Content for TS 23.259 Word version: 18.0.0
5.3 PN-configuration
5.3.1 General
5.3.2 PN-configuration procedure in the IM CN subsystem
5.3.3 PN-configuration procedure for PNE other than a PN UE in the IM CN subsystem
5.4 PN-deconfiguration
5.5 PN-query
...
...
5.3 PN-configuration p. 14
5.3.1 General p. 14
The PN-configuration procedures enable the PN-user to configure UEs as the default UE for terminating requests addressed to any UE belonging to the same PN and to configure the PN access control list. The PN-configuration can be done in three levels in IM CN subsystem and two levels in CS domain. They are a global level for all services supported by the UE capabilities and subscriptions, a per service basis for selected services supported by the UE capabilities and subscriptions, and a per service component basis for the different media of a supported service for the UE.
The following subclause describes the PN-configuration procedures in the IM CN subsystem. The signalling flow in figure 5.3.2-1 describes the information flow exchange between UE and NAF/PNM AS when the UE performs the PN-configuration.
5.3.2 PN-configuration procedure in the IM CN subsystem p. 15
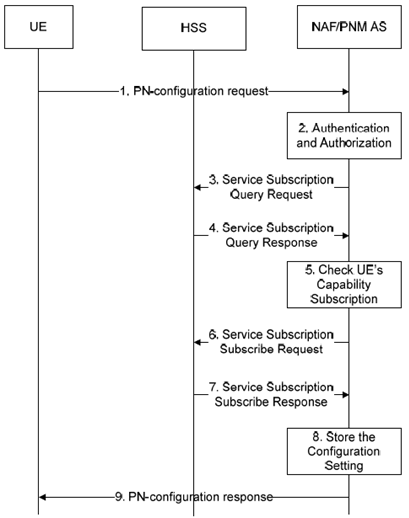
The signalling flow in Figure 5.3.2-1 describes the signal flow between UE and NAF/PNM AS when the UE wants to configure the PN. The procedure shall only take place after a successful bootstrapping procedure (as described in TS 33.220) in which case the bootstrapped security association has been established before Step 1.
Step 1.
UE sends a PN-configuration request to the NAF/PNM AS informing the PNM AS about its desirable settings for the PN UE redirection applications and/or the PN access control list. The PN-configuration request contains the public user identity/identities of the UE, and the PN UE names of the UEs to be configured. The relevant parameters for executing the PN UE redirection application (e.g configuration level and the priority value) may be included. The controller UE and controllee UE, and the PN access control list including either the public user identities (if reachable in the IM CN subsystem) and/or the directory number (if reachable in the CS domain) may be included.
Step 2.
Upon receiving this Configuration request message, the NAF/PNM AS authenticates the PN-configuration request according to the TS 33.222. After a successful authentication, the NAF inserts the private user identity of the UE and forwards the requestto the PNM AS. The PNM AS authorizes the Configuration request message by comparing the public user identity and the PN UE name with those ones that are registered in the PN by means of the PN-registration procedure.
Step 3.
The NAF/PNM AS sends a Service Subscription Query request to the HSS in order to obtain the service subscription tied to the public user identity received in the PN-configuration request.
Step 4.
The HSS sends a Service Subscription Query response back to the NAF/PNM AS with the service subscription tied to the public user identity.
Step 5.
Upon receiving the Service Subscription Query response, the NAF/PNM AS verifies the UE capability and the service subscription of the public user identity.
Step 6.
The NAF/PNM AS sends the Service Subscription Subscribe request to the HSS.
Step 7.
The HSS sends the Service Subscription Subscribe Response to the NAF/PNM AS.
Step 8.
The NAF/PNM AS stores the configuration settings.
Step 9.
The NAF/PNM AS sends the PN-configuration response to the UE.
