Content for TS 24.502 Word version: 19.0.0
7.3 IKE SA establishment procedure for untrusted non-3GPP access
7.3.1 General
7.3.2 IKE SA and signalling IPsec SA establishment procedure
7.3.2.1 IKE SA and signalling IPsec SA establishment initiation
7.3.2.2 IKE SA and signalling IPsec SA establishment accepted by the network
7.3.2.3 IKE SA and signalling IPsec SA establishment not accepted by the network
7.3.3 EAP-5G session over non-3GPP access
7.3.3.1 General
7.3.3.1A EAP-5G session initiation
7.3.3.2 EAP-5G session completion initiated by the network
7.3.3.3 EAP-5G session completion initiated by the UE
7.3.4 Abnormal cases in the UE
7.3.5 Abnormal cases in the N3IWF
7.3.6 Procedures for UE behind the 5G-RG accessing 5GC via untrusted non-3GPP access network
...
...
7.3 IKE SA establishment procedure for untrusted non-3GPP access p. 52
7.3.1 General p. 52
The purpose of this procedure is to establish a secure connection between the UE and the N3IWF over NWu, which is used to securely exchange the NAS signalling messages between the UE and the AMF via the N3IWF. The UE establishes the secure connection by establishing an IKE SA and first child SA to the N3IWF. The IKE SA and first child SA, called signalling IPsec SA, are created between the UE and the N3IWF after the IKE_SA_INIT exchange and after the IKE_AUTH exchange (see RFC 7296). The signalling IPsec established is used to transfer NAS signalling traffic. Additional child SAs (user plane IPsec SAs) can be established between the UE and the N3IWF to transfer user-plane traffic (see clause 7.5).
Upon completion of the N3IWF selection procedure (clause 7.2) the UE initiates an IKE_SA_INIT exchange as specified in RFC 7296. Upon reception of the IKE_SA_INIT exchange the UE shall inform the upper layers that the access stratum connection is established.
Upon establishment of the access stratum connection, the UE initiates IKE_AUTH exchange (see RFC 7296) with EAP-5G encapsulation, as specified in clause 7.3.2.
The UE encapsulates the initial NAS message and the AN parameters using the EAP-5G procedure as described in clause 7.3.3. The signalling IPsec SA is established after completion of the EAP-5G procedure and IKE_AUTH exchange.
7.3.2 IKE SA and signalling IPsec SA establishment procedure p. 52
7.3.2.1 IKE SA and signalling IPsec SA establishment initiation p. 52
The UE proceeds with the establishment of IKE SA and signalling IPsec SA with the selected N3IWF by initiating an IKE_SA_INIT exchange according to RFC 7296. All the IKE messages following the IKE_SA_INIT exchange are encrypted and integrity protected using the cryptographic algorithms and keys negotiated in the IKE_SA_INIT exchange as specified in RFC 7296.
Upon completion of the IKE_SA_INIT exchange, the UE shall initiate an IKE_AUTH exchange as specified in RFC 7296 to establish an IKE SA and first child SA (signalling IPsec SA). In the initial IKE_AUTH request message, the UE shall:
- indicate the intention to use EAP by not including the AUTH payload;
- include the IDi payload with the ID type set to ID_KEY_ID and value set to any random number;
- include CERTREQ payload to request N3IWF's certificate if the UE is provisioned with the N3IWF root certificate; and
- include the HPA_INFO Notify payload, as defined in TS 24.302, within the IKE_AUTH request message if the UE has a valid Access Identity 1 as specified in clause 4.5.2 of TS 24.501;
- an EAP-Request/5G-Start packet to inform the UE an EAP-5G session that will be used to convey the initial NAS messages (see the EAP-5G procedure described in clause 7.3.3);
- the IDr payload with the value set to N3IWF identifier; and
- the CERT payload containing the N3IWF's certificate if the CERTREQ payload is included in the IKE_AUTH request message.
7.3.2.2 IKE SA and signalling IPsec SA establishment accepted by the network p. 53
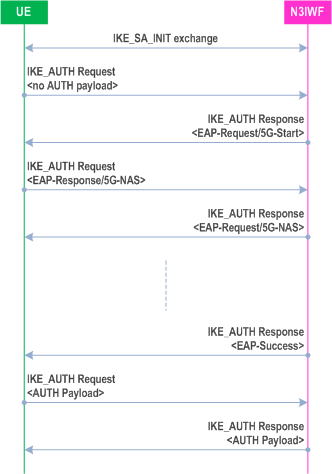
If IKE SA and signalling IPsec SA establishment is accepted by the network, the UE receives from the N3IWF an IKE_AUTH response message containing an EAP-Success message (as shown in Figure 7.3.2.2-1), which completes the EAP-5G session. No further EAP-5G packets are exchanged.
