Content for TS 24.501 Word version: 19.1.1
1…
3…
4…
4.4…
4.4.3…
4.5…
4.5.3…
4.6…
4.7…
4.9…
4.15…
5…
5.2…
5.3…
5.3.2…
5.3.7…
5.3.19…
5.4…
5.4.1.3…
5.4.2…
5.4.4…
5.4.5…
5.4.6…
5.5…
5.5.1.2.4
5.5.1.2.5…
5.5.1.3…
5.5.1.3.4
5.5.1.3.5…
5.5.2…
5.6…
5.6.2…
6…
6.1.4…
6.2…
6.3…
6.3.2…
6.3.3…
6.4…
6.4.1.4…
6.4.2…
6.5…
7…
8…
8.2.9…
8.3…
9…
9.11.2…
9.11.2.10…
9.11.3…
9.11.3.4…
9.11.3.8…
9.11.3.14…
9.11.3.18C…
9.11.3.29…
9.11.3.33…
9.11.3.39…
9.11.3.45…
9.11.3.50…
9.11.3.53A…
9.11.3.68…
9.11.3.75…
9.11.4…
9.11.4.10…
9.11.4.13…
9.11.4.16…
9.11.4.30…
9.12
10…
A…
B…
C…
D…
D.6…
D.6.3…
D.6.8
D.7…
5.4.2 Security mode control procedure
5.4.2.1 General
5.4.2.2 NAS security mode control initiation by the network
5.4.2.3 NAS security mode command accepted by the UE
5.4.2.4 NAS security mode control completion by the network
5.4.2.5 NAS security mode command not accepted by the UE
5.4.2.6 Abnormal cases in the UE
5.4.2.7 Abnormal cases on the network side
5.4.3 Identification procedure
5.4.3.1 General
5.4.3.2 Identification initiation by the network
5.4.3.3 Identification response by the UE
5.4.3.4 Identification completion by the network
5.4.3.5 Abnormal cases in the UE
5.4.3.6 Abnormal cases on the network side
...
...
5.4.2 Security mode control procedure p. 271
5.4.2.1 General p. 271
The purpose of the NAS security mode control procedure is to take a 5G NAS security context into use, and initialise and start NAS signalling security between the UE and the AMF with the corresponding 5G NAS keys and 5G NAS security algorithms.
Furthermore, the network may also initiate the security mode control procedure in the following cases:
- in order to change the 5G NAS security algorithms for a current 5G NAS security context already in use;
- in order to change the value of uplink NAS COUNT used in the latest SECURITY MODE COMPLETE message as described in subclause 6.9.4.4 of TS 33.501; and
- in order to provide the Selected EPS NAS security algorithms to the UE.
- delete the valid KAUSF and the valid KSEAF, if any; and
- consider the new KAUSF to be the valid KAUSF, and the new KSEAF to be the valid KSEAF, reset the SOR counter and the UE parameter update counter to zero, and store the valid KAUSF, the valid KSEAF, the SOR counter and the UE parameter update counter as specified in Annex C and use the valid KAUSF in the verification of SOR transparent container and UE parameters update transparent container, if any are received.
5.4.2.2 NAS security mode control initiation by the network p. 271
The AMF initiates the NAS security mode control procedure by sending a SECURITY MODE COMMAND message to the UE and starting timer T3560 (see example in Figure 5.4.2.2).
The AMF shall reset the downlink NAS COUNT counter and use it to integrity protect the initial SECURITY MODE COMMAND message if the security mode control procedure is initiated:
- to take into use the security context created after a successful execution of the 5G AKA based primary authentication and key agreement procedure or the EAP based primary authentication and key agreement procedure; or
- upon receipt of REGISTRATION REQUEST message, if the AMF needs to create a mapped 5G NAS security context (i.e. the type of security context flag is set to "mapped security context" in the ngKSI IE included in the SECURITY MODE COMMAND message).
- during an initial registration procedure for emergency services if no valid 5G NAS security context is available;
- during a registration procedure for mobility and periodic registration update for a UE that has an emergency PDU session if no valid 5G NAS security context is available;
- during a service request procedure for a UE that has an emergency PDU session if no valid 5G NAS security context is available; or
- after a failed primary authentication and key agreement procedure for a UE that has an emergency PDU session or is establishing an emergency PDU session, if continued usage of a valid 5G NAS security context is not possible.
