Content for TS 33.163 Word version: 18.0.0
A Structure of APN names for BEST
B HSE to EAS interface based on Restful HTTP
B.1 Introduction
B.2 Restful HTTP interface
$ Change history
A Structure of APN names for BEST p. 50
Due to regulatory requirements, operators may have to disable the best service for UEs roaming in their network. A simple, but effective method relies on the MME capability to filter specific APNs. For that reason, a BEST APN structure is proposed in this section. Operators may agree on a different method in bilateral requirements.
APNs that are used for the BEST service may reside in a specific subdomain of the operator. It is proposed to use the subdomain 'best' for this specific service.
B HSE to EAS interface based on Restful HTTP p. 50
B.1 Introduction p. 50
This annex contains example of a RESTful HTTP interface between the HSE and the EAS.
B.2 Restful HTTP interface p. 51
B.2.1 Overview p. 51
It is described as follows:
- TCP provides communication service at the transport layer
- TLS provides security to the communication
- HTTP based transport of XML data
- XML documents used to embed specific data structures, such as keys etc.
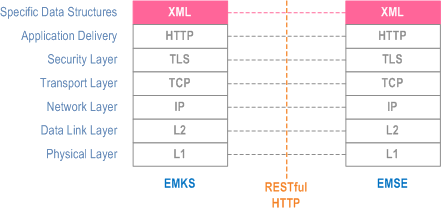
The HSE and the EAS act as both HTTP client and server. The underlying TCP connection permits bidirectional communication between the EAS and the HSE.
RESTful HTTP is used at the application delivery layer. The content type of the RESTful HTTP is XML.
The unsecured HTTP protocol shall be combined with TLS, as HTTPS, to provide confidentiality and integrity protection. Mutual authentication shall be enabled in TLS for authenticating and allowing only an authorized third party EAS to access the HSE. The profile for TLS implementation and usage shall follow the provisions given in TS 33.310, Annex E.
B.2.2 Procedures over the RESTful HTTP reference point p. 51
B.2.2.1 Overview of the procedures p. 51
Following procedures are supported over the RESTful HTTP reference point:
- Initial registration by the EAS
- Obtaining UE specific pre-shared key from the HSE
- Obtaining UE specific pre-shared key during BEST Session Setup
- Deregistration by EAS
B.2.2.2 Initial registration by EAS p. 52
The EAS registers with the HSE by sending an HTTP POST "EAS Session Register" message to the HSE including its identifier (EAS_Id). The HSE establishes a session context for this EAS and returns session id in HTTP 201 CREATED.
B.2.2.3 Obtaining UE specific pre-shared key from the EAS p. 52
The EAS obtains UE specific pre-shared key (KInt_EAS_PSK) from the HSE by sending an EAS Session Request message including an identity of the UE and the key identifier received from the UE. The HSE derives EAS specific pre-shared key and provides it in the EAS Session Start message.
B.2.2.4 Obtaining UE specific pre-shared key during BEST Session Setup p. 52
During BEST Session setup, the HSE forwards the EAS specific pre-shared key (KInt_EAS_PSK) in the EAS Session Request message. The EAS responds with a EAS Session Start message.
B.2.2.5 Deregistration by EAS p. 52
When the session needs to be terminated, EAS may send an HTTP DELETE message including the session ID to the HSE.