Content for TS 33.533 Word version: 18.3.0
6.4 Security for communication of Ranging/SL positioning control
6.4.1 General
6.4.2 Security requirements
6.4.3 Security procedures for unicast direct communication over RSPP between the UEs
6.4.3.1 General
6.4.3.2 Unicast direct communication for Ranging/SL Positioning services provided application
6.4.3.3 Unicast direct communication for Ranging/SL Positioning services provided by network
6.4.4 Security procedure for broadcast/groupcast communication over RSPP
6.4.4.1 General
6.4.4.2 Security flows for broadcast/groupcast communication
6.4.4.3 Protection of messages between UEs
6.4.4.3.1 Message processing in the sending UE
6.4.4.3.2 Protected message processing in the receiving UE
6.4.4.4 Key hierarchy for broadcast/groupcast protection communication over RSPP
6.4.5 Security procedure for communication between the UE and LMF
...
...
6.4 Security for communication of Ranging/SL positioning control p. 14
6.4.1 General p. 14
Ranging/SL Positioning control is defined in TS 23.586, which is supported by the Ranging/SL Positioning layer above the AS layer. The Ranging/SL Positioning layer provides the support of Ranging/SL Positioning Protocol (RSPP) between the UEs and between the UE and LMF for Ranging/SL Positioning.
Ranging/SL Positioning control over RSPP is performed on SR5 reference point between UEs. PC5-U is used as the transport layer for RSPP as specified in clause 5.3.2 of TS 23.586. Depending on type of the UE (V2X capable or 5G ProSe capable), V2X Communication procedures defined in TS 23.287 or 5G ProSe Direct Communication procedures defined in TS 23.304 are used for RSPP transport between UEs.
Ranging/SL Positioning control over the protocol between the UE and LMF is specified in clauses 6.20 of TS 23.273.
6.4.2 Security requirements p. 14
The 5G system shall support mutually authentication between the UEs during unicast direct communication establishment for Ranging/SL Positioning control over RSPP.
The 5G system shall support integrity, confidentiality and anti-replay protection for the information transferred during unicast direct communication for Ranging/SL Positioning control over RSPP.
The 5G system shall support cryptographic separation for each SR5 interface and for each peer UE during unicast direct communication for Ranging/SL Positioning control over RSPP.
The 5G system shall support integrity, confidentiality and anti-replay protection for the information transferred during unicast communication for Ranging/SL Positioning control over the protocol between the UE and LMF.
The 5G system shall support a means to configure PC5 security policies to the UE for Ranging/SL positioning services.
SR5 signalling integrity protection policy is configured to "REQUIRED" for Ranging/SL positioning services.
The 5G system shall support a means to provide confidentiality, integrity and anti-replay protection of SL positioning broadcast/groupcast signalling.
The 5G system shall provide a means to mitigate trackability and linkability attacks of the UE during SL Positioning broadcast/ groupcast signalling procedures.
6.4.3 Security procedures for unicast direct communication over RSPP between the UEs p. 15
6.4.3.1 General p. 15
Ranging/SL Positioning services could be provided by an application provider (i.e. the services requested by a Ranging/SL positioning application server) or by a network operator (i.e. the services requested by a 5GC NF). For Ranging/SL Positioning services provided by application providers, long-term credentials provided by applications are assumed available on the UE. For Ranging/SL Positioning services provided by network operators (e.g. 5GC-MO-LR and 5GC-MT-LR services using SL positioning as defined in TS 23.586 and TS 23.273), there are no long-term credentials provided by applications on the UE (e.g. Located UE). The security procedures for unicast communication for Ranging/SL Positioning services provided by application and for Ranging/SL Positioning services provided by network are specified separately in subclauses 6.4.3.2 and 6.4.3.3.
6.4.3.2 Unicast direct communication for Ranging/SL Positioning services provided application p. 15
If long-term credentials provided by application are available on the UE, the security procedures defined for V2X unicast mode communication in clause 5.3 of TS 33.536 are reused on V2X capable UEs. The security procedures defined for 5G ProSe unicast mode Direct Communication in clause 6.2.3 of TS 33.503 are reused on ProSe capable UEs.
