Content for TS 33.127 Word version: 19.1.0
0…
5…
5.4…
5.6…
5.7…
6…
6.2.2…
6.2.3…
6.2.5…
6.3…
6.3.3…
6.3.4…
6.4…
7…
7.3…
7.4…
7.4.7…
7.5…
7.6…
7.7…
7.8…
7.9…
7.10…
7.11…
7.12…
7.13…
7.14…
7.15…
7.16…
8…
A…
A.2…
A.3…
A.4…
B…
D…
E…
7.13 RCS
7.13.1 Background
7.13.2 Architecture
7.13.2.1 Overview
7.13.2.2 Deployment options
7.13.2.2.1 Implementations without a third party registration to the RCS Server
7.13.2.2.2 Implementations that have a file transfer localisation function
7.13.3 Target identities
7.13.4 IRI events
7.13.4.1 General RCS IRI events
7.13.4.2 RCS events for topologies without a third party registration to the RCS Server
7.13.4.3 RCS events for topologies utilising a file transfer localisation function
...
...
7.13 RCS p. 130
7.13.1 Background p. 130
Rich Communication Suite (RCS) is the platform that enables the delivery of communication experiences beyond voice and SMS, providing consumers with a number of services related to:
- Capability discovery for enhanced contacts information.
-
Standalone messaging:
- Pager mode.
- Large message mode.
-
Chat:
- 1-to-1.
- Group chat.
- File URL transfer for enhanced messaging.
- Upload and download of files through HTTP Content Server.
7.13.2 Architecture p. 131
7.13.2.1 Overview p. 131
The capabilities defined in this clause and the following subclauses apply to the LI for RCS. The LI architecture and functionality for RCS builds on the LI capabilities defined for IMS (see clause 7.4). When LI for RCS is required, the LI functions in IMS are provisioned as described in clause 7.4.
The network functions involved in providing the interception of RCS events are determined based on the deployment option, the network configuration, LI service scope and the RCS communication type. In general, the LI functions involved in the interception of RCS events are located either in the IMS core or in RCS specific network functions.
Additional topology options for RCS are described in clause 7.13.2.2.
The present document refers to any server that provides support, services or functions for RCS as an RCS Server. In general, RCS Servers are IMS Application Servers. The HTTP Content Server supports file upload, URI generation, and file download to allow for the transfer of files over RCS.
The following sub-clauses contain general stage 2 details for LI for RCS.
The RCS Servers shall have LI capabilities to generate xIRI records and xCC when RCS events related to the target UE are handled. The HTTP Content Server shall have LI capabilities to generate xIRI records and xCC when the target UE uploads or downloads a file and when any user downloads a file previously uploaded by a target. If an IRI-TF or CC-TF is required, the relevant RCS Server shall have the CC-TF. Figure 7.13.2.1-1 provides a reference point representation of the LI architecture for RCS interception.
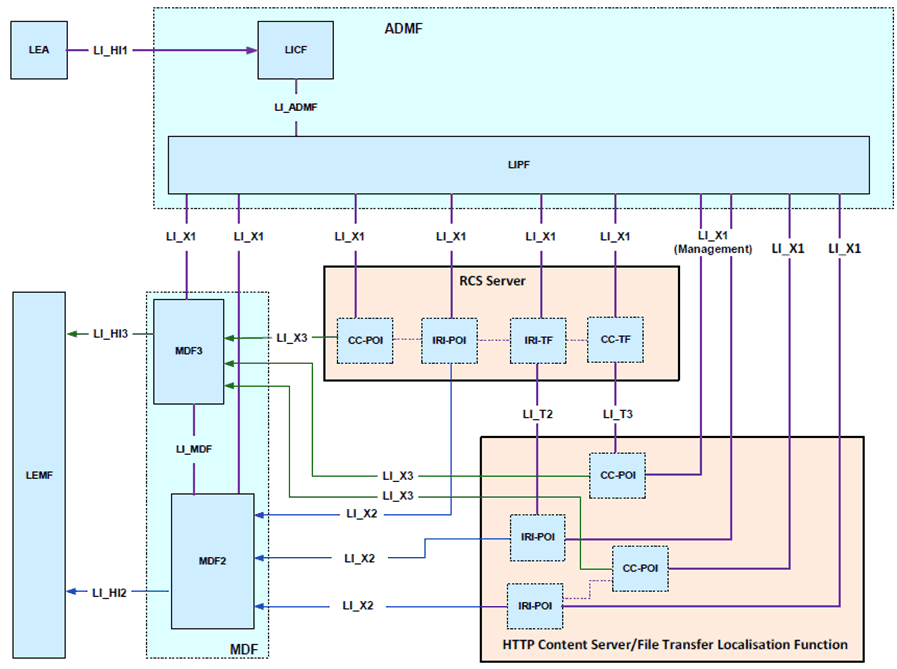
The LICF present in the ADMF receives the warrant from an LEA, derives the intercept information from the warrant and provides it to the LIPF.
The LIPF present in the ADMF provisions the IRI-POI present in each RCS Server, the IRI-TF in the relevant RCS Servers, the MDF2 and the MDF3 over the LI_X1 interfaces.
