Content for TS 33.163 Word version: 18.0.0
4.6 Key Management
4.6.1 Key Agreement and Refresh
4.6.1.1 Key setup messaging between HSE and UE
4.6.1.2 Usage of Keys
4.6.1.3 Key Setup for BEST session end point modification
4.6.1.4 BEST key handling
4.6.2 BEST key hierarchy
4.6.2.1 Introduction
4.6.2.2 BEST key hierarchy for separate BEST domain
...
...
4.6 Key Management p. 16
4.6.1 Key Agreement and Refresh p. 16
4.6.1.1 Key setup messaging between HSE and UE p. 16
New keys are agreed either at the start of a BEST session or as required due to key aging or counter thresholds being met. Key agreement can be based on the 3GPP AKA mechanism detailed in TS 33.102, TS 33.401, or TS 33.501, respectively, or based on one of the following external key agreement methods: GBA TS 33.220, 5G GBA TS 33.220, Annex N, AKMA TS 33.535, or proprietary key agreement. For 3GPP AKA based key agreement, the AKA challenge is then transported between the HSE and the UE as part of the BEST service detailed in clause 4.3.2. The key hierarchy is shown in clause 4.6.2.2.
The EMDSP protocol has 7 Key IDs for each session ID. Each Key ID has a separate keyset consisting of an integrity Key (KE2Mint), an encryption key (KE2Menc), optionally an Intermediate Key (KIntermediate) and optionally an EAS PSK (KEAS_PSK). The Key IDs shall be set during the derivations of the keys as specified in clause 5.1.
The Intermediate Key (KIntermediate) is used together with a separate enterprise server identifier (EAS Id) to calculate the EAS PSK (KEAS_PSK). There can be many KEAS_PSK derived from one KIntermediate.
The EAS PSK (KEAS_PSK) is used together with the Enterprise Key to calculate KE2Eint and KE2Eenc when BEST User plane security services are used in UE-to-EAS mode.
Figure 4.6.1.1-1 shows the generic key agreement process for EPS networks:
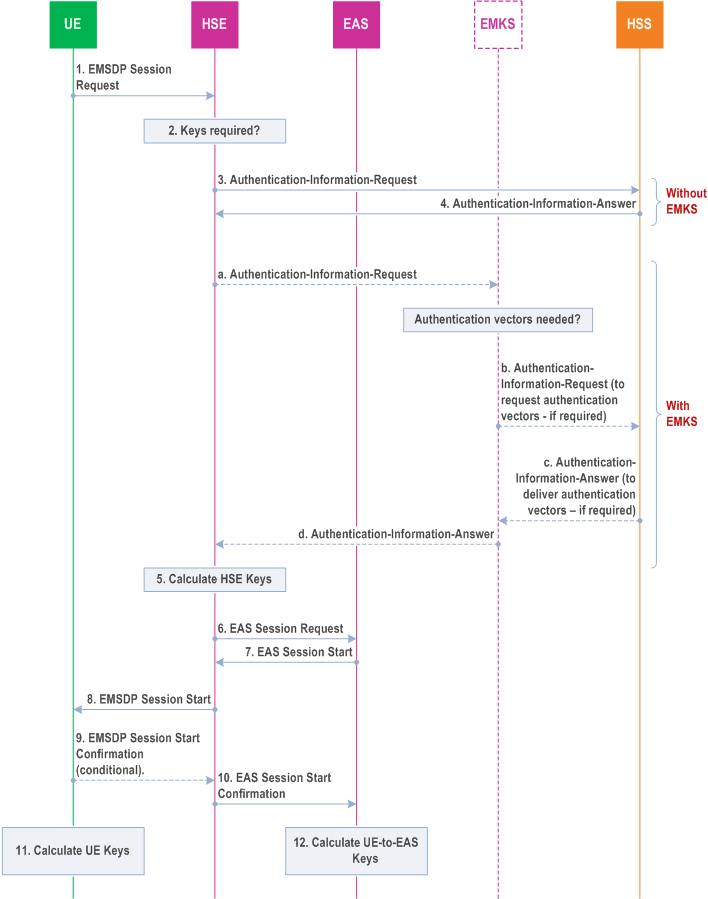
The Key agreement steps are:
Step 1.