6.4.3.3 Unicast direct communication for Ranging/SL Positioning services provided by network p. 15
For Ranging/SL Positioning services provided by network operators, the network shall support key provisioning and management for unicast direct communication. The security procedures defined for 5G ProSe UE-to-Network Relay communication in clause 6.3.3.2 of TS 33.503 are reused with the following modifications:
- The SLPKMF instead of 5G PKMF is used to generate and provision the key materials for secure unicast direct communication of Ranging/SL Positioning services.
- UE SLP Key Request/Response are used instead of ProSe Remote User Key Request/Response.
- Ranging/SL Positioning Application Identifier is used instead of RSC.
- SLPK and SLPK ID are used instead of UP-PRUK and UP-PRUK ID.
- SLP Key Request/Response are used instead of Key Request/Response.
- KSLP is used instead of KNRP.
- KDF of KSLP as defined in clause A.2 uses Ranging/SL Positioning Application Identifier as input instead of RSC.
6.4.4 Security procedure for broadcast/groupcast communication over RSPP p. 15
6.4.4.1 General p. 15
This clause describes the security mechanism for broadcast/groupcast communication over RSPP. The RSPP messages for broadcast/groupcast communication are protected at the RSPP layer.
6.4.4.2 Security flows for broadcast/groupcast communication p. 16
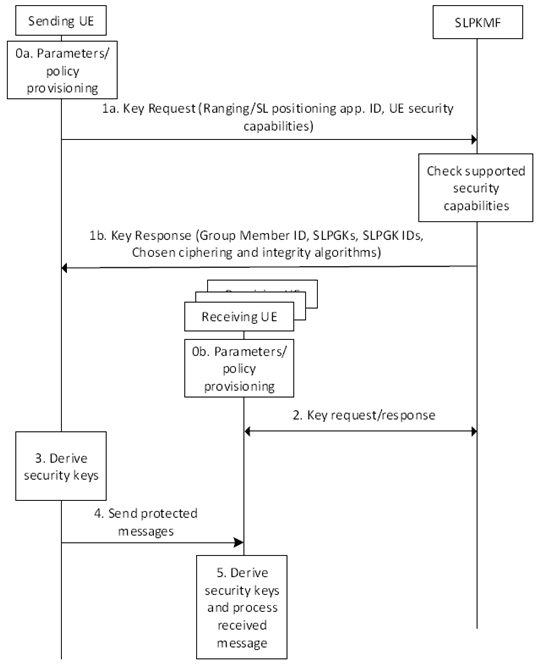
Figure 6.4.4.2-1: Security flows for broadcast/groupcast communication
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
Step 0a and 0b.
Both sending and receiving UEs shall be provisioned with the parameters/policy for Ranging/SL positioning service as specified in clause 5.1 of TS 23.586.
Step 1a.
The sending UE shall establish a secure connection with the Sidelink Positioning Key Management Function (SLPKMF) based on the security procedures specified in clause 5.2.5 of TS 33.503. The sending UE sends a Key Request message to Sidelink Positioning Key Management Function (SLPKMF) including the Ranging/SL positioning application identifier provisioned in step 0a, and UE security capabilities.
Step 1b.
The SLPKMF shall reply with the Key Response message containing the Sidelink Positioning Group Key (SLPGK), the Sidelink Positioning Group Key ID (SLPGK ID), the validity time, and the chosen ciphering and integrity algorithms. The SLPKMF may be locally configured with the UE's authorization information. Otherwise, the SLPKMF interacts with the UDM of the UE to retrieve the UE's authorization information. The chosen ciphering and integrity algorithms are determined by SLPKMF based on the received UE security capabilities in step 1a. The Key Response message may include multiple SLPGK and SLPGK ID pairs with different validity times. Group member ID shall be assigned by the SLPKMF which is included in the Key Response message. As an alternative, the sending UE may generate a Group member ID randomly.
Step 2.
The receiving UE shall perform a Key Request procedure to get security materials from the SLPKMF as described in step 1. This may happen any time before step 5.
Step 3.
The sending UE shall derive the Sidelink Positioning Traffic Key (SLPTK) from SLPGK using Group member ID, and SLPTK ID as specified in Annex A.3 of present document. SLPTK ID is a counter set to a unique value in the sending UE that has not been previously used together with the same SLPGK and the associated SLPGK ID. The UE shall use a new SLPGK and SLPGK ID pair based on step 1 before the SLPTK ID wraps around. The UE shall calculate the Sidelink Positioning Encryption Key (SLPEK) and Sidelink Positioning Integrity Key (SLPIK) from SLPTK using the chosen ciphering and integrity algorithms, respectively as specified in Annex A.4 of present document.
