Content for TS 33.180 Word version: 18.1.0
1…
4…
4.3.4
4.3.5
5…
5.1.3
5.1.4…
5.2…
5.2.3
5.2.4
5.2.5
5.2.6…
5.3…
5.4…
6…
7…
7.3…
8…
9…
9.4…
10…
A…
B…
C…
D…
E…
F…
J…
L…
5.2.4 Key distribution with associated parameters p. 43
The key distribution mechanisms described in Clause 5.2.2 and clause 5.2.3 may be extended to include data associated with the key in the MIKEY I_MESSAGE. This data is stored within a format known as 'associated parameters' and defined in Annex E.6.
The associated parameters are encrypted using K, the key distributed within the MIKEY I_MESSAGE. The security mechanism is summarised in Figure 5.2.4-1.
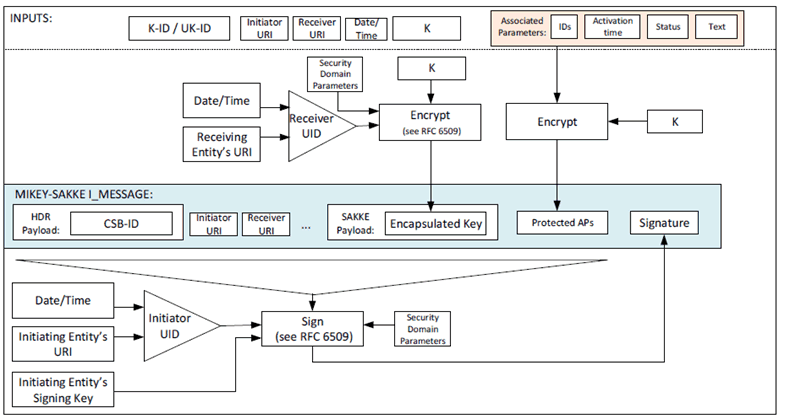
Figure 5.2.4-1: Common key distribution mechanism with associated parameters
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
At the receiving MCX entity, the initiating entity's URI is extracted from the initiator field (IDRi) of the message. Along with the time, this is used to check the signature on the payload. If valid, the receiving entity extracts and decrypts the encapsulated key, K, using the (KMS-provisioned) receiving entity's decryption key.
The receiving MCX entity also extracts 'associated parameters' payload from the I_MESSAGE. The receiving entity uses the decrypted key, K, to decrypt these associated parameters. The receiving entity stores these parameters with the distributed key, K. If the Status field within the 'associated parameters' payload indicates the key has been revoked, the distributed key, K, and the K-ID shall not be used. If the decryption process for the encapsulated associated parameters fails, the key is rejected.
The security mechanism is summarised in Figure 5.2.4-2.
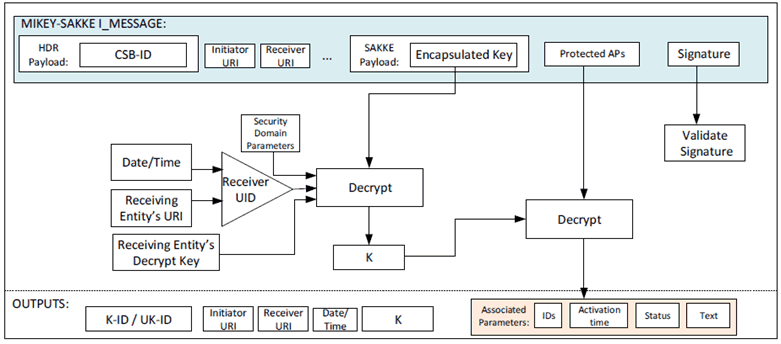
Figure 5.2.4-2: Common key extraction mechanism with associated parameters
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)