Content for TS 24.502 Word version: 19.0.0
8 Message transport procedures
8.1 General
8.2 Transport of NAS messages over control plane
8.2.1 General
8.2.2 TCP packet encapsulation
8.2.3 Establishment of TCP connection for transport of NAS messages
8.2.3A Re-establishment of TCP connection for transport of NAS messages
8.2.4 Transport of NAS messages over TCP connection
8.2.5 Release of TCP connection for transport of NAS messages
8.3 Transport of messages over user plane
8.3.1 General
8.3.2 Generic routing encapsulation (GRE)
...
...
8 Message transport procedures p. 75
8.1 General p. 75
In trusted and untrusted non-3GPP access, the UE establishes IKE SA and signalling IPsec SA i.e. the first child SA for NAS message exchange. Thereafter the UE establishes other child SAs for exchange of the user data packets. IPsec tunnel mode is employed for all the established child SAs including the first child SA for the signalling, to protect and encrypt the original IP user data packets, the original IP signalling packets and the port numbers used for communications of such IP packets. This clause is to list the parameters and the procedures for such IP tunneling mode of the signalling IPsec SA and the user data child SAs.
In wireline access, the 5G-RG establishes signalling connection using W-CP protocol stack as described in clause 6.3.1. Thereafter the W-AGF serving the 5G-RG and the 5G-RG establish W-UP bearers for exchange of the user data packets as specified in clause 4.4.2.2.
8.2 Transport of NAS messages over control plane p. 76
8.2.1 General p. 76
In trusted and untrusted non-3GPP access, after the completion of IKE SA and establishment of signalling IPsec SA as specified in clause 7.3 for untrusted non-3GPP access and clause 7.3A for trusted non-3GPP access, the UE establishes with the N3IWF for untrusted non-3GPP access or the TNGF for trusted non-3GPP access a TCP connection for transport of NAS messages over the inner IP layer and the signalling IPsec SA as specified in clause 8.2.3. Once the TCP connection for transport of NAS messages is established, the UE performs NAS procedures over the TCP connection for transport of NAS messages. All uplink and downlink NAS mobility management messages and NAS session management messages are relayed between the UE and the AMF via N3IWF for untrusted non-3GPP access and the TNGF for trusted non-3GPP access using the TCP connection for transport of NAS messages as specified in clause 8.2.4. Once the TCP connection is established and upon detection of a TCP connection failure, the UE and the N3IWF for untrusted non-3GPP access or the UE and the TNGF for trusted non-3GPP access re-establish the TCP connection as specified in clause 8.2.3A. When the TCP connection for transport of NAS messages is no longer needed, the UE, the N3IWF for untrusted non-3GPP access or the TNGF for trusted non-3GPP access release the TCP connection as specified in clause 8.2.5.
In wireline access, all uplink and downlink NAS mobility management messages and NAS session management messages are relayed between the 5G-RG and the AMF via W-AGF serving the 5G-RG using the signalling connection using W-CP protocol stack. If access network parameters, such as GUAMI, selected PLMN ID, requested NSSAI, establishment cause, and selected NID if the 5G-RG is accessing an SNPN, are provided along with an uplink NAS message, the access network parameters are relayed along the NAS message from the 5G-RG to the W-AGF serving the 5G-RG using the signalling connection using W-CP protocol stack. Transport using the signalling connection using W-CP protocol stack is out of scope of the present document.