- the AMF supports N26 interface;
- the UE set the S1 mode bit to "S1 mode supported" in the 5GMM capability IE of the REGISTRATION REQUEST message; and
- the security mode control procedure is initiated during an initial registration procedure for emergency services, during a registration procedure for mobility and periodic registration update for a UE that has an emergency PDU session, or during a service request procedure for a UE that has an emergency PDU session,
- during an initial registration procedure for emergency services;
- during a registration procedure for mobility and periodic registration update for a UE that has an emergency PDU session;
- during a service request procedure for a UE that has an emergency PDU session; or
- after a primary authentication and key agreement procedure for a UE that has an emergency PDU session or is establishing an emergency PDU session.
- indicate the use of the new mapped 5G NAS security context to the UE by setting the type of security context flag in the ngKSI IE to "mapped security context" and the KSI value related to the security context of the source system; or
- set the ngKSI value to "000" in the ngKSI IE if the AMF sets 5G-IA0 and 5G-EA0 as the selected NAS security algorithms for a UE that has an emergency PDU session.
- the 3GPP access, the AMF includes the ngKSI in the SECURITY MODE COMMAND message over the 3GPP access. When the AMF sends the SECURITY MODE COMMAND message to UE over the non-3GPP access to take into use the new 5G NAS security context, the AMF shall include the same ngKSI in the SECURITY MODE COMMAND message to identify the new 5G NAS security context; or
- the non-3GPP access, the AMF includes the ngKSI in the SECURITY MODE COMMAND message over the non-3GPP access. When the AMF sends the SECURITY MODE COMMAND message to UE over the 3GPP access to take into use the new 5G NAS security context, the AMF shall include the same ngKSI in the SECURITY MODE COMMAND message to identify the new 5G NAS security context.
- the REGISTRATION REQUEST message does not successfully pass the integrity check at the AMF; or
- the AMF can not decipher the value part of the NAS message container IE in the REGISTRATION REQUEST message;
- the DEREGISTRATION REQUEST message does not successfully pass the integrity check at the AMF; or
- the AMF can not decipher the value part of the NAS message container IE in the DEREGISTRATION REQUEST message;
- SERVICE REQUEST message; or
- CONTROL PLANE SERVICE REQUEST message excluding non-cleartext IEs, except the Uplink data status IE if needed (see subclause 5.4.2.3);
- the Master session key, if the AUN3 device does not support 5G key hierarchy; or
- the KWAGF key, if the AUN3 device supports 5G key hierarchy.
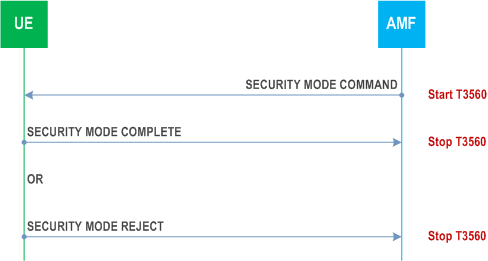
5.4.2.3 NAS security mode command accepted by the UE p. 275
Upon receipt of the SECURITY MODE COMMAND message, the UE shall check whether the security mode command can be accepted or not. This is done by performing the integrity check of the message, and by checking that the received Replayed UE security capabilities IE has not been altered compared to the latest values that the UE sent to the network.
When the SECURITY MODE COMMAND message includes an EAP-success message the UE handles the EAP-success message and the ABBA as described in subclause 5.4.1.2.2.8, 5.4.1.2.3.1, 5.4.1.2.3A.1, 5.4.1.2.3B.1 and 5.4.1.2.3C.1.
If:
- the UE is registered for emergency services, performing initial registration for emergency services, establishing an emergency PDU session or has an emergency PDU session established;
- the W-AGF acts on behalf of the FN-RG;
- the W-AGF acts on behalf of the N5GC device; or
- the 5G-RG acts on behalf of the AUN3 device,
- the UE is registered for emergency services, performing initial registration for emergency services, establishing an emergency PDU session or has an emergency PDU session established;
- the W-AGF acts on behalf of the FN-RG;
- the W-AGF acts on behalf of the N5GC device; or
- the 5G-RG acts on behalf of the AUN3 device.
