Content for TS 33.503 Word version: 18.3.0
6.3.4 Security for 5G ProSe Communication via 5G ProSe Layer-2 UE-to-Network Relay
6.3.5 Direct Communication Request in 5G ProSe UE-to-Network Relay Communication
6.3.6 Security for emergency service from 5G ProSe Remote UE via 5G ProSe UE-to-Network Relay
6.3.6.1 General
6.3.6.2 Security requirements
6.3.6.3 Security for Emergency service via 5G ProSe Layer 2 UE-to-Network Relay and via 5G ProSe Layer-3 UE-to-Network Relay
6.3.6.3.1 Security procedure for supporting emergency service via 5G ProSe Layer 2 UE-to-Network Relay and via 5G ProSe Layer-3 UE-to-Network Relay
6.3.7 Security mechanism selection in path switching between two 5G ProSe UE-to-Network Relays
...
...
6.3.4 Security for 5G ProSe Communication via 5G ProSe Layer-2 UE-to-Network Relay p. 43
Connection establishment for 5G ProSe Communication via 5G ProSe Layer-2 UE-to-Network Relay is specified in clause 6.5.2.2 of TS 23.304. During the connection establishment, the 5G ProSe Remote UE and NG-RAN node shall establish AS security as specified in TS 33.501.
The 5G ProSe Remote UE and the 5G ProSe UE-to-Network Relay shall establish security for PC5 connection using either User Plane based solution as specified in clause 6.3.3.2 or Control Plane based solution as specified in clause 6.3.3.3.2. The requirements on security policies for PC5 connection between the 5G ProSe Remote UE and the Layer-2 UE-to-Network Relay are as follows:
- The PCF shall be able to provision the PC5 security policies to the 5G ProSe Remote UE and Layer-2 UE-to-Network Relay respectively per ProSe relay service during their service authorization and information provisioning procedures as defined in TS 23.304.
6.3.5 Direct Communication Request in 5G ProSe UE-to-Network Relay Communication p. 43
6.3.5.1 General p. 43
This clause describes the mechanism to protect the privacy of the UP-PRUK ID/CP-PRUK-ID and RSC in Direct Communication Request (DCR) message when restricted discovery is used for the UE-to-Network Relay service. This clause also describes a mechanism to integrity protect the DCR message when DUIK is provisioned for discovery.
6.3.5.2 Privacy protection of UP-PRUK ID and RSC in DCR p. 43
The 5G ProSe Remote UE encrypts the UP-PRUK ID/CP-PRUK ID and RSC using the code-receiving security parameters used for discovery. The 5G ProSe UE-to-Network Relay, on receiving the DCR message, decrypts the encrypted UP-PRUK ID/CP-PRUK ID and RSC using the code-sending security parameters used for discovery and verifies if the RSC matches with the one that it sent in the discovery message. If the RSC does not match, the 5G ProSe UE-to-Network Relay shall abort the PC5 direct link establishment procedure.
The 5G ProSe Remote UE shall encrypt the UP-PRUK ID/CP-PRUK ID and RSC as follows:
- If the UE is configured with Discovery User Confidentiality Key (DUCK), the DCR ciphering key KDCR is set to DUCK. If the UE is configured with Discovery User Scrambling Key (DUSK) but not DUCK, KDCR is set to DUSK. If the UE is neither configured with DUCK nor DUSK, the DCR message is not protected, and Steps 2-3 are skipped.
- Set Keystream to DCR confidentiality keystream calculated using KDCR, UTC-based counter and RSC as described in clause A.5.
- XOR the first L bits of the Keystream with the RSC where L is the length of the RSC, and XOR the remaining bits of the Keystream with the UP-PRUK ID/CP-PRUK ID.
- If the UE is configured with DUCK, the DCR ciphering key KDCR is set to DUCK. If the UE is configured with DUSK but not DUCK, KDCR is set to DUSK. If the UE is neither configured with DUCK nor DUSK, the DCR message is not protected, and steps 2-3 are skipped.
- Set Keystream to DCR confidentiality keystream calculated using KDCR, UTC-based counter and RSC as described in clause A.5.
- XOR the first L bits of Keystream with the encrypted RSC where L is the length of the encrypted RSC, and XOR the remaining bits of Keystream with the encrypted UP-PRUK ID/CP-PRUK ID.
6.3.5.3 Integrity protection of DCR p. 44
The 5G ProSe Remote UE integrity protects the DCR message using the code-receiving security parameters used for discovery. The integrity protection of the DCR message is performed after the privacy protection of UP-PRUK ID/CP-PRUK ID and RSC.
