Content for TS 33.127 Word version: 19.1.0
0…
5…
5.4…
5.6…
5.7…
6…
6.2.2…
6.2.3…
6.2.5…
6.3…
6.3.3…
6.3.4…
6.4…
7…
7.3…
7.4…
7.4.7…
7.5…
7.6…
7.7…
7.8…
7.9…
7.10…
7.11…
7.12…
7.13…
7.14…
7.15…
7.16…
8…
A…
A.2…
A.3…
A.4…
B…
D…
E…
7 Service layer based interception
7.1 General
7.2 Central subscriber management
7.2.1 General
7.2.2 LI at UDM
7.2.2.1 Architecture
7.2.2.2 Target identities
7.2.2.3 Identity privacy
7.2.2.4 IRI events
7.2.2.5 Common IRI parameters
7.2.2.6 Specific IRI parameters
7.2.2.7 Network topologies
7.2.3 LI at HSS
7.2.3.1 Architecture
7.2.3.2 Target identities
7.2.3.3 IRI events
7.2.3.4 Common IRI parameters
7.2.3.5 Specific IRI parameters
7.2.3.6 Network topologies
7.2.4 LI at the IMS supporting HSS
...
...
7 Service layer based interception p. 75
7.1 General p. 75
Clause 7 provides details for the configuration of the high-level LI architecture for service layer based interception and for network function which are not specific to a single access type or network service (e.g. subscription management functions). It defines aspects of the LI configuration specific to each service under consideration, while aspects concerning network over which the service is delivered (e.g. 5G) are considered in clause 6.
If one of the services listed below is implemented in a non-standard way, see Annex F.3.
7.2 Central subscriber management p. 75
7.2.1 General p. 75
Clause 7.2 provides LI architecture and requirements for the CSP 3GPP subscriber database LI reporting. Central subscriber databases are common for all CSP network services, including both the network layer and the service layer. Clause 7.2 provides requirements for both user session related interception events and requirements for reporting of changes to the subscriber information held within the 3GPP subscriber databases, which may or may not be directly related to service usage.
7.2.2 LI at UDM p. 76
7.2.2.1 Architecture p. 76
The UDM provides the unified data management for UE. The UDM shall have LI capabilities to generate the target UE's serving system (e.g. VPLMN Id or AMF Id related xIRI). Extending the generic LI architecture presented in clause 5, Figure 7.2.2.1-1 below gives a reference point representation the LI architecture with UDM as a CP NF providing the IRI-POI functions.
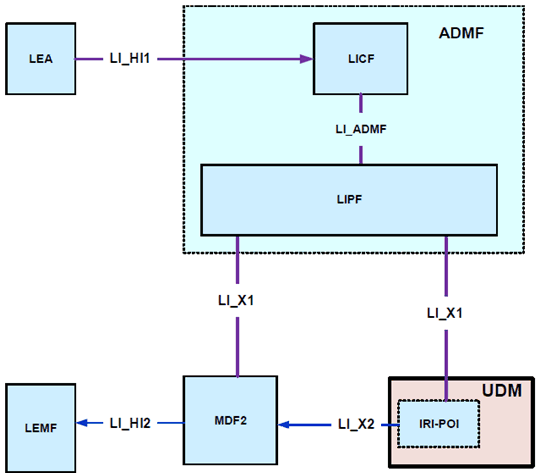
The LICF present in the ADMF receives the warrant from an LEA, derives the intercept information from the warrant and provides it to the LIPF.
The LIPF present in the ADMF provisions IRI-POI (over LI_X1) present in the UDM and MDF2. The LIPF may interact with the SIRF (over LI_SI) present in the NRF to discover the UDM in the network.
The IRI-POI present in the UDM detects the target UE's service area registration and subscription related functions, generates and delivers the xIRI to the MDF2 over LI_X2. The MDF2 generates and delivers the IRI messages based on received xIRI to the LEMF over LI_HI2.
7.2.2.2 Target identities p. 77
The LIPF present in the ADMF provisions the intercept information associated with the following target identities to the IRI-POI present in the UDM:
- SUPI.
- PEI.
- GPSI.
- IMPU/IMPI.
7.2.2.3 Identity privacy p. 77
TS 33.501 defines the ability to prevent the SUPI being exposed over the 5G RAN through the use of SUCI. Where SUPI privacy is implemented by both the UDM and UE, the SUPI is not sent in the clear over the RAN. Therefore, the UDM shall ensure that the SUPI is provided to the serving AMF in both initial registration and re-registration procedures as defined in TS 33.501.
7.2.2.4 IRI events p. 77
The IRI-POI present in the UDM shall generate xIRI, when the UDM detects the following specific events or information:
- Serving system.
- Subscriber record change.
- Cancel location.
- Location information request.
- Location information result.
- UE information response.
- UE authentication response.
- Start of interception with target already registered at the UDM.
- ProSe target identifier deconcealment.
- ProSe target authentication.
7.2.2.5 Common IRI parameters p. 78
The list of xIRI parameters is specified in TS 33.128. All xIRIs shall include the following information:
- Target identity.
- Time stamp.
7.2.2.6 Specific IRI parameters p. 78
The parameters in each xIRI are defined in TS 33.128.
7.2.2.7 Network topologies p. 78
The UDM shall provide the IRI-POI functions in the following network topology cases:
- Non-roaming case.
- Roaming case, in HPLMN.
7.2.3 LI at HSS p. 78
7.2.3.1 Architecture p. 78
The HSS contains subscription-related information for users served by the CSP. The HSS provides the support functions for mobility management, session setup, user authentication and access authorization.