If the authentication method used to authenticate at the HTTP Content Server uses a permanent identifier, the LIPF present in the ADMF also provisions the IRI-POI in the HTTP Content Server.
To enable the interception of the target's message contents (e.g. when the warrant requires the interception of communication contents), the CC-POI in each RCS Server and the CC-TF present in the relevant RCS Servers are also provisioned with the intercept data.
If the authentication method used to authenticate at the HTTP Content Server uses a permanent identifier and the interception of the target's communication contents is required, the LIPF present in the ADMF also provisions the CC-POI in the HTTP Content Server.
The IRI-POI present in the relevant RCS Server detects RCS registration and deregistration; session establishment, modification, and deletion; and message related events, generates and delivers the related xIRI to the MDF2 over LI_X2. The MDF2 delivers the IRI messages to the LEMF over LI_HI2.
When the IRI-TF present in the RCS Server detects a URI for file transfer, the IRI-TF present in the RCS Server sends a trigger to the IRI-POI in the HTTP Content Server over the LI_T2 interface.
The IRI-POI present in the HTTP Content Server detects file uploads, downloads, or retrieval (i.e. by File Transfer Localisation Function, see clause 7.13.2.2.2), generates and delivers the related xIRI to the MDF2 over LI_X2. The MDF2 delivers the IRI messages to the LEMF over LI_HI2.
When interception of communication contents is required, the CC-POI present in the relevant RCS Server generates the xCC from RCS messages and delivers the xCC (that includes the correlation number and the target identity) to the MDF3. The MDF3 delivers the CC to the LEMF over LI_HI3.
When interception of communication contents is required, the CC-TF present in the RCS Servers sends a trigger to the CC-POI present in the HTTP Content Server over the LI_T3 interface.
The trigger sent from the IRI-TF to the IRI-POI or the CC-TF to the CC-POI includes the following information:
- File detection rules.
- Target identity.
- Correlation information.
- MDF3 address.
7.13.2.2 Deployment options p. 133
7.13.2.2.1 Implementations without a third party registration to the RCS Server p. 133
As a deployment option, the S-CSCF may not perform a third party registration with the RCS Server. In this case, in addition to the architecture information in clause 7.13.2.1, the IRI-POI present in the IMS Signalling Function detects RCS registration and deregistration, generates and delivers the related xIRI to the MDF2 over LI_X2.
7.13.2.2.2 Implementations that have a file transfer localisation function p. 133
As described in GSMA RCC.07, clause 4.1.15.3 [35], the terminating CSP may utilize a File Transfer Localisation Function which retrieves objects from the originating HTTP Content Server and makes the same available to the terminating user.
If the CSP implements a File Transfer Localisation Function, in addition to the architecture information in clause 7.13.2.1, the following requirements apply.
The LI architecture for the File Transfer Localisation Function is depicted in Figure 7.13.2.1-1.
When the IRI-TF present in the RCS Server detects a URI for an incoming file transfer, the IRI-TF present in the RCS Server sends a trigger to the IRI-POI in the File Transfer Localisation Function over the LI_T2 interface. When interception of communication contents is required, the CC-TF present in the RCS Servers sends a trigger to the CC-POI present in the File Transfer Localisation Function over the LI_T3 interface. The trigger sent from the TF to the POI includes the following information:
- File detection rules.
- Target identity.
- Correlation information.
- MDF2 (for xIRI) or MDF3 (for xCC) address.
7.13.3 Target identities p. 134
The LIPF present in the ADMF provisions the intercept information associated with the following target identities to the IRI-POI, IRI-TF, CC-POI and CC-TF present in the RCS Server:
- IMPU.
- IMPI.
- IMEI.
- IMSI.
- SUPI.
- GPSI.
- Email Address.
7.13.4 IRI events p. 134
7.13.4.1 General RCS IRI events p. 134
As described in clause 7.13.2, the term RCS Server in the present document refers to any server performing support, services or functions for RCS. In most deployments there will be more than one RCS Server, and the events listed below shall be intercepted in the server responsible for performing the functions described by the event.
The IRI-POI present in the RCS Servers shall generate xIRI when it detects the following specific events or information:
- Registration.
- Deregistration.
- Capability discovery.
- RCS message.
- RCS message report.
- Session establishment.
- Session modification.
- Session release.
- Group chat establishment.
- Group chat modification.
- Group chat release.
- Start of interception with already registered UE.
- Start of interception with already established session.
- Unsuccessful procedure.
- File upload.
- File download.
- Unsuccessful procedure.
7.13.4.2 RCS events for topologies without a third party registration to the RCS Server p. 136
The events specified in clause 7.13.4.1 apply with the following changes:
Rather than the IRI-POI present in the RCS Servers, the IRI-POI present in the IMS Signalling Function shall generate xIRI when it detects the following specific events or information:
- Registration.
- Deregistration.
7.13.4.3 RCS events for topologies utilising a file transfer localisation function p. 136
The events specified in clause 7.13.4.1 apply with the following changes:
In addition to the IRI-POI present in the HTTP Content Server (as described in clause 7.13.4.1), the IRI-POI present in the Localisation Function shall generate xIRI when it detects the following specific events or information:
- File transfer.
- File download.
- Unsuccessful procedure.