The 5G ProSe UE-to-Network Relay, on receiving the DCR message, verifies the integrity of the received DCR message using the code-sending security parameters used for discovery. If the integrity verification of the DCR fails, the 5G ProSe UE-to-Network Relay shall abort the PC5 direct link establishment procedure.
The 5G ProSe Remote UE shall integrity protect the DCR as follows:
- If the UE is configured with DUIK, the DCR integrity key KINT is set to DUIK. Otherwise, the DCR message is not integrity protected, and steps 2-3 are skipped.
- Calculate Message Integrity Check (MIC) using KINT, UTC-based counter and the DCR message as described in clause A.9.
- Set the MIC IE to the calculated MIC.
- If the UE is configured with DUIK, the DCR integrity key KINT is set to DUIK. Otherwise, the DCR message is not integrity protected, and step 2 is skipped.
- Calculate a MIC using KINT, UTC-based counter and the received DCR message as described in clause A.9 and compare the calculated MIC with the MIC included in the DCR message. If they mismatch, the integrity check fails.
6.3.6 Security for emergency service from 5G ProSe Remote UE via 5G ProSe UE-to-Network Relay |R18| p. 45
6.3.6.1 General p. 45
This clause describes the security requirements and the procedures that are specifically applied to support of emergency service via 5G ProSe Layer 2 UE-to-Network Relay and 5G ProSe Layer 3 UE-to-Network Relay defined in TS 23.304.
When a 5G ProSe enabled UE does not have direct connection to the network for emergency service, the UE may attempt to obtain emergency service via 5G ProSe Layer-2 or Layer-3 UE-to-Network Relay. A 5G ProSe enabled UE acting as 5G ProSe UE-to-Network Relay shall have a normal registration to support for relaying emergency service. Dedicated RSC(s) are used for relaying of emergency service as specified in TS 23.304.
Based on the regulatory requirements in some regions, emergency service over relay may be supported without PC5 link security. RSC(s) dedicated for emergency service needs to be provisioned in the 5G ProSe enabled UEs with capability of 5G ProSe UE-to-Network Relay and/or 5G ProSe Remote UE as specified in clause 5.1.4 of TS 23.304. Based on the regulation and the operator policy, there may or may not be discovery security materials provisioned for Emergency RSC.
6.3.6.2 Security requirements p. 45
The 5G system shall support the establishment of PC5 communication for emergency service over UE-to-network relay with or without PC5 security.
The security requirements defined in clause 6.3.2 and clause 6.3.3.1 apply for the case PC5 link security establishment is required for relaying emergency service.
Otherwise, the following security requirements apply based on the regulatory requirements in some regions:
- For relaying emergency service without PC5 link security, protection is not required for emergency service discovery.
- For relaying emergency service without PC5 link security, the PC5 signalling security shall support NULL ciphering algorithm and NULL integrity protection algorithm.
- For relaying emergency service without PC5 link security, the PC5 user plane security shall support no integrity protection (by not inserting a MAC-I) and NULL ciphering algorithm.
- For relaying emergency service without PC5 link security, PEI may be used to identify the 5G ProSe Remote UE.
6.3.6.3 Security for Emergency service via 5G ProSe Layer 2 UE-to-Network Relay and via 5G ProSe Layer-3 UE-to-Network Relay p. 45
6.3.6.3.1 Security procedure for supporting emergency service via 5G ProSe Layer 2 UE-to-Network Relay and via 5G ProSe Layer-3 UE-to-Network Relay p. 45
A 5G ProSe Remote UE can establish a PC5 security link for Emergency service with a network, via both a 5G ProSe Layer 2 UE-to-Network Relay and a 5G ProSe Layer-3 UE-to-Network Relay as specified in clause 6.3.3.
Based on the regulation, the operator policy and the UP security policies of the 5G ProSe Remote UE and the 5G ProSe UE-to-Network Relay for the emergency RSC, the UP traffic may be transmitted via a PC5 link without security protection for case that relaying emergency service with PC5 link security is not required.
6.3.6.3.1.1 PC5 security establishment for Emergency Service over UE-to-Network relay p. 46
Figure 6.3.6.3.1.1-1 shows the PC5 security establishment procedure for the 5G ProSe UE-to-Network Relay communication when an Emergency Relay Service Code is used. This procedure is based on the procedure in clause 6.3.3.2.2 and clause 6.3.3.3.2.
