Content for TS 33.501 Word version: 18.4.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
Z Authentication of AUN3 devices using additional EAP methods
Z.1 General
Z.2 Authentication of AUN3 devices by 5GC
Z.3 Authentication of AUN3 devices by AAA server
$ Change history
Z (Normative) Authentication of AUN3 devices using additional EAP methods |R18| p. 311
Z.1 General p. 311
This Annex describes the authentication procedure for AUN3 devices behind 5G-RG in private networks or in isolated deployment scenarios (i.e., roaming is not supported) using any key generating EAP method.
An AUN3 device may be authenticated by the 5GC or a Credential Holder using a AAA server.
Z.2 Authentication of AUN3 devices by 5GC p. 311
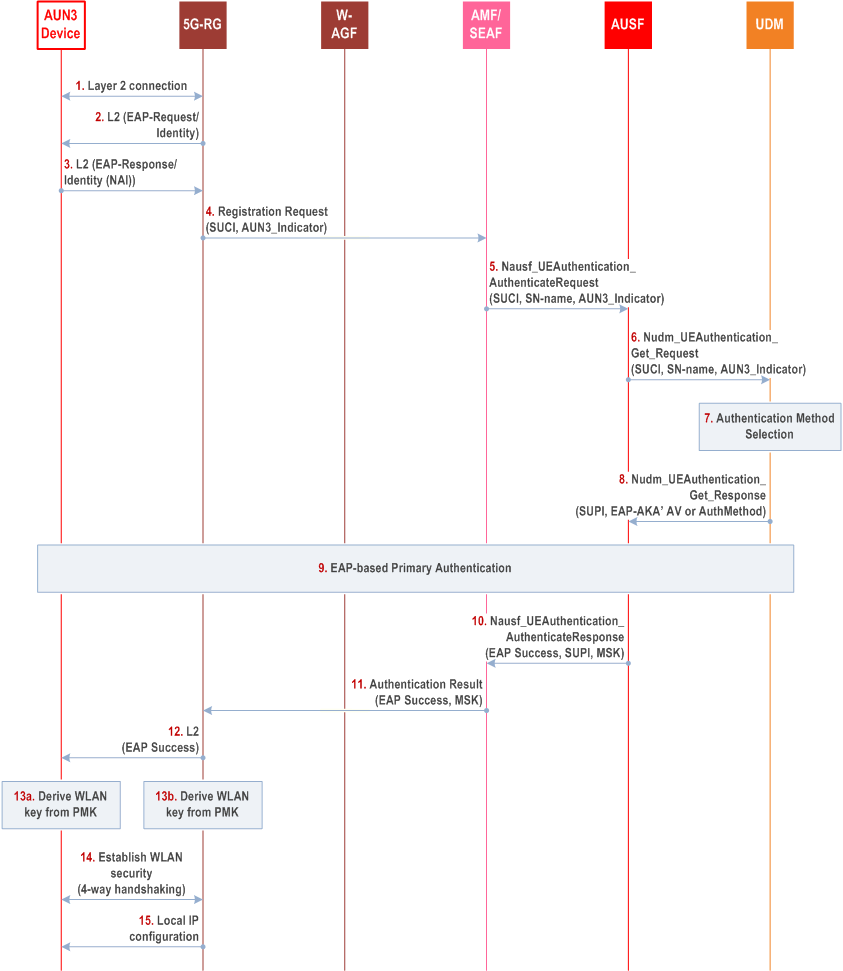
This authentication procedure is based on clause 7B.7.3 but differs in some steps.
Steps 1-6 are the same as steps 1-6 in clause 7B.7.3.
Step 7.
Steps 10-15 are the same as steps 17-22 in clause 7B.7.3.
Upon reception of the Nudm_UEAuthentication_Get Request, the UDM shall invoke the SIDF to map the SUCI to the SUPI and select an authentication method based on the SUPI and the AUN3 device indicator. When the "username" part of the SUPI is "anonymous" or omitted, the UDM may select an authentication method based on the "realm" part of the SUPI, the AUN3 device indicator, a combination of the "realm" part and the AUN3 device indicator, or the UDM local policy. When EAP-AKA' authentication method is selected, the UDM/ARPF shall generate an authentication vector using the Access Network Identity as the KDF input parameter.