5.3.3 PN-configuration procedure for PNE other than a PN UE in the IM CN subsystem |R9| p. 17
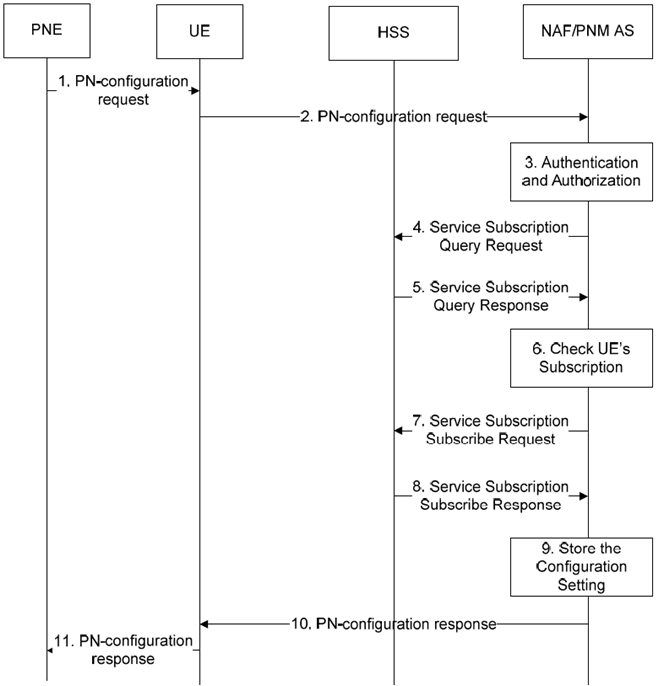
The signalling flow in Figure 5.3.3-1 describes the signalling flow between PNE and NAF/PNM AS through the UE when the PNE wants to configure the PN.
Step 1.
PNE sends a PN-configuration request to the UE contains the public user identity/identities of the UE, and the PN identifier of the PNE to be configured. The relevant parameters for executing the PN redirection application (e.g configuration level and the priority value) may be included. The PN access control list including either the public user identities (if reachable in the IM CN subsystem) and/or the directory number (if reachable in the CS domain) may be included.
Step 2.
UE forwards the PN-configuration request to the NAF/PNM AS informing the PNM AS about the desirable settings of PNE.
Step 3.
Upon receiving this Configuration request message, the NAF/PNM AS authenticates the PN-configuration request according to the TS 33.222. After a successful authentication, the NAF inserts the private user identity of the UE and forwards the request to the PNM AS. The PNM AS authorizes the Configuration request message by comparing the public user identity and the PN UE name with those ones that are registered in the PN by means of the PN-registration procedure.
Step 4.
The NAF/PNM AS sends a Service Subscription Query request to the HSS in order to obtain the service subscription tied to the public user identity received in the PN-configuration request.
Step 5.
The HSS sends a Service Subscription Query response back to the NAF/PNM AS with the service subscription tied to the public user identity.
Step 6.
Upon receiving the Service Subscription Query response, the NAF/PNM AS verifies the PNE service subscription of the public user identity.
Step 7.
The NAF/PNM AS sends the Service Subscription Subscribe request to the HSS.
Step 8.
The HSS sends the Service Subscription Subscribe Response to the NAF/PNM AS.
Step 9.
The NAF/PNM AS stores the configuration settings.
Step 10.
The NAF/PNM AS sends the PN-configuration response to the UE.
Step 11.
UE forwards the PN-configuration response to the PNE.
5.4 PN-deconfiguration p. 18
5.4.1 General p. 18
The PN-deconfiguration procedure enables the PN-user to deconfigure the default UE of a PN. Corresponding to the configuration procedure described in subclause 5.3, the PN-deconfiguration can be done in three levels in IM CN subsystem and two levels in CS domain.
The following subclauses describe the PN-deconfiguration procedure in the IM CN subsystem.