- the SECURITY MODE COMMAND message is received in order to take a 5G NAS security context into use created after a successful execution of the 5G AKA based primary authentication and key agreement procedure or the EAP based primary authentication and key agreement procedure; or
- the SECURITY MODE COMMAND message received includes the type of security context flag set to "mapped security context" in the NAS key set identifier IE the ngKSI does not match the current 5G NAS security context, if it is a mapped 5G NAS security context.
- if the SECURITY MODE COMMAND message has been successfully integrity checked using an estimated downlink NAS COUNT equal to 0, then the UE shall set the downlink NAS COUNT of this new 5G NAS security context to 0;
- otherwise the UE shall set the downlink NAS COUNT of this new 5G NAS security context to the downlink NAS COUNT that has been used for the successful integrity checking of the SECURITY MODE COMMAND message.
- the UE is in 5GMM-IDLE mode over the non-current access, the AMF and the UE shall activate the new 5G NAS security context over the non-current access as described in TS 33.501. The AMF and the UE shall set the downlink NAS COUNT and uplink NAS COUNT to zero for the non-current access; or
- the UE is in 5GMM-CONNECTED mode over the non-current access, the AMF shall send the SECURITY MODE COMMAND message over the non-current access to activate the new 5G NAS security context that was activated over the current access as described in TS 33.501. The AMF shall include the same ngKSI in the SECURITY MODE COMMAND message to identify the new 5G NAS security context.
- the UE is in 5GMM-IDLE mode over the non-current access, the AMF and the UE shall activate the new 5G NAS security context for the non-current access. If a primary authentication and key agreement procedure was completed before the security mode control procedure, the AMF and the UE shall set the downlink NAS COUNT and uplink NAS COUNT to zero for the non-current access, otherwise the downlink NAS COUNT and uplink NAS COUNT for the non-3GPP access are not changed; or
- the UE is in 5GMM-CONNECTED mode over the non-current access, the AMF shall send the SECURITY MODE COMMAND message over the non-current access to activate the new 5G NAS security context that was activated over the current access as described in TS 33.501. The AMF shall include the same ngKSI in the SECURITY MODE COMMAND message to identify the new 5G NAS security context.
-
if the UE:
- supports at least one 3GPP access technology, the UE shall include its IMEISV in the IMEISV IE of the SECURITY MODE COMPLETE message; or
- does not support any 3GPP access technology (i.e. satellite NG-RAN, NG-RAN, satellite E-UTRAN, E-UTRAN, UTRAN or GERAN) and supports NAS over untrusted or trusted non-3GPP access, the UE shall include its EUI-64 in the non-IMEISV PEI IE of the SECURITY MODE COMPLETE message; or
-
if:
- the 5G-RG contains neither an IMEISV nor an IMEI or when the 5G-RG acts on behalf of the AUN3 device; or
- when the W-AGF acts on behalf of the FN-RG (or on behalf of the N5GC device),
- shall not include any non-cleartext IE, except the Uplink data status IE; and
- may include the Uplink data status IE.
5.4.2.4 NAS security mode control completion by the network p. 277
The AMF shall, upon receipt of the SECURITY MODE COMPLETE message, stop timer T3560. From this time onward the AMF shall integrity protect and encipher all signalling messages with the selected 5GS integrity and ciphering algorithms.
If the SECURITY MODE COMPLETE message contains a NAS message container IE with a REGISTRATION REQUEST message, the AMF shall complete the ongoing registration procedure by considering the REGISTRATION REQUEST message contained in the NAS message container IE as the message that triggered the procedure.
If the SECURITY MODE COMPLETE message contains a NAS message container IE with a DEREGISTRATION REQUEST message, the AMF shall complete the ongoing deregistration procedure by considering the DEREGISTRATION REQUEST message contained in the NAS message container IE as the message that triggered the procedure.
If the SECURITY MODE COMPLETE message contains a NAS message container IE with a REGISTRATION REQUEST message, the 5GMM capability IE included in the REGISTRATION REQUEST message indicates "S1 mode supported" and the AMF supports N26 interface, the AMF shall initiate another NAS security mode control procedure in order to provide the selected EPS NAS security algorithms to the UE as described in subclause 5.4.2.2. This second NAS security mode control procedure should be initiated as part of 5GMM common procedures of the ongoing registration procedure.
If the SECURITY MODE COMPLETE message contains a NAS message container IE with a SERVICE REQUEST message, the AMF shall complete the ongoing service request procedure by considering the SERVICE REQUEST message contained in the NAS message container IE as the message that triggered the procedure.