Step 8.
The UDM shall send to the AUSF a Nudm_UEAuthentication_Get Response message, including the SUPI and EAP-AKA' authentication vector if EAP-AKA' is selected or the selected authentication method if other key generating EAP method (e.g., EAP-TLS, EAP-TTLS, etc) is selected. According to the AUN3 subscription data, the UDM shall also send the MSK indicator to AUSF.
Step 9.
The AUN3 device and the AUSF perform the selected EAP authentication method.
Z.3 Authentication of AUN3 devices by AAA server p. 313
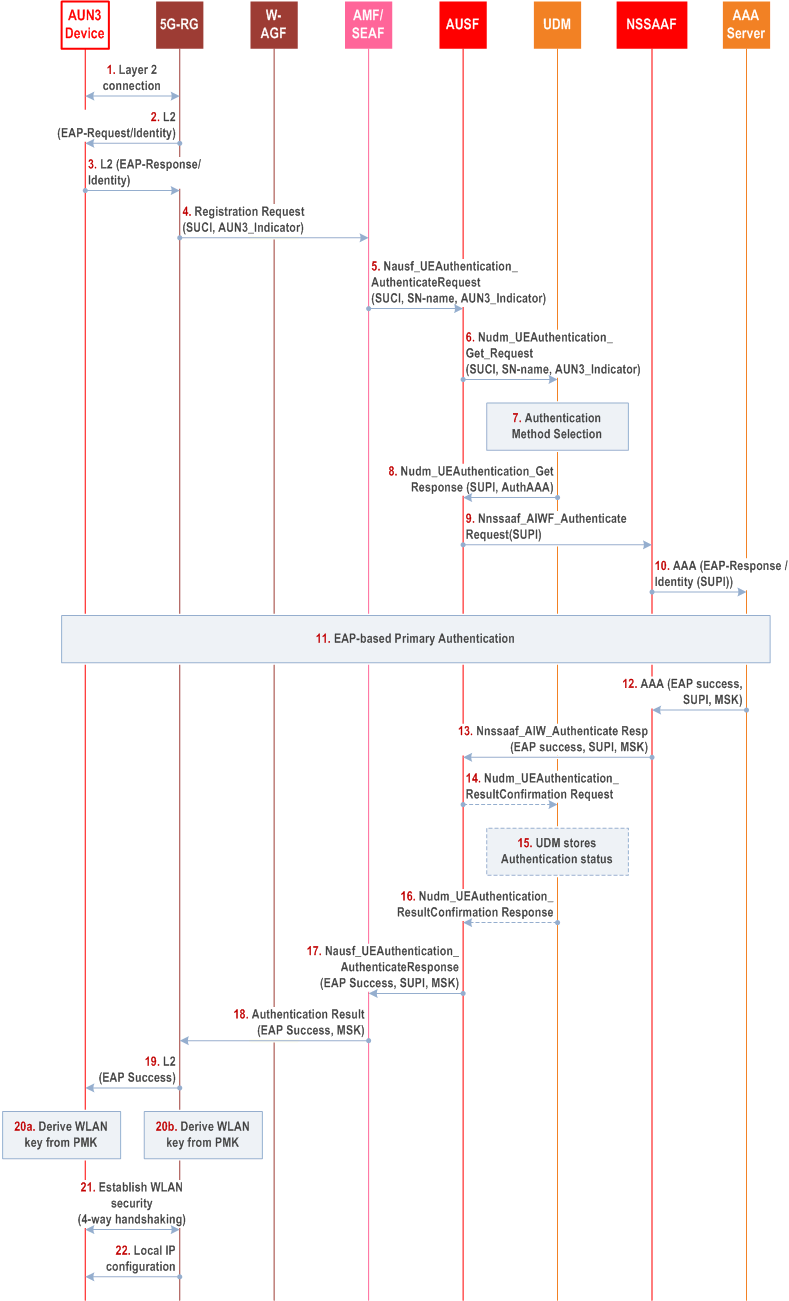
This authentication procedure is based on clause 7B.7 and I.2.2.2.2.
Steps 1-6 are the same as steps 1-6 in clause 7B.7.
Steps 7-16 are the same as steps 4-13 in clause I.2.2.2.2.
Steps 17-22 are the same as steps 17-22 in clause 7B.7.