Content for TS 33.127 Word version: 19.1.0
0…
5…
5.4…
5.6…
5.7…
6…
6.2.2…
6.2.3…
6.2.5…
6.3…
6.3.3…
6.3.4…
6.4…
7…
7.3…
7.4…
7.4.7…
7.5…
7.6…
7.7…
7.8…
7.9…
7.10…
7.11…
7.12…
7.13…
7.14…
7.15…
7.16…
8…
A…
A.2…
A.3…
A.4…
B…
D…
E…
E STIR/SHAKEN operation
E.1 General
E.2 STIR/SHAKEN
E.2.1 STIR/SHAKEN for telephony
E.2.2 STIR/SHAKEN for intra-network telephony
E.2.3 STIR/SHAKEN for messaging
E.2.4 Out of band SHAKEN
E.2.5 STIR/SHAKEN and forwarded calls
E.3 Enhanced caller data
E.3.1 General
E.3.2 RCD
E.3.3 eCNAM
E.4 STIR/SHAKEN call flow example
F Application to proprietary implementations
F.1 General
F.2 Implementation with proprietary Network Layers
F.3 Implementation with proprietary Service Layers
$ Change history
E STIR/SHAKEN operation p. 178
E.1 General p. 178
This Annex defines STIR (Secure Telephony Identity Revisited), SHAKEN (Secure Handling of Asserted information using toKENs), eCNAM (Enhanced Calling Name) and RCD (Rich Call Data) and their application to different call scenarios.
E.2 STIR/SHAKEN p. 178
E.2.1 STIR/SHAKEN for telephony p. 178
STIR (Secure Telephony Identity Revisited) and SHAKEN (Secure Handling of Asserted information using toKENs) are the frameworks to prevent the completion of illegally spoofed telephony sessions. Call spoofing is when a session originator changes the calling number to hide or change which calling number is shown on the telephony session display.
STIR provides the ability within SIP to authenticate caller ID, and SHAKEN defines the end-to-end architecture to implement caller ID authentication using STIR in the telephone network.
STIR/SHAKEN uses digital certificates, based on common public key cryptography techniques, to ensure the calling number of a telephony session is secure. Each telephone service provider obtains its digital certificates from a trusted certificate authority. The certificate technology enables verifying that the calling number is accurate and has not been spoofed.
Figure E.2.1-1 below depicts the SHAKEN reference architecture as specified in TS 24.229 when using end-to-end SIP signalling.
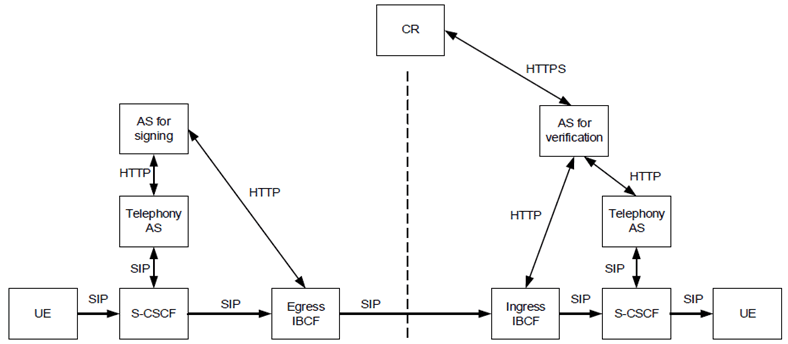
Figure E.2.1-1: SHAKEN reference architecture for end-to-end SIP signalling
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
It is based on IMS architecture. The "application server (AS) for signing" is an HTTP-based application server that performs the function of the authentication service defined in RFC 8224 for originating number identity and in RFC 8946 for diverting number identity. The "AS for verification" is an HTTP-based application server that performs the function of the verification service defined in RFC 8224 and in RFC 8946. Certificate Repository (CR) represents the publicly accessible store for public key certificates.
Either the Telephony AS or IBCF in the originating service provider's network invokes the AS for signing which creates a digital signature for the call called a PASSportT (Personal Assertion Token) assigned to a SIP Identity header. The IBCF or Telephony AS in the terminating service provider's network invokes the AS for verification which verifies the digital signature of the call. The AS includes a VERSTAT parameter in the P-Asserted-Identity or From header of the SIP INVITE request, with possible values of TN-Validation-Passed, TN-Validation-Failed or No-TN-Validation.
A SIP INVITE request might have one Identity added by an authentication service at the originating administrative domain and then other Identity header fields added by some further intermediaries. The presence of multiple Identity header fields within a SIP INVITE request raises the prospect that a verification service could receive a message containing both valid and invalid Identity header fields. As a guideline, RFC 8224 recommends that only if a verifier determines that all Identity header fields within a message are invalid should the request be considered to have an invalid identity. If at least one Identity header field value is valid and from a trusted source, then relying parties can use that header for authorization decisions regardless of whether other untrusted or invalid Identity headers appear in a request.
