Content for TS 33.535 Word version: 18.4.0
4.6 Roaming
4.6.1 AKMA roaming requirements
4.7 Use of Authentication Proxy (AP)
4.7.1 Architecture of using AP
4.7.2 AP-AS reference point
4.7.3 Example of using AP for TLS tunnels
...
...
4.6 Roaming |R18| p. 12
4.6.1 AKMA roaming requirements p. 12
Requirements for AKMA roaming are:
- The roaming subscriber shall be able to utilize the AKMA feature provided by the home network.
- The home network shall be able to control whether its subscriber is authorized to use the service in the visited network.
4.7 Use of Authentication Proxy (AP) |R18| p. 12
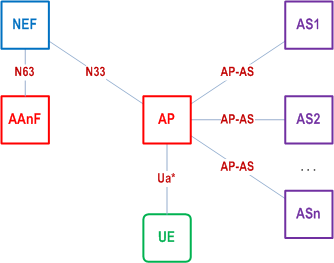
4.7.1 Architecture of using AP p. 12
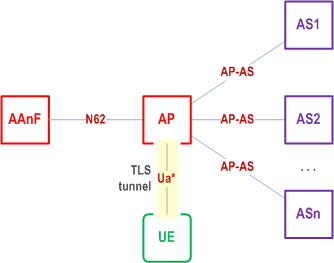
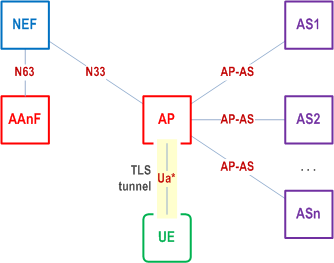
An Authentication Proxy (AP) is a proxy which takes the role of an AF and delegates a group of Application Servers (ASs). It may reside between the UE and the AS as depicted in the figures below. The AP helps the ASs behind the AP to execute AKMA procedures to save the consumption of signalling resources and AAnF computing resources. It may also relieve the AS of security tasks. The use of an AP is fully compatible with the architecture specified in the present document.
The AP can assure the ASs that the request is coming from an authorized subscriber of the MNO.
If the Ua* is HTTP based, the UE is configured with the FQDN of AS, and the AP is a reverse proxy to handle the communication between the UE and the AS. The AP takes the role of an AF. The AKMA Application Key (i.e. KAF), which is utilized between the UE and the AP, is derived based on the FQDN of the AS.
If the Ua* is not HTTP based, it is left to implementation, e.g., how the AP identifies the traffic towards corresponding AS may be pre-configured in the AP by the operator who deploys the AP.
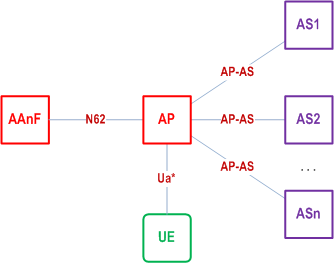
4.7.2 AP-AS reference point p. 13
The HTTP protocol is run over the AP-AS reference point.
Confidentiality and integrity protection can be provided for the reference point between the AP and the AS using NDS/IP mechanisms as specified in TS 33.210. For traffic between different security domains, the Za reference point shall be operated. For traffic inside a security domain, it is up to the operator to decide whether to deploy the Zb reference point.
4.7.3 Example of using AP for TLS tunnels p. 13
When the TLS based protocol is used as Ua* profile, the AP can be used to handle the TLS security relation with the UE and relieves the AS of this task. When an HTTPS request is destined towards an AS behind an AP, the AP terminates the TLS tunnel and performs UE authentication. The AP proxies the HTTP requests received from UE to one or many application servers. The AP may add an assertion of identity of the subscriber for use by the AS, when the AP forwards the request from the UE to the AS.