Content for TS 33.501 Word version: 18.4.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
I.9 Security of UE onboarding in SNPNs
I.9.1 General
I.9.2 Authentication
I.9.2.1 Requirements
I.9.2.2 Primary authentication without using DCS
I.9.2.3 Primary authentication using DCS
I.9.2.4 Secondary authentication
I.9.2.4.1 Secondary authentication using DCS
I.9.2.4.2 Secondary authentication using DN-AAA
I.10 Security for access to SNPN services via Non-3GPP access
I.10.1 General
I.10.2 Security for access to SNPN services via Untrusted non-3GPP access
I.10.2.0 General
I.10.2.1 Untrusted non-3GPP access support in SNPN without CH
I.10.2.2 Untrusted non-3GPP access support in SNPN with CH
I.10.3 Security for access to SNPN services via Trusted non-3GPP access
I.10.3.0 General
I.10.3.1 Trusted non-3GPP access support in SNPN without CH
I.10.3.2 Trusted non-3GPP access support in SNPN with CH
I.10.4 Security for access to SNPN services for N5CW devices
I.10.4.0 General
I.10.4.1 Support for N5CW devices in SNPN without CH
I.10.4.2 Support for N5CW devices in SNPN with CH
I.10.5 Security for NSWO support in SNPN
I.10.5.1 NSWO support in SNPN using CH with AAA server
I.10.5.2 NSWO support in SNPN without CH
I.10.5.3 NSWO support in SNPN using CH with AUSF/UDM
I.11 Security for accessing a localised service
...
...
I.9 Security of UE onboarding in SNPNs |R17| p. 256
I.9.1 General p. 256
Onboarding of UEs for SNPNs is specified in clause 5.30.2.10 of TS 23.501.
Onboarding of UEs for SNPNs allows the UE to access an Onboarding Network (ONN) based on Default UE credentials for the purpose of provisioning the UE with SNPN credentials and any other necessary information. The Default UE credentials are pre-configured on the UE. Default UE credentials consist of credentials for primary authentication and optionally credentials for secondary authentication.
To provision SNPN credentials in a UE that is configured with Default UE credentials, the UE selects an SNPN as ONN and establishes a secure connection with that SNPN referred to as Onboarding SNPN (ON-SNPN).
The present clause specifies security of UE onboarding.
I.9.2 Authentication p. 256
I.9.2.1 Requirements p. 256
The primary authentication shall be performed before UE onboarding is allowed. For primary authentication, the UE shall use Default UE credentials for primary authentication. Credentials or means used to authenticate the UE based on Default UE credentials for primary authentication may be stored within the ON-SNPN or in a Default Credentials Server (DCS) that is external to the ON-SNPN.
The UE shall use Onboarding SUPI and Onboarding SUCI as specified in TS 24.501 during Onboarding Registration.
I.9.2.2 Primary authentication without using DCS p. 257
When the primary authentication is performed between the UE and the ON-SNPN, any one of the existing authentication methods defined in the present document may be used, i.e., 5G AKA, EAP-AKA' or any other key-generating EAP authentication method (e.g., EAP-TLS).
The choice of primary authentication method used is left to the decision of the ON-SNPN.
Credentials required to authenticate the UE using default UE credentials for primary authentication, are provisioned at the AUSF or AUSF/UDM of the ON-SNPN. The provisioning of this information is out of scope of this document.
I.9.2.3 Primary authentication using DCS p. 257
When the primary authentication is performed between the UE and the DCS, the authentication requirements and procedures defined in clause I.2 for Credential Holder shall apply with the DCS taking the role of the Credentials Holder. When the DCS uses AAA Server for primary authentication, AUSF directly selects the NSSAAF as specified in 23.501 [2]. In this case, the UDM is not involved in the procedure defined in clause I.2.2.2.2, and the step 3 to step 5 shall be skipped. When 5G AKA or EAP-AKA' is used, the DCS shall act as a AUSF/UDM.
The choice of primary authentication method used between the UE and the DCS is left to the decision of the DCS.
When the primary authentication is performed between the UE and the DCS via the AUSF using EAP-TTLS, Annex U can be used.
