Content for TS 33.180 Word version: 18.1.0
1…
4…
4.3.4
4.3.5
5…
5.1.3
5.1.4…
5.2…
5.2.3
5.2.4
5.2.5
5.2.6…
5.3…
5.4…
6…
7…
7.3…
8…
9…
9.4…
10…
A…
B…
C…
D…
E…
F…
J…
L…
4.3.5 Media security p. 23
4.3.5.1 General p. 23
Media security establishes an end-to-end security context between MC users to support group communications and private communications for the MCPTT, MCVideo or MCData services. The intention is for media to be able to be encrypted end-to-end between MC clients, irrespective of whether the media is routed unicast via the media distribution server, multicast via the media distribution server, or transmitted over a direct or IOPS connection.
Key distribution for groups is performed by the Group Management Server. Key distribution for private calls is performed by the initiating MC client. Once a security context is established, the media is protected using the distributed key material. Aditionally, when MC UEs are off-network, the security context that is used to protect media security is also used to protect control signalling (e.g. RTCP).
4.3.5.2 Media security for group communications. p. 23
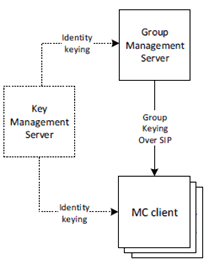
Media security for groups is secured by establishing a shared group security context between group members. Key distribution for the group security context is performed by a Group Management Server. The Group Management Server creates and sends group keys and group security parameters over SIP as part of group management.
Group keys and security parameters are encrypted by the Group Management Server to the identity of the individual MC users that are members of the group. MC users and MCX servers require identity keying by a KMS prior to performing group management.
Figure 4.3.5.2-1 provides an overview of the group keying process. Details of the process may be found in clause 5.7.
Once a group key has been shared with MC users, keys are derived from that group key to protect media (and control signalling when the UE is off-network).
For MCPTT and MCVideo (specifically RTP), key derivation is based on the MCPTT or MCVideo user's identity, hence every member of the group encrypts media using a different key. Media is encrypted using the SRTP protocol in this case. For MCData, the user-specific key derivation is not required. Media is encrypted within a MCData data payload in this case.
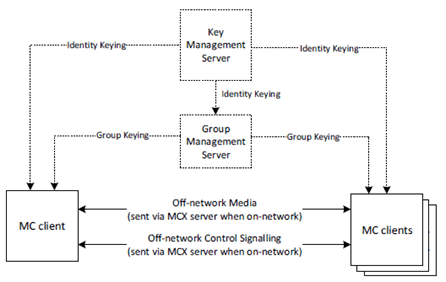
When the MC UE has a network connection the encrypted media is routed to other MC clients via the media distribution function in the MCX Server. Media from an MC client is distributed to group members by the MCX Server over either unicast or multicast. When the MC UE is off-network, the encrypted media is routed directly to MC clients on other MC UEs. The security procedure for protecting media is the same in either case. Details of media encryption are provided in clause 7 for MCPTT and MCVideo, and clause 8 for MCData.
Unlike media, control signalling (such as floor control or transmission control) is protected differently when the UE has a network connection and when it is off-network. When the UE has a network connection, control signalling traffic is encrypted to the identity of the MC Domain. When it is off-network, control signalling is encrypted directly to UEs using a key derived from the root key for the group or private communication. Details of control signalling encryption is provided in clause 9.4.
Figure 4.3.5.2-2 provides an overview of how media is protected for group communications.
4.3.5.3 Media security for private calls p. 24
As part of setting up a private call, the call initiator provides the session key to the terminating client. The key is encrypted to the MC user that is currently registered on the terminating client. As a result, MC users require identity keying by a KMS prior to performing private communications.
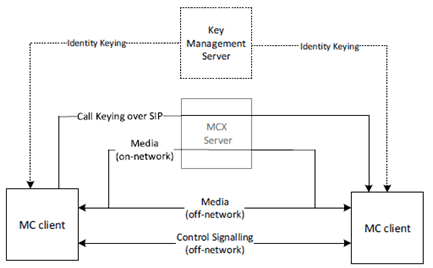
Figure 4.3.5.3-1 provides an overview of media protection for private calls. For clarity, MC network entities do not have access to the private call key material and hence are not able to decrypt the media for the private call communication (unless the monitoring function is specifically authorised for either user).
Details of private call key distribution are provided in clause 5.6, specific MCPTT and MCVideo procedures are described in clause 7 and specific MCData procedures are in clause 8.
Once private call key distribution has been completed, control signalling and application signalling are used to setup and control the media transport of a private communication. Media will be routed via the media distribution function in the MCX Server when the UE is online, and directly when the UE is off-network. Details of media protection are found in clause 7 and clause 8, control signalling protection is found in clause 9.4 and application signalling protection is found in clause 9.3.
The media security context shall also be used to protect control signalling (e.g. floor control) when the MC UE is off-network.