The UE completes the IKE SA and signalling IPsec SA (first child SA) establishment procedure by initiating an IKE_AUTH exchange including an AUTH payload computed based on the N3IWF key as described in TS 33.501.
In the initial IKE_AUTH request message the UE shall include:
- the INTERNAL_IP4_ADDRESS attribute, the INTERNAL_IP6_ADDRESS attribute, or both, indicating the type of IP address to be used for the IP tunnels, in the CFG_REQUEST configuration payload. The INTERNAL_IP4_ADDRESS attribute shall contain no value and the length field shall be set to 0. The INTERNAL_IP6_ADDRESS attribute shall contain no value and the length field shall be set to 0; and
- the MOBIKE_SUPPORTED notify payload as specified in RFC 4555 if the UE supports RFC 4555.
- a single CFG_REPLY Configuration Payload including the INTERNAL_IP4_ADDRESS attribute with an IPv4 address assigned to the UE, the INTERNAL_IP6_ADDRESS attribute with an IPv6 address assigned to the UE, or both;
- the NAS_IP4_ADDRESS notify payload with an N3IWF IPv4 address assigned to transport of NAS messages, if the initial IKE_AUTH request message contained a CFG_REQUEST configuration payload with the INTERNAL_IP4_ADDRESS attribute and NAS messages are to be transmitted using IPv4 based inner IP tunnel;
- the NAS_IP6_ADDRESS notify payload with an N3IWF IPv6 address assigned to transport of NAS messages if the initial IKE_AUTH request message contained a CFG_REQUEST configuration payload with the INTERNAL_IP6_ADDRESS attribute and NAS messages are to be transmitted using IPv6 based inner IP tunnel;
- the NAS_TCP_PORT notify payload with an N3IWF TCP port number assigned to transport of NAS messages; and
- the MOBIKE_SUPPORTED notify payload as specified in RFC 4555, if the initial IKE_AUTH request message contained a MOBIKE_SUPPORTED configuration payload with the INTERNAL_IP4_ADDRESS attribute.
7.3.2.3 IKE SA and signalling IPsec SA establishment not accepted by the network p. 54
If IKE SA and signalling IPsec SA establishment is not accepted by the network, the UE receives from the N3IWF an IKE_AUTH response message including a Notify payload with an error type.
Upon receiving the IKE_AUTH response message with a Notify payload with an error type other than a CONGESTION Notify payload, the UE shall pass the error indication to the upper layer along with the encapsulated NAS messages, if any, within EAP/5G-NAS packet.
After the N3IWF receives from the UE an IKE_AUTH request message, the N3IWF shall construct an IKE_AUTH response message including a CONGESTION Notify payload as defined in clause 9.2.4.2 and a N3GPP_BACKOFF_TIMER Notify payload as defined in clause 9.3.1.7. if the N3IWF decides to not accept the IKE SA and signalling IPsec SA establishment based on the OVERLOAD START message received from the AMF(s) as specified in TS 29.413.
Based on regional/national requirements and network operator policy, unless doing so would cause network instability, the N3IWF may exempt a UE that is being treated with MPS priority (e.g., as identified in clause 7.3.2.1 or 7.3A.2.2) from congestion controls.
The N3IWF shall send the IKE_AUTH response message to the UE. Upon reception of the IKE_AUTH response message including:
- a CONGESTION Notify payload as defined in clause 9.2.4.2; and
- a N3GPP_BACKOFF_TIMER Notify payload as defined in clause 9.3.1.7; and
-
if the back-off timer value in N3GPP_BACKOFF_TIMER Notify payload indicates neither zero nor deactivated, the UE shall start the Tw3 timer with the value provided and the UE shall not retry the IKE SA and signalling IPsec SA establishment procedure to the same N3IWF until:
- timer Tw3 expires;
- the UE is switched off;
- the UICC containing the USIM is removed;
- an access attempt occurs due to emergency services; or
- the UE needs to request one or more S-NSSAIs that were not included in the requested NSSAI provided to the N3IWF previously;
-
if the back-off timer value in N3GPP_BACKOFF_TIMER Notify payload indicates that this timer is deactivated, the UE shall not retry the IKE SA and signalling IPsec SA establishment procedure to the same N3IWF until:
- the UE is switched off;
- the UICC containing the USIM is removed;
- an access attempt occurs due to emergency services; or
- the UE needs to request one or more S-NSSAIs that were not included in the requested NSSAI provided to the N3IWF previously; and
- if the back-off timer value in N3GPP_BACKOFF_TIMER Notify payload indicates zero, the UE may retry the IKE SA and signalling IPsec SA establishment procedure to an N3IWF from the same PLMN.