8.2.2 TCP packet encapsulation p. 76
If a TCP packet is transported between the UE and the N3IWF for untrusted non-3GPP access or the TNGF for trusted non-3GPP access, and:
a)
If the UE receives an IKE_AUTH response message containing both NAS_IP4_ADDRESS and NAS_IP6_ADDRESS notify payload, the UE:
if the IKE_AUTH response message contained the INTERNAL_IP4_ADDRESS attribute and the NAS_IP4_ADDRESS notify payload, an inner IPv4 datagram shall be constructed where:
b)
-
the TCP packet shall be encapsulated in the inner IPv4 datagram with IPv4 header where:
-
if the UE constructs the inner IPv4 datagram:
- the source address field shall be set to the IPv4 address in the INTERNAL_IP4_ADDRESS attribute;
- the source port number shall be set to the UE's TCP port number;
- the destination address field shall be set to the IPv4 address in the NAS_IP4_ADDRESS notify payload; and
- the destination port number shall be set to the NAS_TCP_PORT notify payload;
-
if the N3IWF for untrusted non-3GPP access or the TNGF for trusted non-3GPP access constructs the inner IPv4 datagram:
- the source address field shall be set to the IPv4 address in the NAS_IP4_ADDRESS notify payload;
- the source port number shall be set to the NAS_TCP_PORT notify payload;
- the destination address field shall be set to the IPv4 address in the INTERNAL_IP4_ADDRESS attribute; and
- the destination port number shall be set to the UE's TCP port number; and
-
if the UE constructs the inner IPv4 datagram:
- the protocol field shall be set to 06H;
-
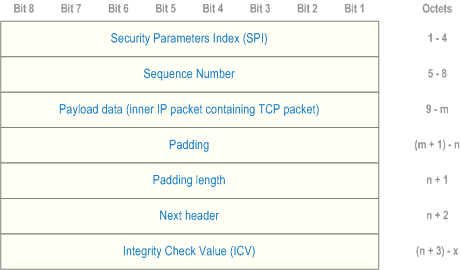
the inner IPv4 datagram shall be protected employing the ESP protocol in tunnel mode as specified in RFC 4303 where:
- the SPI field in the ESP packet shall be set to the SPI of the signalling IPsec SA; and
- the next header field in the ESP packet shall be set to 04H; and
- the IP packet encapsulating the ESP protected inner IPv4 datagram shall be sent to the peer for the SPI of the signalling IPsec SA; or
if the IKE_AUTH response message contained the INTERNAL_IP6_ADDRESS attribute and the NAS_IP6_ADDRESS notify payload, an inner IPv6 datagram shall be constructed where:
-
the TCP packet shall be encapsulated in the inner IPv6 datagram with IPv6 header where:
-
if the UE constructs the inner IPv6 datagram:
- the source address field shall be set to the IPv6 address in the INTERNAL_IP6_ADDRESS attribute;
- the source port number shall be set to the UE's TCP port number;
- the destination address field shall be set to the IPv6 address in the NAS_IP6_ADDRESS notify payload; and
- the destination port number shall be set to the NAS_TCP_PORT notify payload;
-
if the N3IWF for untrusted non-3GPP access or the TNGF for trusted non-3GPP access constructs the inner IPv6 datagram:
- the source address field shall be set to the IPv6 address in the NAS_IP6_ADDRESS notify payload;
- the source port number shall be set to the NAS_TCP_PORT notify payload;
- the destination address field shall be set to the IPv6 address in the INTERNAL_IP6_ADDRESS attribute; and
- the destination port number shall be set to the UE's TCP port number; and
- the next header field shall be set to 06H;
-
if the UE constructs the inner IPv6 datagram:
-
the inner IPv6 datagram shall be protected employing the ESP protocol in tunnel mode as specified in RFC 4303 where:
- the SPI field in the ESP packet shall be set to the SPI of the signalling IPsec SA; and
- the next header field in the ESP packet shall be set to 29H, and
- the IP packet encapsulating the ESP protected inner IPv6 datagram shall be sent to the peer for the SPI of the signalling IPsec SA.
- shall select and use either NAS_IP4_ADDRESS or NAS_IP6_ADDRESS;
- shall not switch between NAS_IP4_ADDRESS and NAS_IP6_ADDRESS for TCP packet transport during the lifetime of the IKE SA; and
- shall not switch between NAS_IP4_ADDRESS and NAS_IP6_ADDRESS when rekeying any child SA or IKE SA.
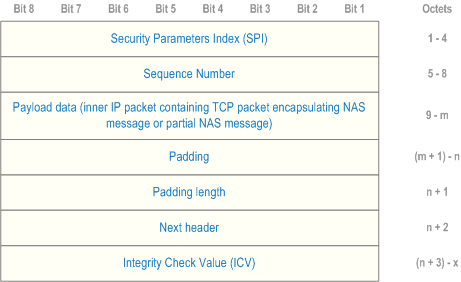
8.2.3 Establishment of TCP connection for transport of NAS messages p. 78
For transport of NAS messages, the UE shall initiate establishment of a TCP connection as defined in RFC 793. The UE and the N3IWF for untrusted non-3GPP access and the TNGF for trusted non-3GPP access shall construct and transport TCP packets according to clause 8.2.2.