The HSS shall have LI capabilities to generate the xIRIs as described in clause 7.2.3.3. The present document specifies two options for HSS LI capabilities:
IMS ), TS 33.128 shall be used for stage 3 LI reporting. For details of stage 2 requirements, see clause 7.2.4 of the present document.
Extending the generic LI architecture presented in clause 5, Figure 7.2.3.1-1 below gives a reference point representation the LI architecture with HSS as a CP NF providing the IRI-POI functions.
- Use TS 33.107 and TS 33.108 natively as defined in those documents
- Use the capabilities specified below in the present document for stage 2 and in TS 33.128 for stage 3
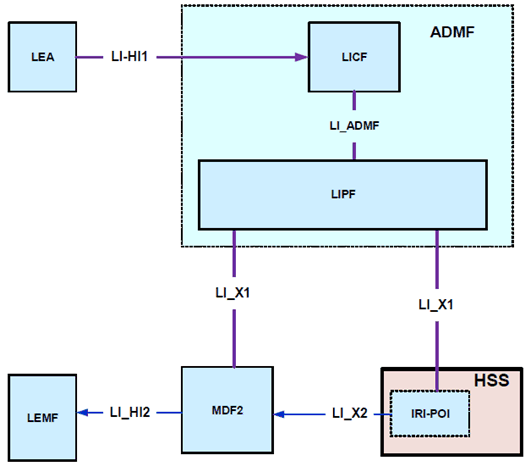
The LICF present in the ADMF receives the warrant from an LEA, derives the intercept information from the warrant and provides it to the LIPF.
The LIPF present in the ADMF provisions IRI-POI (over LI_X1) present in the HSS and MDF2.
The IRI-POI present in the HSS detects the target UE's service area registration and subscription related functions, generates and delivers the xIRI to the MDF2 over LI_X2. The MDF2 generates and delivers the IRI messages based on received xIRI to the LEMF over LI_HI2.
The HSS shall provide the IRI-POI functions independent of the services on which the interception is active.
When multiple intercepts are active, IRI-POI functions in the HSS may send one xIRI which can then be distributed to the LEMFs associated with those multiple intercepts from the MDF2.
7.2.3.2 Target identities p. 79
The LIPF present in the ADMF provisions the intercept information associated with the following target identities to the IRI-POI present in the HSS:
- IMSI.
- IMEI.
- MSISDN.
- IMPU/IMPI.
7.2.3.3 IRI events p. 80
The IRI-POI present in the HSS shall generate xIRI, when it detects the applicable events specified in TS 33.107.
The IRI-POI present in the HSS shall also generate a start of intercept with already registered target xIRI when the IRI-POI present in the HSS detects that intercept has been activated for a UE that has existing context in the HSS. Format of this xIRI is described in clause 7.2.3.3.3 of TS 33.128.
The IRI-POI present in the EPC supporting HSS shall generate a subscriber record change record when the IRI-POI in the HSS observes an update to the IMEI context for the target at the HSS.
If HSS-UDM interworking is supported, the IRI-POI present in the HSS shall generate a serving system xIRI as defined in clause 7.2.3.3.2 of TS 33.128.
A serving system xIRI is generated when the IRI-POI present in the HSS detects that the HSS has received a roaming status update from the UDM as part of a UE context update.
7.2.3.4 Common IRI parameters p. 80
The list of xIRI parameters is specified in TS 33.128. All xIRIs shall include the following information:
- Target identity.
- Time stamp.
7.2.3.5 Specific IRI parameters p. 80
The parameters in each xIRI are defined in TS 33.128.
7.2.3.6 Network topologies p. 80
The HSS shall provide the IRI-POI functions in the following network topology cases:
- Non-roaming case.
- Roaming case, in HPLMN.
7.2.4 LI at the IMS supporting HSS p. 80
7.2.4.1 Architecture p. 80
The present document defines an IMS-HSS as an HSS that supports service based interfaces for connection to the 5GC. The IMS-HSS contains subscription-related information IMS users served by the CSP. The IMS-HSS provides the support functions for mobility management, session setup, user authentication and access authorization to a 5G network in support of enhanced IMS services (e.g. VoNR).
The IMS-HSS shall have LI capabilities to generate the xIRIs as described in clause 7.2.4.3.
When the deployed architecture supports service based interfaces between the HSS and IMS (e.g. Nhss_IMS ), TS 33.128 shall be used for stage 3 LI reporting.
The presented in Figure 7.2.3.1-1 gives a reference point representation the LI architecture with HSS (or IMS-HSS) presented as an NF providing the IRI-POI functions.
7.2.4.2 Target identities p. 81
The LIPF present in the ADMF provisions the intercept information associated with the following target identities to the IRI-POI present in the IMS-HSS:
- IMSI.
- IMEI.
- MSISDN.
- IMPU/IMPI.
7.2.4.3 IRI events p. 81
The IRI-POI present in the IMS-HSS shall generate xIRI, when it detects the following specific events or information:
- Start of interception with registered target.
- Serving system.
- Subscriber record change.
7.2.4.4 Common IRI parameters p. 81
The list of xIRI parameters is specified in TS 33.128. All xIRIs shall include the following information:
- Target identity.
- Time stamp.
7.2.4.5 Specific IRI parameters p. 81
The parameters in each xIRI are defined in TS 33.128.
7.2.4.6 Network topologies p. 81
The IMS-HSS shall provide the IRI-POI functions in the following network topology cases:
- Non-roaming case.
- Roaming case, in HPLMN.