I.9.2.4 Secondary authentication p. 257
I.9.2.4.1 Secondary authentication using DCS p. 257
After successful primary authentication as described in I.9.2.2 (i.e. primary authentication without using DCS), upon the establishment of the Onboarding PDU Session, the ON-SNPN may trigger secondary authentication procedure with the DCS using Default UE credentials for secondary authentication, as described in clause 11.1.
I.9.2.4.2 Secondary authentication using DN-AAA p. 257
After successful primary authentication as described in clause I.9.2.2 or clause I.9.2.3, upon the establishment of the Onboarding PDU Session, the ON-SNPN may trigger secondary authentication procedure with a DN-AAA server using Default UE credentials for secondary authentication, as described in clause 11.1.
I.10 Security for access to SNPN services via Non-3GPP access |R18| p. 257
I.10.1 General p. 257
Access to SNPN services via Non-3GPP access is described in TS 23.501, sub-clauses of clause 5.30.2. Security for non-3GPP access to the 5G core network of PLMN is described in clause 7 and Annex S of this specification. The present clause describes changes and additions that apply in the SNPN case.
I.10.2 Security for access to SNPN services via Untrusted non-3GPP access p. 258
I.10.2.0 General p. 258
The decision to use a Credentials Holder using AAA is taken by the UDM. The selection criteria is described in step 4 of Annex I.2.2.2.2.
I.10.2.1 Untrusted non-3GPP access support in SNPN without CH p. 258
Procedures for untrusted non-3GPP access authentication are described in clause 7.2.1. For SNPN the procedures are modified as follows:
Steps 1-4 are performed as described in clause 7.2.1.
In step 5, the SUCI can be an onboarding SUCI.
Further in step 5, the SUCI can be of type anonymous SUCI if the construction of SUCI as described in clause 6.12 cannot be used and if the employed EAP method supports SUPI privacy.
Step 6 is performed as described in clause 7.2.1.
In step 7 of clause 7.2.1, in case the AUSF receives an onboarding indication, the AUSF shall perform steps 6-10 and 14-17 as described in Annex I.2.2.2.
In the selection of UE authentication method in step 7 of clause 7.2.1, 5G AKA, EAP-AKA', or any other key-generating EAP authentication method apply. When the "username" part of the SUPI is "anonymous" or omitted, the UDM may select an authentication method based on the "realm" part of the SUPI or on the UDM local policy.
In case the AUSF received an anonymous SUCI in step 7 (but no onboarding indication was received) the AUSF shall perform steps 11-13 of Annex I.2.2.2 after a successful authentication to inform the UDM of the actual SUPI. In case anonymous SUCI and onboarding indication was received in step 7, steps 11-13 of Annex I.2.2.2 can be skipped.
In step 8 of clause 7.2.1 in case an EAP method is used for primary authentication, the AMF shall encapsulate the EAP-Success received from AUSF within the SMC message.
Steps 9-16 are performed as described in clause 7.2.1.
I.10.2.2 Untrusted non-3GPP access support in SNPN with CH p. 258
UE may use the credentials from a Credentials Holder AAA server to access SNPN services via Untrusted non-3GPP access.
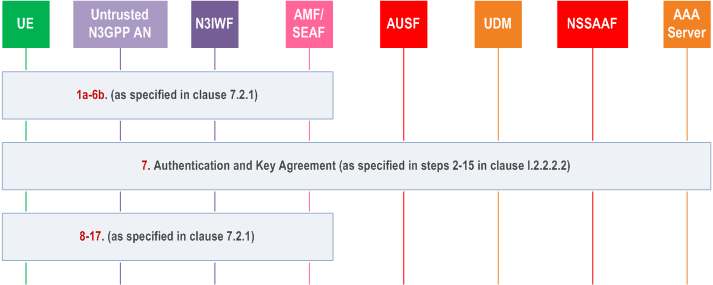
Step 0.
prior conditions and assumptions are described in step 0 in clause I.2.2.2.2.
Step 1a-6b.
as specified in clause 7.2.1. In addition, if the construction of SUCI as described in clause 6.12 cannot be used and if the employed EAP method supports SUPI privacy, the UE may send an anonymous SUPI based on configuration.
Step 7.
authentication and key agreement procedure between the UE and the AAA server, as specified in steps 2-15 in clause I.2.2.2.2.
