the subscription identification procedure described in clause 6.12.4 of the present document.
6.9.4 Key-change-on-the-fly p. 100
6.9.4.1 General p. 100
Key change on-the-fly consists of key refresh or key re-keying.
Key refresh shall be possible for KgNB, KRRCenc, KRRCint, KUPenc, and KUPint (if available ) and shall be initiated by the gNB/ng-eNB when a PDCP COUNTs are about to be re-used with the same Radio Bearer identity and with the same KgNB. The procedure is described in clause 6.9.4.5.
Key re-keying shall be possible for the KgNB, KRRCenc, KRRCint, KUPenc, and KUPint (if available). This re-keying shall be initiated by the AMF when a 5G AS security context different from the currently active one shall be activated. The procedures for doing this are described in clause 6.9.4.4.
AS Key change on-the-fly is accomplished using a procedure based on intra-cell handover. The following AS key changes on-the-fly shall be possible: local KgNB refresh (performed when PDCP COUNTs are about to wrap around), KgNB re-keying performed after an AKA run, activation of a native context after handover from E-UTRAN.
Key re-keying shall be possible for KNASenc and KNASint. Re-keying of KNASenc and KNASint shall be initiated by the AMF when a 5G NAS security context different from the currently active one shall be activated. The procedures for doing this are described in clause 6.9.4.2.
Re-keying of the entire 5G key hierarchy including KAMF shall be achieved by first re-keying KAMF, then KNASenc and KNASint, followed by re-keying of the KgNB and derived keys. For NAS key change on-the-fly, activation of NAS keys is accomplished by a NAS SMC procedure.
6.9.4.2 NAS key re-keying p. 100
After a primary authentication has taken place, new NAS keys from a new KAMF shall be derived, according to Annex A.8.
To re-activate a non-current full native 5G security context after handover from E-UTRAN the UE and the AMF take the NAS keys into use by running a NAS SMC procedure according to clause 6.7.2.
AMF shall activate fresh NAS keys from a primary authentication run or activate native security context, which has a sufficiently low NAS COUNT values, before the NAS uplink or downlink COUNT wraps around with the current security context.
6.9.4.3 NAS key refresh p. 100
If the AMF determines that NAS key refresh is required due to e.g. uplink or downlink NAS counter in the current security context is about to wrap around or based on a local operator policy to refresh the NAS keys after a certain time, the AMF may trigger a primary authentication run or may derive a new KAMF key using horizontal KAMF derivation upon the reception of an initial NAS message, e.g. a Registration Request or a Service Request using the uplink NAS COUNT value in the initial NAS message as described in clause 6.9.3 for mobility update registration. The AMF resets the corresponding uplink and downlink NAS counters and derive new NAS keys from the new KAMF key and the algorithms in use. The AMF activates the new KAMF key by running a NAS SMC with UE according to clause 6.7.2. When the new KAMF key is horizontally derived, the UE shall use the uplink NAS COUNT value that was sent in the initial NAS message to derive the same KAMF key as the AMF, reset the corresponding uplink and downlink NAS counters and then derive new NAS keys from the KAMF and the algorithms in use.
In this case, if AS security is also established between the UE and gNB/ng-eNB, then the AMF and the UE shall derive a new initial KgNB from the new KAMF as specified in Annex A.9. Further, the AMF and the UE shall associate the derived new initial KgNB with a new NCC value equal to zero. Further, the derived new initial KgNB/KeNB is sent by the AMF to the gNB/ng-eNB triggering the gNB/ng-eNB to perform the AS key re-keying as described in clause 6.9.4.4.
6.9.4.4 AS key re-keying p. 101
The KgNB/KeNB re-keying procedure is initiated by the AMF. It may be used under the following conditions:
- after a successful AKA run with the UE as part of activating a partial native 5G security context; or
- as part of synchronizing the NAS and the AS security contexts as a part of handover procedure, if a handover is occuring; or
- as part of re-activating a non-current full native 5G security context after handover from E-UTRAN according to clause 8.4; or
- to create a new KgNB from the current KAMF.
- The UE, AMF, and gNB/ng-eNB shall delete any old NH upon completion of the context modification.