If the SECURITY MODE COMPLETE message contains a NAS message container IE with a CONTROL PLANE SERVICE REQUEST message, the AMF shall complete the ongoing service request procedure by considering the CONTROL PLANE SERVICE REQUEST message contained in the NAS message container IE as the message that triggered the procedure.
5.4.2.5 NAS security mode command not accepted by the UE p. 278
If the security mode command cannot be accepted, the UE shall send a SECURITY MODE REJECT message. The SECURITY MODE REJECT message contains a 5GMM cause that typically indicates one of the following cause values:
#23
If the UE detects that the received Replayed UE security capabilities IE has been altered compared to the latest values that the UE sent to the network, the UE shall set the cause value to #23 "UE security capabilities mismatch".
Upon receipt of the SECURITY MODE REJECT message, the AMF shall stop timer T3560. The AMF shall also abort the ongoing procedure that triggered the initiation of the NAS security mode control procedure.
Both the UE and the AMF shall apply the 5G NAS security context in use before the initiation of the security mode control procedure, if any, to protect the SECURITY MODE REJECT message and any other subsequent messages according to the rules in subclause 4.4.4 and 4.4.5.
UE security capabilities mismatch.
#24
security mode rejected, unspecified.
5.4.2.6 Abnormal cases in the UE p. 278
The following abnormal cases can be identified:
- Transmission failure of SECURITY MODE COMPLETE message or SECURITY MODE REJECT message indication from lower layers (if the security mode control procedure is triggered by a registration procedure). The UE shall abort the security mode control procedure and re-initiate the registration procedure.
- Transmission failure of SECURITY MODE COMPLETE message or SECURITY MODE REJECT message indication with change in the current TAI (if the security mode control procedure is triggered by a service request procedure). If the current TAI is not in the TAI list, the security mode control procedure shall be aborted and a registration procedure shall be initiated. If the current TAI is still part of the TAI list, the security mode control procedure shall be aborted and it is up to the UE implementation how to re-run the ongoing procedure that triggered the security mode control procedure.
- Transmission failure of SECURITY MODE COMPLETE message or SECURITY MODE REJECT message indication without change in the current TAI (if the security mode control procedure is triggered by a service request procedure). The security mode control procedure shall be aborted and it is up to the UE implementation how to re-run the ongoing procedure that triggered the security mode control procedure.
-
NAS security mode command not accepted by the UE as specified in subclause 5.4.2.5 and there is an ongoing:
- service request procedure for emergency services fallback the UE shall abort the service request procedure, stop timer T3517, locally release the N1 NAS signalling connection and locally release any resources allocated for the service request procedure and enter state 5GMM-REGISTERED; or
- registration procedure for mobility and periodic registration update triggered upon a request from the upper layers to perform an emergency services fallback procedure the UE shall abort the registration procedure for mobility and periodic registration update, stop timer T3510, locally release the N1 NAS signalling connection and locally release any resources allocated for the registration procedure for mobility and periodic registration update and enter the state 5GMM-REGISTERED; and
5.4.2.7 Abnormal cases on the network side p. 279
The following abnormal cases can be identified:
- Lower layer failure before the SECURITY MODE COMPLETE or SECURITY MODE REJECT message is received. The network shall abort the security mode control procedure.
- Expiry of timer T3560. The network shall, on the first expiry of the timer T3560, retransmit the SECURITY MODE COMMAND message and shall reset and start timer T3560. This retransmission is repeated four times, i.e. on the fifth expiry of timer T3560, the procedure shall be aborted.
- Collision between security mode control procedure and registration, service request or de-registration procedure not indicating switch off. The network shall abort the security mode control procedure and proceed with the UE initiated procedure.
- Collision between security mode control procedure and other 5GMM procedures than in item c. The network shall progress both procedures.
- Lower layers indication of non-delivered NAS PDU due to handover: If the SECURITY MODE COMMAND message could not be delivered due to an intra AMF handover and the target TA is included in the TAI list, then upon successful completion of the intra AMF handover the AMF shall retransmit the SECURITY MODE COMMAND message. If a failure of the handover procedure is reported by the lower layer and the N1 signalling connection exists, the AMF shall retransmit the SECURITY MODE COMMAND message.