E.2.2 STIR/SHAKEN for intra-network telephony p. 179
Some telecommunication regulation authorities may force CSPs implementing STIR/SHAKEN even for intra-network voice sessions. Figure E.2.2-1 depicts the SHAKEN reference architecture for such scenario when using end-to-end SIP signalling. The Telephony AS is the default approach to provide STIR/SHAKEN capabilities, i.e. is capable of invoking the AS for signing on the originating side and AS for verification on the terminating side.
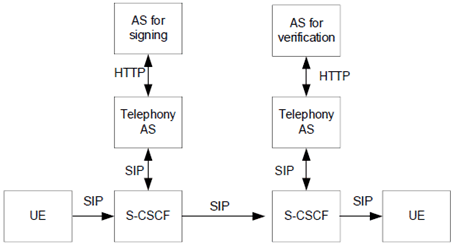
Figure E.2.2-1: SHAKEN reference architecture for intra-network telephony
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
E.2.3 STIR/SHAKEN for messaging p. 179
STIR/SHAKEN could apply to providing protection for textual and multimedia messaging as specified in the RFC 9475.
A PASSporT could be used to securely negotiate a session over which messages will be exchanged; this is applicable for example to the following RCS services: large message mode standalone messaging, 1-to-1 chat and group chat where messages are exchanged using MSRP (Message Session Relay Protocol) after the SIP session is established. In these scenarios, usage of STIR/SHAKEN is very similar to that for voice sessions.
In sessionless scenarios such as RCS pager mode standalone messaging service, a PASSporT could be generated on a per-message (i.e. SIP MESSAGE) basis with its own built-in message security. An Identity header could be added to any SIP MESSAGE request, but without some extension to the PASSporT claims, the PASSporT would offer no protection to the message content. In RFC 9475, PASSporT provides its own integrity check for message contents as part of its assertions through a new claim which is here defined to provide a hash over message contents. A new "msg" PASSporT Type is defined for that purpose. A new optional claim "msgi" provides a digest over a MIME body (i.e. body of the SIP MESSAGE). The PASSporT is conveyed in an Identity header field in the SIP MESSAGE request. The authentication and verification service procedures for populating that PASSporT follow the same procedures as for a voice session, with the addition of the "msgi" claim.
E.2.4 Out of band SHAKEN p. 180
In today's PSTN, and for the foreseeable future, the Identity header may fail to arrive at the terminating service provider's network for verification by their AS for verification because the call is not transmitted using SIP end to end. However, Out-of-Band SHAKEN remedies this problem. A possible scenario is described in Figure E.2.4-1.
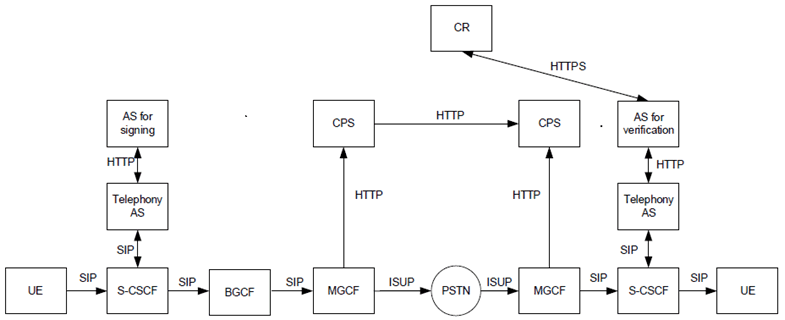
Figure E.2.4-1: Out of band SHAKEN reference architecture for non end-to-end SIP signalling
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
With this solution, the identity token is sent to the terminating service provider separately, out-of-band, through implementation of a Call Placement Service (CPS).All other SHAKEN steps for authentication, use of certificates and verification remain the same. CPS as defined in RFC 8816 permits the identity token to be stored during call processing and retrieved for verification purposes when a session is not using end-to-end SIP signalling, i.e. a leg in the session is using circuit switching and ISUP signalling.
Out-of-Band SHAKEN is used when a service provider wants to use STIR/SHAKEN for a call sent or received across a non-SIP network segment. For example, Out-of-Band SHAKEN would be used in the following situations:
- A service provider originating a call using TDM signalling would generate the applicable PASSporTs using their AS for signing and publish them to a CPS.
- An Intermediate Service Provider converting a session from SIP to TDM would publish all PASSporTs received in SIP signalling for that call to a CPS.
- An Intermediate Service Provider converting a call from TDM to SIP would retrieve all PASSporTs for that call from a CPS and insert them into the SIP signalling for that call.