Step 8-17.
as specified in clause I.10.2.1.
I.10.3 Security for access to SNPN services via Trusted non-3GPP access p. 259
I.10.3.0 General p. 259
The decision to use a Credentials Holder using AAA is taken by the UDM. The selection criteria is described in step 4 of Annex I.2.2.2.2.
I.10.3.1 Trusted non-3GPP access support in SNPN without CH p. 259
Procedures for trusted non-3GPP access authentication are described in clause 7A.2.1. For SNPN the procedures are re-used with the following modifications:
Steps 0-4 are performed as described in clause 7A.2.1.
In step 5, the SUCI can be an onboarding SUCI.
Further in step 5, the SUCI carried in AN parameter and NAS-PDU can be of type anonymous SUCI if the construction of SUCI as described in clause 6.12 cannot be used and if the employed EAP method supports SUPI privacy. If anonymous SUCI is used, the UE shall send a 64-bit random number as a key identifier in the AN parameters. The random number generation should follow the recommendations given in SP 800-90A [110] or equivalent. If the UE provides a key identifier already allocated in the TNGF, the UE will be rejected.
Step 6-7 is performed as described in clause 7A.2.1.
In step 8 of clause 7A.2.1, in case the AUSF receives an onboarding indication, the AUSF shall perform steps 6-10 and 14-17 as described in Annex I.2.2.2.
In the selection of UE authentication method in step 8 of clause 7A.2.1, 5G AKA, EAP-AKA', or any other key-generating EAP authentication method apply. When the "username" part of the SUPI is "anonymous" or omitted, the UDM may select an authentication method based on the "realm" part of the SUPI or on the UDM local policy.
In case the AUSF received an anonymous SUCI in step 7 (but no onboarding indication was received) the AUSF shall perform steps 11-13 of Annex I.2.2.2 after a successful authentication to inform the UDM of the actual SUPI. In case anonymous SUCI and onboarding indication was received in step 7, steps 11-13 of Annex I.2.2.2 can be skipped.
Steps 9-12 are performed as described in clause 7A.2.1.
In step 13, in case anonymous SUCI was used in step 5, the key identifier sent in the AN parameters is used in the IDi payload. If the key identifier is not the same as the one sent in step 5, the IPsec setup will fail and the UE will be rejected.
Steps 14-19 are performed as described in clause 7A.2.1.
I.10.3.2 Trusted non-3GPP access support in SNPN with CH p. 259
UE may use the credentials from a Credentials Holder AAA server to access SNPN services via Trusted Non-3GPP access.
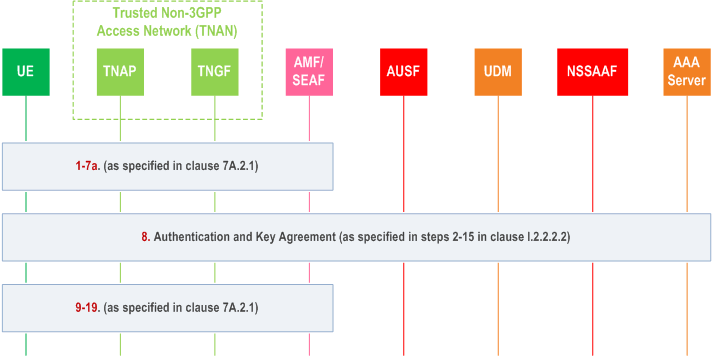
Step 0.
prior conditions and assumptions are described in step 0 in clause I.2.2.2.2.
Step 1-7a.
as specified in clause 7A.2.1. In addition, if the construction of SUCI as described in clause 6.12 cannot be used and if the employed EAP method supports SUPI privacy, the UE may send an anonymous SUPI based on configuration.
Step 8.
authentication and key agreement procedure between the UE and the AAA server, as specified in steps 2-15 in clause I.2.2.2.2.
Step 9-19.
as specified in clause I.10.3.1.
I.10.4 Security for access to SNPN services for N5CW devices p. 260
I.10.4.0 General p. 260
The decision to use a Credentials Holder using AAA is taken by the UDM. The selection criteria is described in step 4 of Annex I.2.2.2.2.