5.4.3 Identification procedure p. 279
5.4.3.1 General p. 279
The purpose of this procedure is to request a particular UE to provide specific identification parameters, e.g. the SUCI, the IMEI, the IMEISV, the EUI-64 or the MAC address. The SUCI is a privacy preserving identifier containing the concealed SUPI and the IMEI, the IMEISV, the EUI-64 and the MAC address are formats of PEI.
5.4.3.2 Identification initiation by the network p. 280
The AMF initiates the identification procedure by sending an IDENTITY REQUEST message to the UE and starting timer T3570 (see example in Figure 5.4.3.2.1). The IDENTITY REQUEST message specifies the requested identification parameters in the Identity type information element.

5.4.3.3 Identification response by the UE p. 280
A UE shall be ready to respond to an IDENTITY REQUEST message at any time whilst in 5GMM-CONNECTED mode.
Upon receipt of the IDENTITY REQUEST message:
- if the Identity type IE in the IDENTITY REQUEST message is not set to "SUCI", the UE shall send an IDENTITY RESPONSE message to the network. The IDENTITY RESPONSE message shall contain the identification parameters as requested by the network; and
-
if the Identity type IE in the IDENTITY REQUEST message is set to "SUCI", the UE shall:
- if timer T3519 is not running, generate a fresh SUCI as specified in TS 33.501, send an IDENTITY RESPONSE message with the SUCI, start timer T3519 and store the value of the SUCI sent in the IDENTITY RESPONSE message; and
- if timer T3519 is running, send an IDENTITY RESPONSE message with the stored SUCI.
5.4.3.4 Identification completion by the network p. 280
Upon receipt of the IDENTITY RESPONSE the network shall stop the timer T3570.
5.4.3.5 Abnormal cases in the UE p. 280
The following abnormal cases can be identified:
- Transmission failure of the IDENTITY RESPONSE message (if the identification procedure is triggered by a registration procedure). The UE shall re-initiate the registration procedure.
- Requested identity is not available If the UE cannot encode the requested identity in the IDENTITY RESPONSE message, e.g. because no valid USIM is available, then it shall encode the identity type as "No identity".
5.4.3.6 Abnormal cases on the network side p. 280
The following abnormal cases can be identified:
- Lower layer failure. Upon detection of a lower layer failure before the IDENTITY RESPONSE is received, the network shall abort any ongoing 5GMM procedure.
- Expiry of timer T3570. The network shall, on the first expiry of the timer T3570, retransmit the IDENTITY REQUEST message and reset and restart the timer T3570. This retransmission is repeated four times, i.e. on the fifth expiry of timer T3570, the network shall abort the identification procedure and any ongoing 5GMM procedure.
- Collision of an identification procedure with a registration procedure for initial registration. If the network receives a REGISTRATION REQUEST message indicating either "initial registration" or "emergency registration" in the 5GS registration type IE before the ongoing identification procedure has been completed and no registration procedure is pending on the network (i.e. no REGISTRATION ACCEPT/REJECT message has still to be sent as an answer to a REGISTRATION REQUEST message), the network shall proceed with the registration procedure for initial registration.
-
Collision of an identification procedure with a registration procedure for initial registration when the identification procedure has been caused by a registration procedure for initial registration.
If the network receives a REGISTRATION REQUEST message indicating either "initial registration" or "emergency registration" in the 5GS registration type IE before the ongoing identification procedure has been completed and a registration procedure for initial registration is pending (i.e. a REGISTRATION ACCEPT/REJECT message has to be sent as an answer to an earlier REGISTRATION REQUEST message), then:
- If one or more of the information elements in the REGISTRATION REQUEST message differ from the ones received within the previous REGISTRATION REQUEST message, the network shall proceed with the new registration procedure for initial registration; or
- If the information elements do not differ, then the network shall not treat any further this new REGISTRATION REQUEST message.
- Collision of an identification procedure with a registration procedure for mobility and periodic registration update. If the network receives a REGISTRATION REQUEST message indicating either "mobility registration updating" or "periodic registration updating" in the 5GS registration type IE before the ongoing identification procedure has been completed, the network shall progress both procedures.
- Collision of an identification procedure with a UE initiated de-registration procedure. If the network receives a DEREGISTRATION REQUEST message with "switch off" indication in the De-registration type IE before the ongoing identification procedure has been completed, the network shall abort the identification procedure and shall progress the UE-initiated de-registration procedure; Else the network shall complete the identification procedure and shall respond to the UE-initiated de-registration procedure as described in subclause 5.5.2.2.