- A service provider terminating a call using TDM signalling would retrieve all PASSporTs for that call from a CPS and verify the call using their AS for verification.
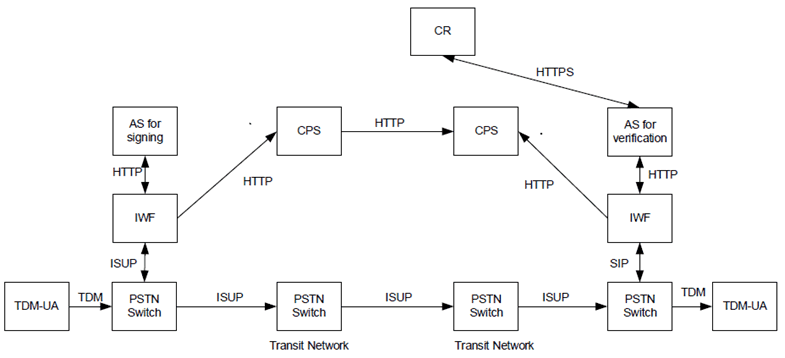
Figure E.2.4-2: Out of band SHAKEN reference architecture for end-to-end TDM signalling
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
E.2.5 STIR/SHAKEN and forwarded calls p. 181
In case of call forwarding, the original called party number is not the number to which a call is delivered. The SIP headers such as "History-Info", "Diversion" and "To" do not provide any cryptographic assurance of secure redirection. RFC 8946 extends the SIP identity token (i.e. PASSporT) with an explicit indication that the original called number no longer reflects the destination to which a call is intended to be delivered via a "div" parameter. It indicates a previous destination for a session during its routing process. When a retargeting entity receives a call signed with the SIP Identity token, it may act as an authentication service and create a new SIP Identity token containing the "div" parameter to attach to the session.
E.3 Enhanced caller data p. 181
E.3.1 General p. 181
Two approaches, namely Rich Call Data (RCD) and eCNAM (Enhanced Calling Name) build on STIR/SHAKEN to provide additional caller information rendered to the callee during alerting to encourage the callee to answer the session.
E.3.2 RCD p. 181
RCD is described in an IETF draft draft-ietf-stir-passport-rcd-12 [42]. RCD is of two main categories. The first data is a more traditional set of information about a caller associated with "display-name", typically a textual description of the caller in the SIP INVITE. The second category is a set of RCD that is defined as part of the jCard (JSON format for vCard) as specified in RFC 7095. RCD is inserted in the SIP Identity header token and is digitally signed. If a session is not authenticated and signed then RCD cannot be used. While RCD can be provided by an originating authentication service, an intermediary in the session path could also acquire RCD by querying a third-party service. Such a service effectively acts as a STIR authentication service, generating its own Identity token including RCD, and that token could be attached to a SIP session by either the originating or terminating side.
E.3.3 eCNAM p. 181
The Enhanced Calling Name (eCNAM) service defined in TS 24.196 provides the terminating user with a name that identifies the originating user, and metadata about that originating user (e.g. address, language, etc.), like with RCD. eCNAM data is managed by the originating network and stored in an authoritative database. To enable the terminating network to retrieve eCNAM data, the terminating service provider queries the database using the calling telephone number as the key, to obtain calling display name and other metadata.
In both RCD and eCNAM the terminating network shall populate the received name and received metadata elements in appropriate SIP headers in the INVITE request being forwarded to the terminating UE.
E.4 STIR/SHAKEN call flow example p. 182
The following procedure explains STIR/SHAKEN operation when SIP signalling is carried end-to-end between an originating and terminating service provider as illustrated in Figure E.4-1.
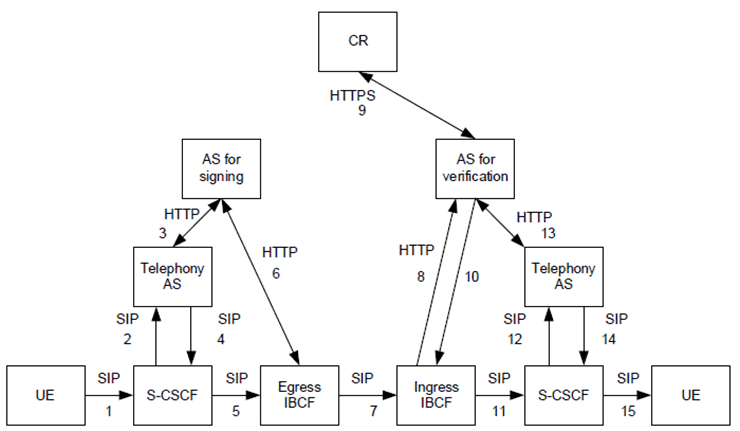
Figure E.4-1: SHAKEN reference call flow using end-to-end SIP signalling
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
1)
The originating UE, which first successfully registers to IMS creates a SIP INVITE request.