Figure 4.6.1.1-2 shows the generic key agreement process for 5GS networks:
EMSDP Session Request (UE ID, BEST capabilities, Enterprise information serving network (cond)). The UE shall send the EMSDP Session Request (UE ID, BEST capabilities, Enterprise information, serving network (cond)) to set up a new BEST session. The BEST capabilities shall indicate that EPS key agreement is supported.
Step 2.
Keys required? - the HSE shall check to see if there are valid keys with valid counter values available in the HSE for that UE then the following is checked:
Step 3.
- If the HSE has a valid set of keys for the indicated session and the UE ID is valid for that session then the HSE may start the BEST session without re-negotiating the keys (step 8).
- If the UE ID is valid for that HSE and the HSE does not have a valid set of keys for the indicated session or the HSE wishes to update the keys, then it shall first renegotiate the keys (steps 2 to 7) and then start the BEST session (step 8).
- If the UE ID is not valid for that session ID or the UE does not support the level of service required by the HSE or the enterprise information is not valid for the HSE, then the HSE may reject the command.
Authentication-Information-Request over S6a interface - The HSE shall use the S6a interface to the HSS to request one or more authentication vectors using the UE IMSI. For UEs the request shall indicate that EPS authentication vectors are requested. For legacy UEs supporting BEST, the request shall indicate that UMTS authentication vectors are requested.
Step 4.
Authentication-Information-Answer over S6a interface - The HSS uses the S6a interface to the HSE to return the requested authentication vectors.
Step 5.
- Authentication-Information-Request over the S6a interface between HSE and EMKS - Where an EMKS is used, the HSE shall use the S6a interface to the EMKS to request an authentication vector using the UE IMSI.
- Authentication-Information-Request over the S6a interface between EMKS and HSE - The EMKS shall use the S6a interface to the HSS to request one or more authentication vectors using the UE IMSI.
- Authentication-Information-Answer over the S6a interface between EMKS and HSE - The HSS shall use the S6a interface to the EMKS to return the requested authentication vectors. These vectors may be stored on the EMKS for later use.
- Authentication-Information-Answer over the S6a interface between HSE and EMKS - The EMKS uses the S6a interface to the HSE to return the requested authentication vector.
Calculate UE-to-HSE Keys - See key derivation details in clause 5.
Step 6.
The HSE may optionally send "EAS Session Request" to the EAS- In case BEST UP service is used in UE-to-EAS mode, the HSE shall use the HSE interface to the EAS to inform the EAS of the new UE-to-EAS session request and shall forward the EAS PSK (KEAS_PSK) to the EAS. In case the BEST key agreement service is used, the HSE shall forward to the EAS, the EAS PSK (KEAS_PSK) and the key identifier for the Intermediate Pre Shared Key (KIntermediate).
Step 7.
The Enterprise Server sends a "EAS Session Start" to the HSE - The Enterprise Server shall respond by sending the "UE-to-EAS Session Start" message. In case BEST UP service is used, this message may contain an EAS container that includes an identifier for the Enterprise Key.
Step 8.
EMSDP Session Start message - The HSE shall send a EMSDP Session Start (Key Agreement, Session Parameters, Request Validation, HSE ID(opt) , EAS container (opt)). The Session Parameters shall contain RAND and AUTN from the received authentication vectors. As described in clause 6.1.2 of TS 33.401, the "separation bit" in the AMF field of AUTN shall be set to 0 if UMTS authentication vectors have been received, and the "separation bit" in the AMF field of AUTN shall be set to 1 if EPS authentication vectors have been received. The Session Parameters shall indicate the selected key agreement (i.e. EPS key agreement).
Step 9.
EMSDP Session Start Confirmation - UE optionally, if requested in the Session Start Confirmation, responds with an EMSDP Session Start Confirmation message.
Step 10.
EAS Session Start Confirmation - The HSE may optionally send EAS Session Start Confirmation.
Step 11.
Calculate UE Keys - See key derivation details in clause 5.
Step 12.
Calculate UE-to-EAS Keys - In case of the UE-to-EAS BEST UP service, the Enterprise server generates UE-to-EAS keys as per the key derivation details in clause 5.