8.2.3A Re-establishment of TCP connection for transport of NAS messages |R16| p. 78
The UE, the N3IWF for untrusted non-3GPP access or the TNGF for trusted non-3GPP access upon detection that the transport of a NAS message over the TCP connection is unsuccessful due to TCP connection failure, e.g. as indicated by the reception of a TCP error message, shall re-establish the TCP connection as defined in RFC 793. The UE and the N3IWF for untrusted non-3GPP access and the TNGF for trusted non-3GPP access shall construct and transport TCP packets according to clause 8.2.2.
8.2.4 Transport of NAS messages over TCP connection p. 78
In order to transport a NAS message over the untrusted non-3GPP access between the UE and the N3IWF or over the trusted non-3GPP access between the UE and the TNGF:
- the NAS message shall be framed in a NAS message envelope as defined in clause 9.4;
- the NAS message envelope shall be transported as a payload of one or more TCP packets using the TCP connection; and
- the UE and the N3IWF for untrusted non-3GPP access and the TNGF for trusted non-3GPP access shall transport the one or more TCP packets encapsulating the NAS message envelope according to clause 8.2.2.
8.2.5 Release of TCP connection for transport of NAS messages p. 79
In order to release the TCP connection for transport of NAS messages, the UE, the N3IWF for untrusted non-3GPP access or the TNGF for trusted non-3GPP access shall initiate release of the TCP connection as defined in RFC 793. The UE, the N3IWF for untrusted non-3GPP access and the TNGF for trusted non-3GPP access shall construct and transport TCP packets according to clause 8.2.2.
8.3 Transport of messages over user plane p. 79
8.3.1 General p. 79
In trusted and untrusted non-3GPP access, after the completion of PDU session establishment via non-3GPP access, user plane IPsec SAs are established as specified in clause 7.5. The UE is able to send and receive GRE encapsulated user data packets over non-3GPP access network via N3IWF in untrusted non-3GPP access and TNGF in trusted non-3GPP access. GRE encapsulation of user plane data packets is described in clause 8.3.2.
In wireline access, after the completion of PDU session establishment via wireline access, one or more W-UP resources are established as specified in clause 4.4.2.2. The 5G-RG is able to send and receive the user data packet, the QFI associated with the downlink user data packet, and RQI (in downlink direction only) via the selected W-UP resource and the W-AGF serving the 5G-RG as specified in clause 4.4.2.2.
For an uplink user data packet associated with a PDU session ID and a QFI:
-
if there is a user plane IPsec SA or a W-UP resource:
- associated with a PDU session ID matching the PDU session ID associated with the uplink user data packet; and
- associated with a QFI matching the QFI associated with the uplink user data packet; the UE or the 5G-RG shall select that user plane IPsec SA or that W-UP resource, respectively;
-
otherwise, the UE or the 5G-RG shall select the user plane IPsec SA or the W-UP resource, respectively:
- associated with a PDU session ID matching the PDU session ID associated with the uplink user data packet; and
- associated with the indication that the child SA is the default child SA.
8.3.2 Generic routing encapsulation (GRE) p. 79
If a user data packet message is transmitted over non-3GPP access between the UE and the N3IWF for untrusted non-3GPP access and the TNGF for the trusted non-3GPP access, the user data packet message shall be encapsulated as a GRE user data packet with a GRE header as specified in clause 9.3.3. In the GRE encapsulated user data packet:
If the IKE_AUTH response message contains:
a0)
the protocol type field is set to zero;
a)
the payload packet field is set to the user data packet;
b)
the QFI field of the key field of the GRE header field is set to the QFI associated with the user data packet;
c)
if the N3IWF for untrusted non-3GPP access and the TNGF for trusted non-3GPP access:
d)
- needs to send RQI for a downlink user data packet, the RQI field of the key field of the GRE header is set to "RQI is indicated" as defined in Table 9.3.3-3; or
- does not need to send RQI for a downlink user data packet, the RQI field of the key field of the GRE header is set to "RQI is not indicated" as defined in Table 9.3.3-3; and
if the UE sends an uplink user data packet, the RQI field of the key field of the GRE header is set to "RQI is not indicated" as defined in Table 9.3.3-3.
