Content for TS 33.180 Word version: 18.1.0
1…
4…
4.3.4
4.3.5
5…
5.1.3
5.1.4…
5.2…
5.2.3
5.2.4
5.2.5
5.2.6…
5.3…
5.4…
6…
7…
7.3…
8…
9…
9.4…
10…
A…
B…
C…
D…
E…
F…
J…
L…
4 Overview of Mission Critical Security
4.1 General
4.2 Signalling plane security architecture
4.3 MC system security architecture
4.3.1 General
4.3.2 User authentication and authorisation
4.3.3 Identity keying of users and services
...
...
4 Overview of Mission Critical Security p. 17
4.1 General p. 17
The mission critical security architecture defined in this document is designed to meet the security requirements defined in Annex A. The security architecture provides signalling and application plane security mechanisms to protect metadata and communications used as part of the MC service. The following signalling plane security mechanisms are used by the MC service:
- Protection of the signalling plane used by the MC Service, defined in clause 6.1 and 6.2.
- Protection of inter/intra domain interfaces, defined in clause 6.3.
- Authentication and authorisation of users to the MC Service, defined in clause 5.1.
- Protection of sensitive application signalling within the MC Service, defined in clause 9.
- Security of RTCP (e.g. floor control, transmission control) within the MC Service, defined in clause 9.
- Security of data signalling within the MCData Service, defined in clause 8.
- End-to-end security of user media within the MC Service. Defined in clause 7 for MCPTT and MCVideo services and defined in clause 8 for the MCData service.
4.2 Signalling plane security architecture p. 17
Within a MC system, signalling plane security protects the interfaces used by the MC application. Figure 4.2-1 provides an overview of these interfaces.
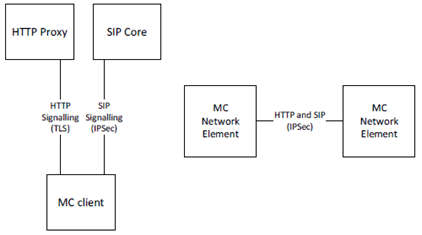
Signalling from the MC client is passed over both HTTP and SIP. The signalling plane security mechanisms for client to server interfaces and between network elements are defined in clause 6.
4.3 MC system security architecture p. 18
4.3.1 General p. 18
The MC system security architecture provides protection both between MC clients, between the MC client and the MC domain, and also between MC domains. MC system security on the client is bound to the MC user associated with the client and not to the MC UE. Consequently, user authentication and authorisation to the MC domain is required prior to access to the majority of MC services.
Application plane signalling security allows protection of MC-specific signalling from all entities outside of the MC system (potentially including the SIP core). Application plane signalling security is applied from the MC client to the client's primary MC domain. It may also be applied between MC domains.
Media security allows protection of MC media within the MC system. It is applied end-to-end between MC clients or in some cases from the MC client to the MCX server (e.g. One-to-server video push or one-from-server video pull). Under normal operation however, MC network entities such as the MCX Servers are typically unable to decrypt the media.
Additionally, signalling plane protection is applied to all HTTP and SIP connections into the MC domain. While signalling plane protection and signalling plane entities are not shown in this subclause, including the SIP core and HTTP proxy, it is assumed that signalling plane protection mechanisms are in use.
4.3.2 User authentication and authorisation p. 18
Prior to connecting to the MC domain, the MCX user application requires a 'token' authorising its access to MC services. To obtain authorisation token(s), the MCX user application authenticates the MC user to an Identity Management Server which provides the authorisation token.
The authorisation token is provided to MCX network entities, such as the MCX Server, over an MCX signalling interface (either a HTTP interface or SIP interface). The MCX network entity will provide access to MCX services based upon the token provided.
The architecture for user authentication and authorisation is shown in Figure 4.3.2-1.
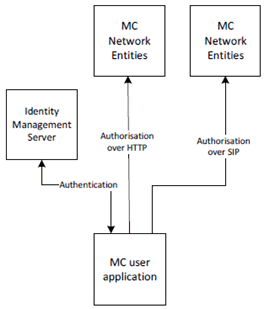
While the HTTP proxy and SIP core is not shown in Figure 4.3.2-1, authorisation occurs over HTTP or SIP and hence uses signalling plane protection to encrypt authorisation requests carried over HTTP to a HTTP proxy and authorisation requests carried in SIP messages through the SIP core to the MCX domain.
The mechanism to perform user authentication and authorisation is defined in clause 5.1.
4.3.3 Identity keying of users and services p. 19
Once a MC client has obtained user authorisation to access the MCX domain, the client may obtain key material associated with the user's identity using the authorisation token. Identity keys are required to support key distribution for application signalling, floor control, transmission control and media. Identity key material is obtained via an HTTP request to a Key Management Server as shown in Figure 4.3.3-1.
Identitiy keying is repeated periodically (e.g. monthly). This ensures that user identities are regularly verified and that users that are no longer part of the MCX domain are removed from the system.
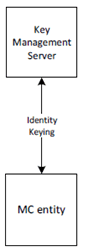
While not shown in Figure 4.3.3-1, the UE connection to the KMS is over HTTP and hence is secured using TLS directly between the MC client and KMS or between the MC client and the HTTP proxy or directly to the KMS. When the HTTP proxy is in the path between the MC client and the KMS, key material is wrapped using a transport key (TrK) distributed out-of-band (reference clause 5.3.2). The TrK or a shared Integrity key (InK) may be used to sign the key material.
A number of MC network entities also require identity key material including the MCX Server and Group Management Server. This key material is obtained via the same HTTP interface.
The mechanism to perform identity keying is defined in clause 5.3.