-
The UE and AMF shall use the KAMF from the currently active 5G NAS security context for the computation of the fresh NH. The computation of NH parameter value sent in the Namf_
Communication_ Request, NGAP HANDOVER REQUEST, and NGAP PATH SWITCH REQUEST ACKNOWLEDGE messages shall be done according to clauses 6.9.2.3.2 and 6.9.2.3.3.CreateUEContext
6.9.4.5 AS key refresh p. 101
This procedure is based on an intra-cell handover. The KgNB chaining that is performed during a handover ensures that the KgNB is re-freshed with respect to the RRC and UP COUNT after the procedure. The gNB/ng-eNB shall indicate to the UE to change the current KgNB in intra-cell handover during this procedure.
6.9.5 Rules on concurrent running of security procedures p. 102
6.9.5.1 Rules related to AS and NAS security context synchronization p. 102
Concurrent runs of security procedures may, in certain situations, lead to mismatches between security contexts in the network and the UE. In order to avoid such mismatches, the following rules shall be adhered to:
- AMF shall not initiate any of the N2 procedures including a new key towards a UE if a NAS Security Mode Command procedure is ongoing with the UE.
- The AMF shall not initiate a NAS Security Mode Command towards a UE if one of the N2 procedures including a new key is ongoing with the UE.
- When the AMF has sent a NAS Security Mode Command to a UE in order to take a new KAMF into use and receives a request for an inter-AMF handover or an inter-RAT handover from the serving gNB/ng-eNB, the AMF shall wait for the completion of the NAS SMC procedure (i.e. receiving NAS Security Mode Complete) before initiating an inter-AMF handover or initiating an inter-RAT handover.
- When the AMF has initiated a NGAP UE Context Modification procedure in order to take a new KgNB into use, and receives a request for an inter-AMF handover from the serving gNB/ng-eNB, and decides not to change the KAMF for the inter-AMF handover, the AMF shall wait for the (successful or unsuccessful) completion of the UE Context Modification procedure before initiating an inter-AMF handover.
- Once the source AMF has initiated inter-AMF handover to the target AMF, or inter-system handover to the target MME, the source AMF shall not send any downlink NAS messages to the UE until it is aware that the handover has either failed or has been cancelled.
6.9.5.2 Rules related to parallel NAS connections p. 102
Concurrent runs of security procedures in parallel over two different NAS connections when terminated in the same AMF can lead to race conditions and mismatches between the security contexts in the network and the UE. In order to avoid such mismatches, the following rules shall be followed:
- The SEAF/AMF shall not initiate a primary authentication or NAS SMC procedure in case a primary authentication or a NAS SMC procedure is ongoing on a parallel NAS connection. Authentication procedures followed by a NAS SMC procedures taking the new 5G security context into use, shall be performed on one NAS signalling connection at a time.
- When the AMF has sent a NAS Security Mode Command to a UE in order to take a new KAMF into use and receives a context transfer request message for the UE from another AMF, the AMF shall wait for the completion of the NAS SMC procedure (e.g. receiving NAS Security Mode Complete) before transferring the context.
- The UE shall not initiate a NAS registration over a second NAS connection to an AMF of the same network before primary authentication on the first NAS connection is complete.
6.9.6 Security handling in registration with AMF reallocation via direct NAS reroute p. 102
In registration with AMF reallocation via direct NAS reroute, the initial AMF shall send the complete Registration Request in clear text to the target AMF.
In registration with AMF reallocation via direct NAS reroute, the initial AMF shall use its local policy to determine whether to perform horizontal KAMF derivation on current KAMF. As described in clause 6.9.3, if the initial AMF decides not to change KAMF, the initial AMF shall send the current security context to the target AMF; otherwise, the initial AMF shall derive new security context and send to the target AMF the derived security context and the indication of horizontal KAMF derivation (i.e., keyAmfHDerivationInd).
If the target AMF receives the indication of horizontal KAMF derivation (i.e., keyAmfHDerivationInd) from the initial AMF, it shall initiate NAS SMC. If the target AMF does not receive keyAmfHDerivationInd, the target AMF shall use the received security context from initial AMF and send protected NAS message including protected authentication request message if authentication is needed. The target AMF decides whether to perform authentication based on local policy.