Step 4.
The sending UE shall protect the message as described in clause 6.4.4.3.1 and send the message.
Step 5.
Upon receiving the message matching the SLPGK ID, the receiving UE shall calculate SLPTK, SLPEK and SLPIK if it has not calculated them. The receiving UE derives security keys as in step 3 using the SLPGK ID, SLPTK ID and Group member ID (if it is included) in the received message. Then, the UE shall decrypt the message and verifies the integrity of the message as described in clause 6.4.4.3.2.
6.4.4.3 Protection of messages between UEs p. 17
6.4.4.3.1 Message processing in the sending UE p. 17
The UE sending a message shall construct the message as follows:
- Form RSPP message header that contains Group member ID, SLPGK ID, SLPTK ID, and a counter. Then, append the Payload to it as illustrated in Figure 6.4.4.3.1-1. The counter is used in combination with the selected ciphering algorithm and integrity algorithm.
- If the chosen integrity algorithm is not the NULL algorithm, calculate MAC of the message header and the Payload based on the chosen integrity algorithm. If the chosen algorithm is the NULL algorithm, then the sending UE shall set the MAC to a 32-bit random string or all zeros in the message header. The use and mode of operation of the chosen integrity algorithm are specified in Annex D of TS 33.501.
- If the chosen ciphering algorithm is not the NULL algorithm, encrypt the Payload and MAC based on the chosen ciphering algorithm. The use and mode of operation of the chosen ciphering algorithm are specified in Annex D of TS 33.501.

Figure 6.4.4.3.1-1: RSPP message format for Sidelink Positioning broadcast/groupcast communication
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
6.4.4.3.2 Protected message processing in the receiving UE p. 17
The UE receiving a message shall do the following steps:
- If the chosen ciphering algorithm is not the NULL algorithm, undo confidentiality protection based on the chosen ciphering algorithm.
- If the chosen integrity algorithm is not the NULL algorithm, verify the integrity of the received message by checking MAC based on the chosen integrity algorithm. The message with MAC part filled with all zeroes is discarded.
6.4.4.4 Key hierarchy for broadcast/groupcast protection communication over RSPP p. 18
The key hierarchy for broadcast/groupcast communication over RSPP follows the key hierarchy for one-to-many ProSe direct communication as specified in TS 33.303. The different layers of keys (see Figure 6.4.4.4-1) are the following:
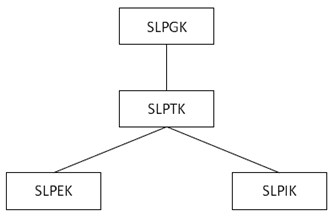
Figure 6.4.4.4-1: Key hierarchy for broadcast/groupcast communication over RSPP
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
- SLPGK: SL Positioning Group Key is a 256-bit root key specific to a Ranging/SL positioning application (for broadcast) or group (for groupcast) provisioned with an expiry time. Each SLPGK has an SLPGK ID to identify it. This allows several SLPGKs to be held simultaneously for one Ranging/SL positioning application (for broadcast) or Ranging/SL positioning group (for groupcast). SLPGK may either be provisioned by the SLPKMF to the UE or be derived by the UE from locally configured long-term credentials.
- SLPTK: SL Positioning Traffic Key is a 256-bit intermediate key derived by the UE from SLPGK. It is unique per UE to ensure that each UE generates unique SLPTKs for protecting the messages it sends. Each SLPTK has a 16-bit SLPTK ID to identify it. SLPTK ID is a counter in the UE set to a unique value that has not been previously used together with the same SLPGK and associated SLPGK ID. Every time a new SLPTK needs to be derived, the SLPTK ID counter is incremented.
- SLPEK and SLPIK: The SL Positioning Encryption Key (SLPEK) and SL Positioning Integrity Key (SLPIK) are derived by the UE from SLPTK and used as broadcast/groupcast keys to protect the integrity and confidentiality of RSPP messages for Sidelink Positioning broadcast/groupcast communication respectively.
6.4.5 Security procedure for communication between the UE and LMF p. 18
The communication for Ranging/SL Positioning control between the UE and LMF is protected by using NAS security context created for the UE.