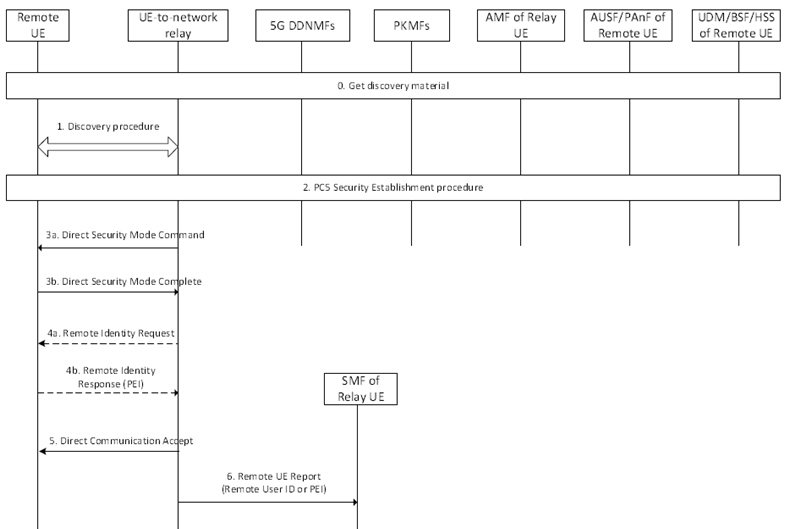
Figure 6.3.6.3.1.1-1: PC5 link security establishment for Emergency Service over UE-to-Network relay
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
If relaying emergency service with PC5 link security is not required for a 5G ProSe Remote UE has no USIM based on the regulation, there is no discovery security materials (and UP-PRUK in case of UP based security procedure) provisioned for an Emergency RSC.
Step 0.
If no discovery security material is provisioned or locally configured, the announcement and discovery of Emergency RSC may be performed without security protection if the regulation allow.
The 5G ProSe UE retrieves discovery material with the procedures as specified in clause 6.1.3.2. For UP based security procedure, the 5G ProSe Remote UE retrieves UP-PRUK as specified in step 1 of clause 6.3.3.2.2.
If the 5G ProSe Remote UE has no USIM, this step is skipped. The discovery security materials, if exist, and the Emergency RSC are locally configured in the 5G ProSe UE.
Step 1.
The discovery procedure for the Emergency RSC is performed between a 5G ProSe Remote UE, and the 5G ProSe UE-to-Network Relay, using the discovery parameters and discovery security material that are obtained in step 0.
Step 2.
If the 5G ProSe Remote UE has a USIM, the 5G ProSe Remote UE sends a Direct Communication Request (DCR) to trigger PC5 security establishment for Emergency RSC using UP based security procedure as specified in step 4 of clause 6.3.3.2.2 or CP based security procedure as specified in step 3 to step 13 of clause 6.3.3.3.2.
If the 5G ProSe Remote UE has no USIM, then the 5G ProSe Remote UE sends a Direct Communication Request that contains PEI and Emergency RSC to the 5G ProSe UE-to-Network Relay. The Direct Communication Request message including PEI and Emergency RSC may be sent without protection if no discovery security material is provisioned or locally configured in the 5G ProSe Remote UE.
If UP/CP-PRUK ID or SUCI is received from the 5G ProSe Remote UE, the 5G ProSe UE-to-Network Relay performs UP based security procedure as specified in step 4 of clause 6.3.3.2.2 or CP based security procedure as specified in step 3 to step 13 of clause 6.3.3.3.2.
If only PEI and Emergency RSC are received from the 5G ProSe Remote UE, the 5G ProSe UE-to-Network Relay skips step 4 of clause 6.3.3.2.2 for UP based security procedure or step 3 to step 13 of clause 6.3.3.3.2 for CP based security procedure if the regulation and the operator policy allow. The 5G ProSe UE-to-network relay shall store the PEI.
Step 3a.
If UP based security procedure as specified in step 4 of clause 6.3.3.2.2 or CP based security procedure as specified in step 3 to step 13 of clause 6.3.3.3.2 in step 2 was successfully performed, then the 5G ProSe UE-to-Network Relay shall proceed with the Direct Security Mode procedure as specified in steps 5a-5d in clause 6.3.3.2.2 for UP based security procedure or step 14 to step 16 of clause 6.3.3.3.2 for CP based security procedure.
If UP based security procedure as specified in step 4 of clause 6.3.3.2.2 or CP based security procedure as specified in step 3 to step 13 of clause 6.3.3.3.2 in step 2 failed or was skipped, the 5G ProSe UE-to-Network Relay shall send Direct Security Mode Command message to the 5G ProSe Remote UE indicating NULL ciphering algorithm and NULL integrity protection algorithm as chosen algorithms if the regulation and the operator policy allow.
When there has been no successful run of authentication of the 5G ProSe Remote UE, the 5G ProSe Remote UE and the 5G ProSe UE-to-Network Relay independently generate the KNRP or KNR_ProSe in an implementation defined way. All key derivations proceed as if they were based on a KNRP or KNR_ProSe generated from a successful authentication run.