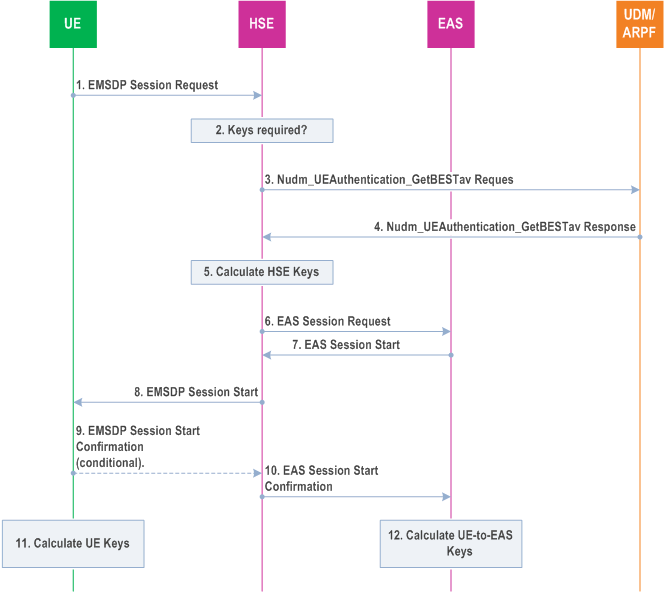
The Key agreement steps are:
Step 1.
EMSDP Session Request (UE ID, BEST capabilities, Enterprise information, serving network). The UE shall send the EMSDP Session Request (UE ID, BEST capabilities, Enterprise information, serving network) to set up a new BEST session. The BEST capabilities shall indicate that 5G key agreement is supported.
Step 2.
Keys required? - the HSE shall check to see if there are valid keys with valid counter values available in the HSE for that UE then the following is checked:
Step 3.
- If the EMSDP Session Request is sent with a valid Session ID (i.e., not 0) and there is a valid key set for that session, then the HSE may start the BEST session without re-negotiating the keys (step 8). In this case the received UE ID may be ignored.
- If the EMSDP Session Request is sent without a valid Session ID or using a single byte Session ID set to 0 or the HSE wishes to update the keys, then it shall first renegotiate the keys (steps 2 to 7) and then start the BEST session (step 8).
- If the UE does not support the level of service required by the HSE or the enterprise information is not valid for the HSE, then the HSE may reject the command.
Nudm_UEAuthentication_GetBESTav Request over SBA interface - The HSE shall use the SBA interface to the UDM/ARPF to request an authentication vector using the UE SUCI. The service operation Nudm_UEAuthentication_GetBESTav Request has the same inputs as the service operation Nudm_UEAuthentication_Get Request.
Step 4.
Nudm_UEAuthentication_GetBESTav Response over SBA interface - The UDM/ARPF uses the SBA interface to the HSE to return a BEST-adapted 5G HE authentication vector (if 5G AKA is the selected authentication method) or a transformed authentication vector (if EAP-AKA' is the selected authentication method).The service operation Nudm_UEAuthentication_GetBESTav Response has the same outputs as the service operation Nudm_UEAuthentication_Get Response, except that in the BEST-adapted 5G HE authentication vector the parameter KAUSF is replaced by KHSE (see clause 5.1.0a).
Step 5.
Calculate UE-to-HSE Keys - See key derivation details in clause 5.
Step 6.
The HSE may optionally send "EAS Session Request" to the EAS- In case BEST UP service is used in UE-to-EAS mode, the HSE shall use the HSE interface to the EAS to inform the EAS of the new UE-to-EAS session request and shall forward the EAS PSK (KEAS_PSK) to the EAS. In case the BEST key agreement service is used, the HSE shall forward to the EAS, the EAS PSK (KEAS_PSK) and the key identifier for the Intermediate Pre Shared Key (KIntermediate).
Step 7.
The Enterprise Server sends a "EAS Session Start" to the HSE - The Enterprise Server shall respond by sending the "UE-to-EAS Session Start" message. In case BEST UP service is used, this message may contain an EAS container that includes an identifier for the Enterprise Key.