2)
The S-CSCF of the originating service provider passes the SIP INVITE request to the Telephony AS.
3)
The Telephony AS runs the telephony services related to the originating user and:
4)
- May send a signing request (HTTP POST request) to the AS for signing. AS for signing using its private key generates an Identity header as defined in RFC 8224 using the Caller ID to attest for the validity of the calling number. The AS for signing returns the signing response (HTTP 200 OK) containing the Identity header to telephony AS. The Telephony AS signs the SIP INVITE request with the SIP Identity header. The Telephony AS also obtains Identity header for each diverting identity as defined in RFC 8946.
- May not sign the SIP INVITE request with the SIP Identity header if it knows the egress IBCF supports invoking the AS for signing for providing an Identity header field.
The Telephony AS passes the SIP INVITE request back to the S-CSCF.
5)
The S-CSCF, through standard resolution, routes the telephony session to the egress IBCF.
6)
If the egress IBCF does not find an Identity header field in the received SIP INVITE request, the IBCF sends a signing request (HTTP POST request) to the AS for signing. When the response to the request is received, the IBCF shall include the value of the "identity" claim in an Identity header field in the SIP INVITE request. If the SIP INVITE request contains one or more History-Info header fields, that determine that one or several diversions have occurred, the IBCF sends a signing request for each of the identities to be signed if no corresponding Identity header fields are found in the SIP INVITE request. The IBCF shall include the value of the "identity" claim in an Identity header field in the SIP INVITE request.
7)
The SIP INVITE request is routed over the NNI through the standard inter-domain routing configuration. The terminating service provider ingress IBCF receives the SIP INVITE request containing one or more Identity header fields over the NNI.
8)
The IBCF uses the identity header fields to build and send a verification request (HTTPS POST request) to the AS for verification related to the originating identity and forwarding identities if the IBCF supports invoking the AS for verification.
9)
The AS for verification uses the "x5u" key in the Identity header field to determine the CR Uniform Resource Identifier (URI) and makes an HTTPS request to the CR. The AS for verification validates the certificate and then extracts the public key. It uses the public key to verify the signature in the Identity header field, which validates the Caller ID used when signing the SIP INVITE request on the originating service provider's AS for signing.
10)
The AS for verification returns a verification response (200 OK) to the ingress IBCF which adds the verification result (TN-Validation-Passed, TN-Validation-Failed, No-TN-Validation) as a VERSTAT parameter to the P-Asserted-Identity or From header in the SIP INVITE request. The TN-Validation-Failed result is associated with a failure response code to identify the specific error. The standard does not propose any authorization policy to follow based on the presence of a valid Identity header field, the presence of an invalid Identity header field or the absence of an Identity header field. However, it is anticipated that local policies could involve making different forwarding decisions or changing how the user is alerted or how identity is rendered in UE implementations.
11)
The ingress IBCF passes the SIP INVITE request to the terminating S-CSCF.
12)
The terminating S-CSCF passes the SIP INVITE request to the terminating Telephony AS.
13)
If the verification has not been performed by the ingress IBCF, the Telephony AS runs the verification procedure toward the AS for verification before running the telephony services related to the terminating identity.
14)
If the validation is successful, the SIP INVITE request is passed back to the terminating S-CSCF which continues to set up the session to the terminating UE.
15)
The terminating UE receives the SIP INVITE request and normal SIP processing of the session continues.
F (Normative) Application to proprietary implementations p. 184
F.1 General p. 184
The following clauses describe how the present document may be used to support LI for implementations that support 3GPP defined networks and services but use architectures, protocols, interfaces or procedures that do not align with the 3GPP specifications.
F.2 Implementation with proprietary Network Layers p. 184
Implementations using proprietary Network Layers for 3GPP defined networks and services may use the present document to describe the functional system requirements with the following changes:
- The LI architecture shall be adjusted such that the reportable events applicable to the network are still intercepted and reported.
- If the functionality of a network function listed in the present document is supported by another network function, the LI functions shall be implemented such that the xIRI events reportable by the original function are reported at whatever network function replaces the original function.
F.3 Implementation with proprietary Service Layers p. 184
Implementations using proprietary Service Layers for 3GPP defined services may use the present document to describe the functional system requirements with the following changes:
- The LI architecture shall be adjusted such that the reportable events applicable to the service are still intercepted and reported.
- If the implementation of a service does not utilize one of the network elements described in the clause for that service, any xIRI events reportable by network element shall be reported by the LI functions in whatever element replaces that element.