If the 5G ProSe Remote UE receives the Direct Security Mode Command message indicating NULL integrity algorithm and NULL encryption algorithm as chosen algorithms, then the 5G ProSe Remote UE shall accept NULL ciphering and NULL integrity algorithms indicated in Direct Security Mode Command message if, and only if, the 5G ProSe Remote UE has sent an Emergency RSC in step 2. The 5G ProSe Remote UE shall set the UP integrity protection as not activated for this connection.
Step 3b.
If the 5G ProSe Remote UE receives the Direct Security Mode Command message indicating non-NULL integrity and non-NULL encryption algorithm then the 5G ProSe Remote UE proceeds step 5a-5d in clause 6.3.3.2.2 for UP based security procedure or step 14- step 16 of clause 6.3.3.3.2 for CP based security procedure.
If the 5G ProSe Remote UE receives the Direct Security Mode Command message indicating NULL integrity and NULL encryption algorithm in step 3a and has accepted the message, then the 5G ProSe Remote UE shall send a Direct Security Mode Complete message and shall include the UP integrity protection policy as NOT NEEDED in the Direct Security Mode Complete message.
If the 5G ProSe UE-to-network relay receives the Direct Security Mode Complete message with no protection, the 5G ProSe UE-to-Network Relay shall only accept the message if 5G ProSe UE-to-Network Relay sent Direct Security Mode Command message including NULL integrity and NULL encryption algorithm in step 3a and if the 5G ProSe Remote UE has sent an Emergency RSC in step 2.
Step 4a.
If UP based security procedure as specified in step 4 of clause 6.3.3.2.2 or CP based security procedure as specified in step 3 to step 13 of clause 6.3.3.3.2 in step 2 failed or was skipped and PEI is not received from the 5G ProSe Remote UE in the Direct Communication Request, the 5G ProSe UE-to-Network Relay sends a Remote Identity Request message to the 5G ProSe Remote UE to retrieve the PEI based on the regulation and the operator policy.
Step 4b.
When the 5G ProSe Remote UE receives a Remote Identity Request message from the 5G ProSe UE-to-Network relay, then the 5G ProSe Remote UE sends a Remote Identity Response message including its PEI to the 5G ProSe UE-to-network relay if, and only if, the 5G ProSe Remote UE has sent an Emergency RSC in step 2. The 5G ProSe UE-to-network relay shall store the PEI.
Step 5.
If the 5G ProSe UE-to-network relay receives the Direct Security Mode Complete message in step 3b, and after successful verification, the 5G ProSe UE-to-Network Relay responds with a protected Direct Communication Accept message to the 5G ProSe Remote UE to complete the PC5 connection establishment procedure.
If the 5G ProSe UE-to-network relay receives the Direct Security Mode Complete message with no protection, and the 5G ProSe UE-to-Network Relay has accepted the message based on the conditions described in step 3b, the 5G ProSe UE-to-Network Relay shall send Direct Communication Accept message with no protection to the 5G ProSe Remote UE.
The 5G ProSe UE-to-Network Relay includes the configuration of UP integrity and confidentiality protection based on the agreed UP security policy in the Direct Communication Accept message as specified in TS 33.536.
Step 6.
The 5G ProSe Remote UE and 5G ProSe UE-to-Network Relay continues the rest of procedure for the emergency service over relay as specified in TS 23.304. The 5G ProSe UE-to-Network Relay sends a Remote UE Report to the SMF for the Emergency RSC. The 5G ProSe UE-to-Network Relay includes Remote User ID i.e. (UP-/CP-) PRUK ID if UP or CP based security procedure is successfully performed. Otherwise, the 5G ProSe UE-to-Network Relay includes the PEI of the 5G ProSe Remote UE in the Remote UE Report.
If UP confidentiality protection is not activated for this connection, the UP confidentiality protection algorithm is the same as the selected signalling confidentiality algorithm as specified in TS 33.536.
If UP integrity protection is not activated for this connection, the 5G ProSe Remote UE and the 5G ProSe UE-to-Network Relay do not put MAC-I into PDCP packet.
UP protection for the layer 2 relaying emergency service shall be handled as specified in clause 10 of TS 33.501.
6.3.7 Security mechanism selection in path switching between two 5G ProSe UE-to-Network Relays |R18| p. 48
Based on the UE-to-Network relay reselection mechanism as per clause 5.15 of TS 23.304, the Remote UE performs the path switching between two UE-to-Network Relays with the following additional security considerations:
- The Remote UE first selects the RSC indicating the same security mechanism with the original path (i.e. User Plane based solution as specified in clause 6.3.3.2 or Control Plane based solution as specified in clause 6.3.3.3.2) to establish the PC5 security link with the new UE-to-Network Relay.