Step 8.
EMSDP Session Start message - The HSE shall send a EMSDP Session Start (Key Agreement, Session Parameters, Request Validation, HSE ID (opt), EAS container (opt)). The Session Parameters shall contain RAND and AUTN from the received authentication vectors. The "separation bit" in the AMF field of AUTN shall be set to 1. The Session Parameters shall indicate that 5G key agreement has been selected.
Step 9.
EMSDP Session Start Confirmation - UE optionally, if requested in the Session Start Confirmation, responds with an EMSDP Session Start Confirmation message.
Step 10.
EAS Session Start Confirmation - The HSE may optionally send EAS Session Start Confirmation.
Step 11.
Calculate UE Keys - See key derivation details in clause 5.
Step 12.
Calculate UE-to-EAS Keys - In case of the UE-to-EAS BEST UP service, the Enterprise server generates UE-to-EAS keys as per the key derivation details in clause 5.
4.6.1.2 Usage of Keys p. 20
For UE-to-HSE BEST UP sessions, the following keys shall be used:
- The KE2Menc shall be used by the UE and the HSE for the encryption of the user plane and the control plane, according to the agreed encryption algorithm.
- The KE2Mint shall be used by the UE and the HSE for the integrity protection of the user plane and the control plane according to the agreed integrity protection algorithm.
- The KE2Menc shall be used by the UE and the HSE for the encryption of the control plane, according to the agreed encryption algorithm.
- The KE2Mint shall be used by the UE and the HSE for the integrity protection of the control plane according to the agreed integrity protection algorithm.
- The KE2Eenc shall be used by the UE and the EAS for the encryption of the user plane, according to the agreed encryption algorithm.
- The KE2Eint shall be used by the UE and the EAS for the integrity protection of the user plane according to the agreed integrity protection algorithm.
- The EAS PSK (KEAS_PSK) shall be used by the EAS and UE for protection of the user plane between the EAS and UE. The protocol to be used between the UE and EAS is out of scope of this specification. Optionally, further keys may be derived from the EAS PSK.
- The KE2Menc shall be used by the UE and the HSE for the encryption of the control plane, according to the agreed encryption algorithm.
- The KE2Mint shall be used by the UE and the HSE for the integrity protection of the control plane according to the agreed integrity protection algorithm.
4.6.1.3 Key Setup for BEST session end point modification p. 21
The modification of a BEST UE-to-EAS UP session to a BEST UE-to-HSE UP session does not require any new calculations of keys.
The modification of a BEST UE-to-HSE UP session to a BEST UE-to-EAS UP session requires new keys to be calculated when no UE-to-EAS keys are available in the EAS. Before sending the EMSDP Modification command the HSE does the following:
- Checks with the EAS whether it has UE-to-EAS keys in storage
- If not, obtains a EAS container that may contain a key identifier for the Enterprise Key from the EAS and forwards this to the UE in the EMSDP Modification command.
4.6.1.4 BEST key handling p. 21
The aging of keys and any counter window used are out of scope of this specification.
4.6.2 BEST key hierarchy p. 21
4.6.2.1 Introduction p. 21
This clause describes the key hierarchy for BEST for both the BEST user plane services and the key agreement service:
4.6.2.2 BEST key hierarchy for separate BEST domain p. 21
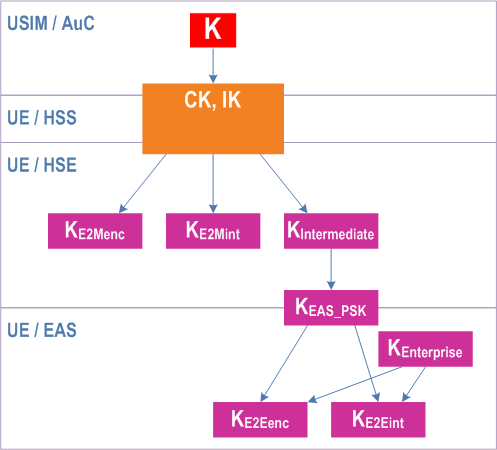
For EPS networks the BEST key hierarchy is as depicted in Figure 4.6.2.2-1.