7.3.3 EAP-5G session over non-3GPP access p. 56
7.3.3.1 General p. 56
A vendor-specific EAP method (EAP-5G) is used to encapsulate NAS messages between the UE and the N3IWF. The EAP-5G packets utilize the "Expanded" EAP type and the existing 3GPP Vendor-Id registered with IANA under the SMI Private Enterprise Code registry (i.e. 10415). The EAP-5G method is utilized only for encapsulating the NAS messages. The EAP-5G method is not utilized to authenticate the UE in untrusted non-3GPP network.
7.3.3.1A EAP-5G session initiation |R16| p. 56
The UE and the N3IWF shall exchange EAP-5G messages within IKE_AUTH request and IKE_AUTH response messages. The N3IWF on reception of an IKE_AUTH request with no AUTH payload shall start an EAP-5G session by sending an EAP-Request/5G-Start message.
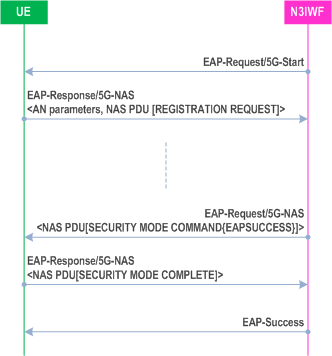
The UE acknowledges start of the EAP-5G session by sending an EAP-Response/5G-NAS message which shall include:
- a NAS-PDU field containing a NAS message, for example, a REGISTRATION REQUEST message; and
- an AN-parameters field containing access network parameters, such as GUAMI, selected PLMN ID, requested NSSAI, establishment cause, selected NID if the UE is accessing SNPN services via a PLMN or the UE is accessing SNPN services via untrusted non-3GPP access network, and onboarding indication if the UE is accessing SNPN for onboarding services in SNPN via untrusted non-3GPP access network (see TS 23.502).
7.3.3.2 EAP-5G session completion initiated by the network p. 56
Upon completion of successful authentication and on reception of the N3IWF key from the AMF, the N3IWF shall complete the EAP-5G session by sending an EAP-Success message.
On reception of the EAP-Success message from the N3IWF, the UE proceeds to establish an IKE SA and signalling IPsec SA as described in clause 7.3.2.
An example of an EAP-5G session after successful authentication is shown in Figure 7.3.3.2-1.
7.3.3.3 EAP-5G session completion initiated by the UE p. 57
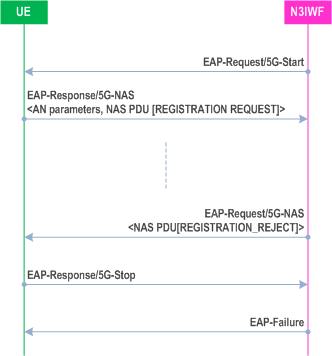
Upon receiving indication from the upper layer that no 5G-NAS messages need to be transmitted between the UE and N3IWF, the UE shall terminate the EAP-5G session by sending an EAP-Response/5G-Stop message to the N3IWF.
On reception of EAP-Response/5G-Stop message, the N3IWF shall complete the EAP-5G session by sending an EAP-Failure message to the UE.
On reception of the EAP-Failure message from the N3IWF, the UE shall delete any context related to IKE SA without requiring an explicit INFORMATIONAL exchange carrying a Delete payload as specified in RFC 7296.
Figure 7.3.3.3-1 shows an example the EAP-5G session completion after registration reject.
7.3.4 Abnormal cases in the UE p. 58
Apart from the cases specified in RFC 7296, no abnormal cases have been identified.
7.3.5 Abnormal cases in the N3IWF p. 58
Apart from the cases specified in RFC 7296, no abnormal cases have been identified.
7.3.6 Procedures for UE behind the 5G-RG accessing 5GC via untrusted non-3GPP access network |R18| p. 58
In wireline access, the UE behind the 5G-RG can access 5GC via untrusted non-3GPP access network.
For the 5G-RG to provide connectivity to the UE behind it to access the 5GC via untrusted non-3GPP access network, the 5G-RG registers to the 5GC and establishes a PDU session as described in TS 23.316. In order to achieve that:
- if the 5G-RG is connected to the 5GC through W-AGF, the 5G-RG shall first establish signalling connection using the W-CP protocol as described in clause 6.3.1, before proceeding with the registration procedure and the PDU session establishment procedure using the procedures specified in TS 24.501; or
- if the 5G-RG is connected to the 5GC through NG-RAN, the 5G-RG proceeds directly with the registration procedure and the PDU session establishment procedure using the procedures specified in TS 24.501.