5.4.2 PN-deconfiguration procedure in the IM CN subsystem p. 18
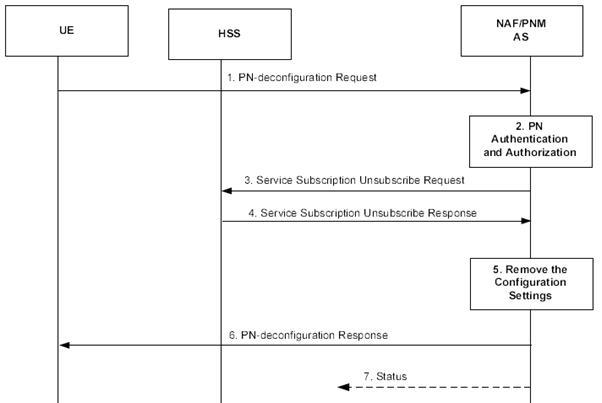
The signalling flow in Figure 5.4.2-1 describes the signal flow between UE and NAF/PNM AS when the UE wants to deconfigure the PN. The messaging shall only take place after a successful bootstrapping procedure (as described in TS 33.220) in which case the bootstrapped security association has been established before Step 1.
Step 1.
In order to remove its configuration settings for the PN UE redirection applications from the PN, a UE sends a Deconfiguration request message to the PNM AS containing the public user identity/identities of the UEs to be deconfigured. Additionally, other relevant parameters for executing the PN UE redirection application such as the configuration level and the priority value can be included.
Step 2.
Upon receiving the PN-deconfiguration request, the NAF/PNM AS authenticates the PN-deconfiguration Request according to the TS 33.222. After a successful authentication, the NAF inserts the private user identity of the UE and forwards it to the PNM AS. The PNM AS authorizes the PN-deconfiguration request by comparing the public user identity with those ones that are registered in the PN by means of the PN-registration procedure.
Step 3.
The PNM AS sends the Unsubscribe request to the HSS.
Step 4.
The HSS sends the Unsubscribe response to the PNM AS.
Step 5.
The PNM AS removes the stored configuration setting.
Step 6.
The PNM AS sends the PN-deconfiguration response to the UE.
Step 7.
If the UE ties to this specific public user identity registered as the only default UE, then the NAF/PNM AS sends the Status message request to these UEs of the PN to inform this change.
5.5 PN-query p. 19
5.5.1 General p. 19
Figure 5.5.2-1 shows a successful PN-query procedure that is used by the PN-users to enquiry their PN settings information which is stored in the PNM AS after performing the PN-registration and PN-configuration procedures.
5.5.2 PN query procedure p. 19
The PN setting information belonging to a PN-user can be categorized into:
- information about the registered public user identities,
- settings for PN UE redirection, such as the default UEs, service level settings and redirection priority.
- settings for the PN access control, such as a PN access control list.
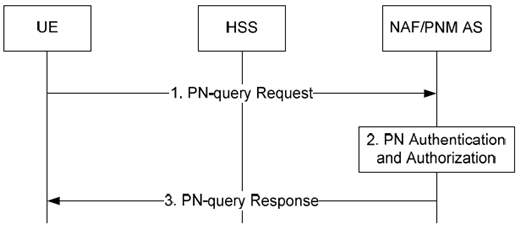
The signalling flow in Figure 5.5.2-1 describes the signal flow between UE and NAF/PNM AS when the UE wants to query the PN settings. The procedure shall only take place after a successful bootstrapping procedure (as described in TS 33.220) in which case the bootstrapped security association has been established before Step 1.
Step 1.
UE sends a PNquery request to the NAF/PNM AS in order to obtain the PN setting information classified above for the PNM applications by including the public user identity/identities of the UEs.
Step 2.
Upon receiving the PN-query request, the NAF/PNM AS authenticates the PN-query request according to the TS 33.222. After a successful authentication, the NAF/PNM AS inserts the private user identity associated with the public user identity/identities of the UE and forwards the message to the NAF/PNM AS. The NAF/PNM AS authorizes the PN-query request by comparing the public user identity with those ones that are registered in the PN by means of the PN-registration procedure.
Step 3.
The NAF/PNM AS sends the PNquery response message to the UE containing the PN settings information for the PNM applications as asked by the UE.