a)
If a user data packet message is transmitted over non-3GPP access between the UE and the N3IWF for untrusted non-3GPP access and the TNGF for trusted non-3GPP access, the user data packet message shall be encapsulated in the payload of an inner IP datagram which is further encapsulated by ESP protocol in tunnel mode as specified in RFC 4303. In order to avoid any IP fragmentation by the sending entity over the non-3GPP access network, the maximum inner IP datagram length shall be set by the sending entity such that the length of the resulting outer IP datagram does not exceed the MTU of the non-3GPP access network. If the length of the user data packet message exceeds the payload size corresponding to the maximum inner IP datagram length and IP fragmentation is needed:
the INTERNAL_IP4_ADDRESS attribute and the CREATE_CHILD_SA request message creating the user plane IPsec SA contains the UP_IP4_ADDRESS notify payload in subclause 7.5.4, an inner IPv4 datagram shall be constructed where:
b)
-
the GRE user data packet shall be encapsulated as the payload of the inner IPv4 datagram with IPv4 header where:
- if the UE constructs the inner IPv4 datagram, the source address field shall be set to the IPv4 address in the INTERNAL_IP4_ADDRESS attribute and the destination address field shall be set to the IPv4 address in the UP_IP4_ADDRESS notify payload;
- if the N3IWF for untrusted non-3GPP access and the TNGF for trusted non-3GPP access constructs the inner IPv4 datagram, the source address field shall be set to the IPv4 address in the UP_IP4_ADDRESS notify payload and the destination address field shall be set to the IPv4 address in the INTERNAL_IP4_ADDRESS attribute; and
- the protocol field shall be set to 2FH;
-
the inner IPv4 datagram shall be protected employing the ESP protocol in tunnel mode as specified in RFC 4303 where:
- the SPI field in the ESP packet shall be set to the SPI of the user plane IPsec SA; and
- the next header field in the ESP packet shall be set to 04H,
- if the DSCP field is associated with the user plane IPsec SA, the DSCP field as specified in RFC 2474 of the IP packet encapsulating the ESP protected inner IPv4 datagram shall be set to the value of the DSCP field included in the 5G_QOS_INFO Notify payload; and
- the IP packet encapsulating the ESP protected inner IPv4 datagram shall be sent to the peer for the SPI of the user plane IPsec SA; or
the INTERNAL_IP6_ADDRESS attribute and the CREATE_CHILD_SA request message creating the user plane IPsec SA contains the UP_IP6_ADDRESS notify payload in clause 7.5.4, an inner IPv6 datagram shall be constructed where:
-
the GRE user data packet shall be encapsulated as the payload of the inner IPv6 datagram with IPv6 header where:
- if the UE constructs the inner IPv6 datagram, the source address field shall be set to the IPv6 address in the INTERNAL_IP6_ADDRESS attribute and the destination address field shall be set to the IPv6 address in the UP_IP6_ADDRESS notify payload;
- if the N3IWF for untrusted non-3GPP access and the TNGF for trusted non-3GPP access constructs the inner IPv6 datagram, the source address field shall be set to the IPv6 address in the UP_IP6_ADDRESS notify payload and the destination address field shall be set to the IPv6 address in the INTERNAL_IP6_ADDRESS attribute; and
- the next header field shall be set to 2FH;
-
the inner IPv6 datagram shall be protected employing the ESP protocol in tunnel mode as specified in RFC 4303 where:
- the SPI field in the ESP packet shall be set to the SPI of the user plane IPsec SA; and
- the next header field in the ESP packet shall be set to 29H;
- if the DSCP field is associated with the user plane IPsec SA, the DSCP field as specified in RFC 2474 of the IP packet encapsulating the ESP protected inner IPv6 datagram shall be set to the value of the DSCP field included in the 5G_QOS_INFO Notify payload; and
- the IP packet encapsulating the ESP protected inner IPv6 datagram shall be sent to the peer for the SPI of the user plane IPsec SA.
- the inner IP IPv4 datagram or inner IP IPv6 datagram shall be fragmented; and
- the IP packet encapsulating the ESP protected inner IPv4 datagram and the IP packet encapsulating the ESP protected inner IPv6 datagram shall not be fragmented.