Content for TS 33.501 Word version: 18.4.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
G Application layer security on the N32 interface
G.1 Introduction
G.2 Structure of HTTP Message
...
...
G Application layer security on the N32 interface p. 246
G.1 Introduction p. 246
The SEPP as described in clause 4.2.1 is the entity that sits at the perimeter of the network and performs application layer security on the HTTP message before it is sent externally over the roaming interface.
The application layer traffic comprises all the IEs in the HTTP message payload, sensitive information in HTTP message header and Request URI. Not all the IEs get the same security treatment in SEPP. Some IEs require e2e encryption, some only require e2e integrity protection, while other IEs may require e2e integrity protection but modifiable by intermediate IPX provider while in-transit.
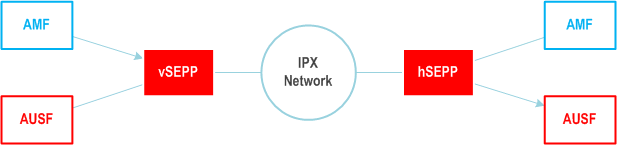
In the above Figure, an example is shown where the AMF NF in the visited PLM network (vPLMN) invokes an API request on the AUSF NF in the home PLM network (hPLMN) using the following message flow:
- The AMF NF first sends the HTTP Request message to its local SEPP (i.e. vSEPP).
- The vSEPP applies application layer security (PRINS) and sends the secure message on the N32 interface to AUSF NF of the hPLMN.
- The hSEPP at the edge of the hPLMN, receives all incoming HTTP messages from its roaming partners. It verifies the message, removes the protection mechanism applied at the application layer, and forwards the resulting HTTP message to the corresponding AUSF NF.
- Sensitive information such as authentication vectors are fully e2e confidentiality protected between two SEPPs. This ensures that no node in the IPX network shall be able to view such information while in-transit.
- IEs that are subject to modification by roaming intermediary IPX nodes are integrity protected and can only be modified in a verifiable way by authorized IPX nodes.
- Receiving SEPP can detect modification by unauthorized IPX nodes.
G.2 Structure of HTTP Message p. 247
Following is a typical structure of the HTTP Message:
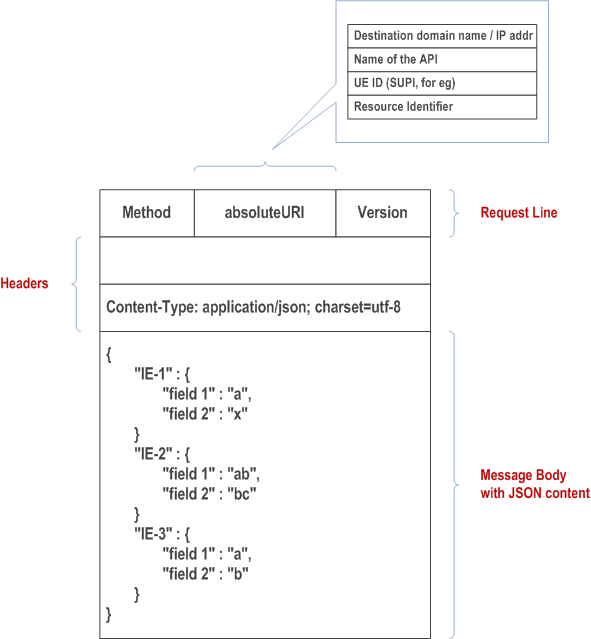
It consists of:
- HTTP Message payload with JSON based IEs
- HTTP Headers with or without sensitive elements
- HTTP Request-URI with or without sensitive elements such as SUPI.