I.10.4.1 Support for N5CW devices in SNPN without CH p. 260
Procedures for authentication for devices that do not support 5GC NAS over WLAN access are described in clause 7A.2.4. For SNPN the procedures are modified as follows:
Steps 0-1 are performed as described in clause 7A.2.4.
In step 2 of clause 7A.2.4 the SUCI can be of type anonymous SUCI if the construction of SUCI as described in clause 6.12 cannot be used and if the employed EAP method supports SUPI privacy.
Step 3-6 is performed as described in clause 7A.2.4.
In the selection of UE authentication method in step 7 of clause 7A.2.4, any key-generating EAP authentication method apply. When the "username" part of the SUPI is "anonymous" or omitted, the UDM may select an authentication method based on the "realm" part of the SUPI or on the UDM local policy.
In step 8 of clause 7A.2.4, in case the AUSF received an anonymous SUCI in step 7, the AUSF shall perform steps 11-13 of Annex I.2.2.2 after a successful authentication to inform the UDM of the actual SUPI.
Steps 9-14 are performed as described in clause 7A.2.4.
I.10.4.2 Support for N5CW devices in SNPN with CH p. 260
N5CW devices may use the credentials from a Credentials Holder AAA server to access SNPN services via trusted WLAN access.
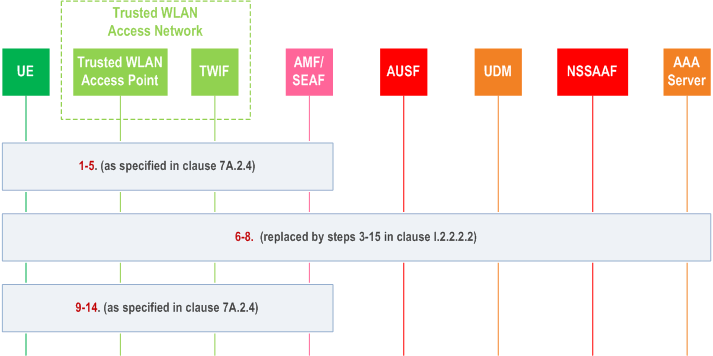
Step 0.
prior conditions and assumptions are described in step 0 in clauses 7A.2.4 and I.2.2.2.2.
Step 1-5.
as specified in clause 7A.2.4. In addition, if the construction of SUCI as described in clause 6.12 cannot be used and if the employed EAP method supports SUPI privacy, the UE may send an anonymous SUCI based on configuration..
Step 6-8.
are replaced by the steps 3-15 in clause I.2.2.2.2.
Step 9-14.
as specified in clause 7A.2.4.
I.10.5 Security for NSWO support in SNPN p. 261
I.10.5.1 NSWO support in SNPN using CH with AAA server p. 261
I.10.5.1.1 NSWO support in SNPN using CH with AAA server via AAA Proxies p. 261
The reference architecture to support authentication for Non-seamless WLAN offload using SNPN credentials from Credentials Holder using AAA Server is specified in Figure 4.2.15-3b of TS 23.501.
This clause applies to UEs that support NSWO in SNPN with any key generating EAP method by using the SNPN credentials with CH AAA server (i.e., the MSK indication described in step 0 of clause I.2.2.2.2 is configured on the UE). The UE shall reuse 5G NSWO procedures defined in Annex S.3.2 with WLAN access network for NSWO authentication with the same key generating EAP method that is used by the SNPN over 3GPP access with the following exception:
- The EAP authentication is performed between the UE and the CH AAA with no involvement of NSWOF/AUSF/UDM.
- The construction of SUCI described in this document is not applicable.
