Content for TR 33.745 Word version: 19.0.0
1 Scope
2 References
3 Definitions of terms, symbols and abbreviations
3.1 Terms
3.2 Symbols
3.3 Abbreviations
4 Security Architecture and Assumptions
...
...
1 Scope p. 8
The present document studies the potential security enhancements for supporting 5G NR Femto. More specifically, the study investigates potential security enhancements in the following areas:
- With the gap analysis, study the potential updates or enhancements needed for 5G NR Femto over TS 33.320.
- Study the security impacts for interworking between CAG and CSG cells.
- Study the security impacts of enabling provisioning of subscribers allowed to access 5G NR Femto cells and how to manage 5G NR Femto access control by the Closed Access Group (CAG) owner or an authorized administrator.
2 References p. 8
The following documents contain provisions which, through reference in this text, constitute provisions of the present document.
- References are either specific (identified by date of publication, edition number, version number, etc.) or non-specific.
- For a specific reference, subsequent revisions do not apply.
- For a non-specific reference, the latest version applies. In the case of a reference to a 3GPP document (including a GSM document), a non-specific reference implicitly refers to the latest version of that document in the same Release as the present document.
[1]
TR 21.905: "Vocabulary for 3GPP Specifications".
[2]
TS 33.320: "Security of Home Node B (HNB) / Home evolved Node B (HeNB)".
[3]
TR 23.700-45: "Study on system aspects of 5G NR Femto"
[4]
TS 23.501: "System Architecture for the 5G System".
[5]
TS 22.220: "Service requirements for Home Node B (HNB) and Home eNode B (HeNB)".
[6]
TS 38.799: "Study on Additional Topological Enhancements for NR"
[7]
TS 24.501: "Non-Access-Stratum (NAS) protocol for 5G System (5GS)"
[8]
TS 29.503: "5G System; Unified Data Management Services".
[9]
TS 33.210: "3G security; Network Domain Security (NDS); IP network layer security".
[10]
TS 33.501: "Security architecture and procedures for 5G system".
[11]
TS 23.502: "Procedures for the 5G System".
[12]
TS 38.413: "NG-RAN; NG Application Protocol (NGAP)".
3 Definitions of terms, symbols and abbreviations p. 8
3.1 Terms p. 8
For the purposes of the present document, the terms given in TR 21.905, TR 23.700-45 and the following apply. A term defined in the present document takes precedence over the definition of the same term, if any, in TR 21.905.
CAG:
as defined in TS 23.501.
CSG:
as defined in TS 22.220.
Hosting Party:
as defined in TS 22.220.
NR Femto Hosting Party:
"H(e)NB Hosting Party" defined in TS 22.220.
CAG Owner:
NR Femto Hosting Party.
3.2 Symbols p. 9
Void
3.3 Abbreviations p. 9
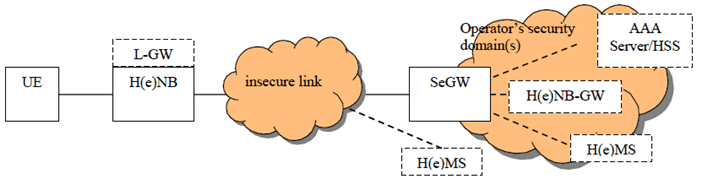
4 Security Architecture and Assumptions p. 9
The following architecture and security assumptions are applied to the present document:
- The architectural assumptions and principles captured in TR 23.700-45 are used as architecture assumptions in this study.
- The security architecture defined in clause 4.1 in TS 33.320 can be reused as basis for this study. Whether all components are all necessary and what are the function names in 5G will be studied in the present document.