For EPS networks the BEST key hierarchy is as depicted in Figure 4.6.2.2-2.
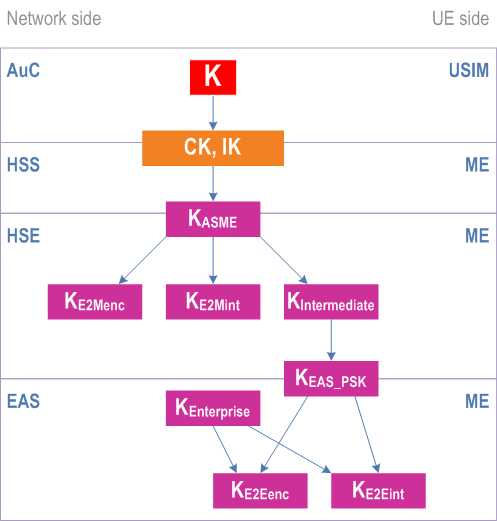
For 5GS networks the BEST key hierarchy is as depicted in Figure 4.6.2.2-3.
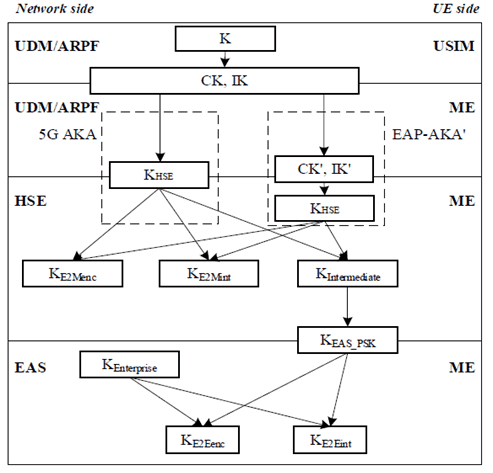
The derivation of the key KHSE is described in clause 5.1.0a.
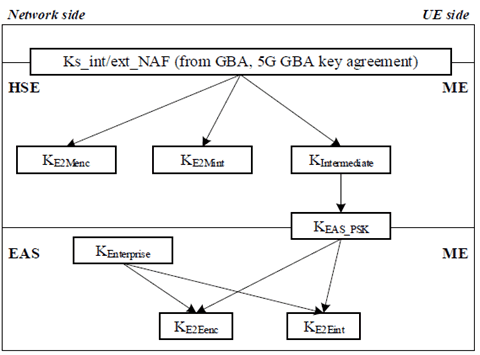
For GBA and 5G GBA based key agreement, the BEST key hierarchy is as depicted in Figure 4.6.2.2-4.
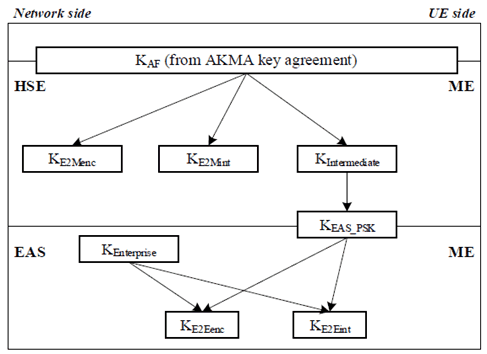
For AKMA based key agreement, the BEST key hierarchy is as depicted in Figure 4.6.2.2-5.
For proprietary key agreement, the BEST key hierarchy is as depicted in Figure 4.6.2.2-6.
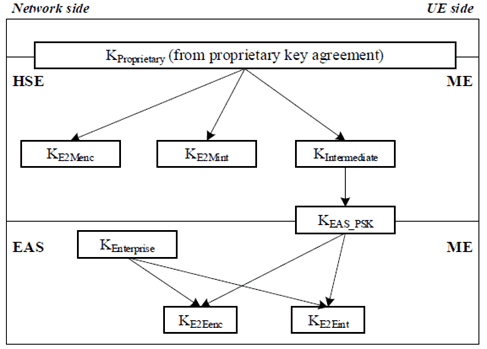
The KIntermediate, KEAS_PSK and all of the keys derived from them are generated when indicated to do so in the BEST CP messaging.