I.10.5.1.2 NSWO support in SNPN using CH with AAA server via 5GC p. 262
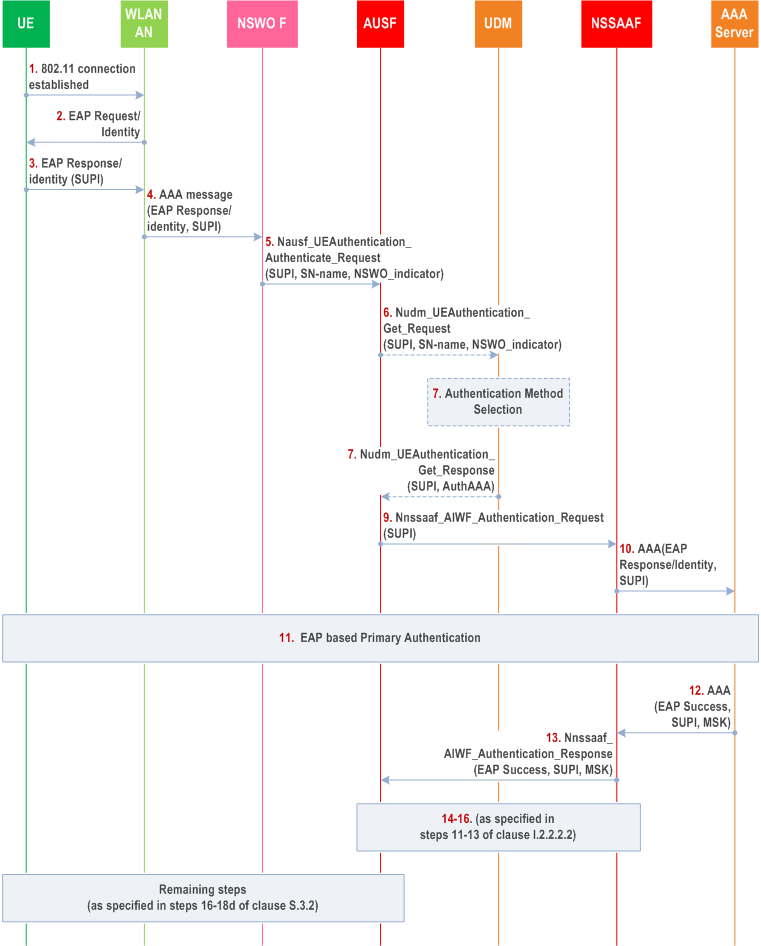
Step 1-5.
Remaining steps are performed as described in steps 16-18d of clause S.3.2.
Same as steps 1-5 of clause S.3.2, except that SUCI is replaced with SUPI. If the EAP method supports privacy and the UE is configured to use anonymous SUPI, the UE sends an anonymous SUPI.
Step 6.
Same as steps 3 of clause I.2.2.2, except that SUCI is replaced with SUPI and NSWO_indicator is also sent to the UDM by the AUSF.
Step 7-16.
Same as steps 4-13 of clause I.2.2.2.2.
I.10.5.2 NSWO support in SNPN without CH p. 262
5G NSWO procedures are defined in Annex S.3.2. For SNPN the procedures are extended to usage of any key-generating EAP-method as follows:
Steps 1-2 are performed as described in Annex S.3.2.
In step 3, the SUCI can be of type anonymous SUCI if the construction of SUCI as described in clause 6.12 cannot be used and if the employed EAP method supports SUPI privacy.
Steps 4-6 are performed as described in Annex S.3.2.
Step 7.
Steps 9-11 are performed as described in steps 16-18 of Annex S.3.2.
Upon reception of the Nudm_UEAuthentication_Get Request, the UDM invokes SIDF to de-conceal SUCI to gain SUPI if the received SUCI is not an anonymous SUCI. For selection of authentication methods, the statements in Annex I.2.2.1 apply. In case of SNPN, the UDM selects authentication method based on the NSWO indicator, subscription data and/or local configuration. The authentication method may include EAP-AKA' or any other key-generating EAP authentication method. The UDM returns the selected authentication method to the AUSF.
Step 8.
Authentication is performed between the AUSF and UE using the selected EAP method. After a successful authentication the AUSF derives the MSK key and does not generate the KAUSF, as indicated by the NSWO indicator and as described for the PLMN case in Annex S.3.2.
I.10.5.3 NSWO support in SNPN using CH with AUSF/UDM p. 263
The architecture for 5G NSWO in SNPN using CH AUSF/UDM is defined in clause 4.2.15 of TS 23.501.
The procedures are the same as those defined in Annex I.10.5.2.
I.11 Security for accessing a localised service |R18| p. 263
Accessing a localized service is specified in Annex N of TS 23.501. Existing authentication procedures, as described in this specification, for either primary authentication, secondary authentication, slice specific authentication or onboarding procedures can be used. The authentication methods include any key-generating EAP method when applicable.