Content for TS 33.401 Word version: 18.1.0
1…
4
5…
6…
6.2…
7…
7.2.5…
7.2.8
7.2.9…
7.3…
8…
9…
10…
11…
15…
A…
B…
C…
C.1.6
C.2…
C.2.7
C.2.8
C.3…
C.4.7
D…
E…
E.2…
E.3…
F…
G…
H…
I…
K…
7.2.8 Key handling in handover p. 44
7.2.8.1 General p. 44
7.2.8.1.1 Access stratum p. 44
The general principle of key handling at handovers is depicted in Figure 7.2.8.1-1.
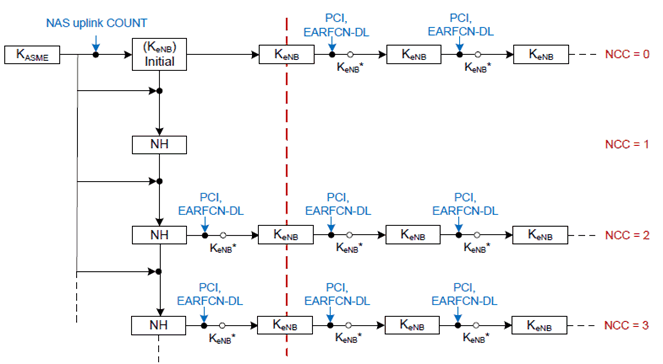
The following is an outline of the key handling model to clarify the intended structure of the key derivations. The detailed specification is provided in clauses 7.2.8.3 and 7.2.8.4.
Whenever an initial AS security context needs to be established between UE and eNB, MME and the UE shall derive a KeNB and a Next Hop parameter (NH). The KeNB and the NH are derived from the KASME. A NH Chaining Counter (NCC) is associated with each KeNB and NH parameter. Every KeNB is associated with the NCC corresponding to the NH value from which it was derived. At initial setup, the KeNB is derived directly from KASME, and is then considered to be associated with a virtual NH parameter with NCC value equal to zero. At initial setup, the derived NH value is associated with the NCC value one.
Whether the MME sends the KeNB key or the {NH, NCC} pair to the serving eNB is described in detail in clauses 7.2.8.3 and 7.2.8.4. The MME shall not send the NH value to eNB at the initial connection setup. The eNB shall initialize the NCC value to zero after receiving S1-AP Initial Context Setup Request message.
The UE and the eNB use the KeNB to secure the communication between each other. On handovers, the basis for the KeNB that will be used between the UE and the target eNB, called KeNB*, is derived from either the currently active KeNB or from the NH parameter. If KeNB* is derived from the currently active KeNB this is referred to as a horizontal key derivation (see Figure 7.2.8.1-1) and if the KeNB* is derived from the NH parameter the derivation is referred to as a vertical key derivation (see Figure 7.2.8.1-1). On handovers with vertical key derivation the NH is further bound to the target PCI and its frequency EARFCN-DL before it is taken into use as the KeNB in the target eNB. On handovers with horizontal key derivation the currently active KeNB is further bound to the target PCI and its frequency EARFCN-DL before it is taken into use as the KeNB in the target eNB.
As NH parameters are only computable by the UE and the MME, it is arranged so that NH parameters are provided to eNBs from the MME in such a way that forward security can be achieved.
7.2.8.1.2 Non access stratum p. 45
A NAS aspect that needs to be considered is possible NAS algorithm change at MME change that could occur at a handover. At an eNB handover with MME relocation, there is the possibility that the source MME and the target MME do not support the same set of NAS algorithms or have different priorities regarding the use of NAS algorithms. In this case, the target MME re-derives the NAS keys from KASME using the NAS algorithm identities as input to the NAS key derivation functions (see clause A.7) and sends NAS SMC. All inputs, in particular the KASME, will be the same in the re-derivation except for the NAS algorithm identity.
In case the target MME decides to use NAS algorithms different from the ones used by the source MME, a NAS SMC including eKSI (new or current value depending on whether AKA was run or not) shall be sent from the MME to the UE.
This NAS Key and algorithm handling also applies to other MME changes e.g. TAU with MME changes.
7.2.8.2 Void
7.2.8.3 Key derivations for context modification procedure p. 45
As outlined in clause 7.2.8.1, whenever a fresh KeNB is calculated from the KASME (as described in Annex A.3), the MME shall transfer the KeNB to the serving eNB in a message modifying the security context in the eNB. The MME and the UE shall also compute the NH parameter from the KASME and the fresh KeNB as described in Annex A.4 according to the rules in clause 7.2.9.2. An NCC value 1 is associated with the NH parameter derived from the fresh KeNB and NCC value 0 with the KeNB. The UE shall compute KeNB and NH in the same way as the MME. From the newly computed KeNB, the eNB and the UE shall compute the temporary KeNB* and then the final KeNB from that KeNB* as described in clause 7.2.9.2.
7.2.8.4 Key derivations during handovers p. 45
7.2.8.4.1 Intra-eNB Handover p. 45
When the eNB decides to perform an intra-eNB handover it shall derive KeNB* as in Annex A.5 using target PCI, its frequency EARFCN-DL, and either NH or the current KeNB depending on the following criteria: the eNB shall use the NH for deriving KeNB* if an unused {NH, NCC} pair is available in the eNB (this is referred to as a vertical key derivation), otherwise if no unused {NH, NCC} pair is available in the eNB, the eNB shall derive KeNB* from the current KeNB (this is referred to as a horizontal key derivation).
The eNB shall use the KeNB* as the KeNB after handover. The eNB shall send the NCC used for KeNB* derivation to UE in HO Command message.
7.2.8.4.2 X2-handover p. 46
As in intra-eNB handovers, for X2 handovers the source eNB shall perform a vertical key derivation in case it has an unused {NH, NCC} pair. The source eNB shall first compute KeNB* from target PCI, its frequency EARFCN-DL, and either from currently active KeNB in case of horizontal key derivation or from the NH in case of vertical key derivation as described in Annex A.5.
Next the source eNB shall forward the {KeNB*, NCC} pair to the target eNB. The target eNB shall use the received KeNB* directly as KeNB to be used with the UE. The target eNB shall associate the NCC value received from source eNB with the KeNB. The target eNB shall include the received NCC into the prepared HO Command message, which is sent back to the source eNB in a transparent container and forwarded to the UE by source eNB.
When the target eNB has completed the handover signaling with the UE, it shall send a S1 PATH SWITCH REQUEST to the MME. Upon reception of the S1 PATH SWITCH REQUEST, the MME shall increase its locally kept NCC value by one and compute a new fresh NH by using the KASME and its locally kept NH value as input to the function defined in Annex A.4. The MME shall then send the newly computed {NH, NCC} pair to the target eNB in the S1 PATH SWITCH REQUEST ACKNOWLEDGE message. The target eNB shall store the received {NH, NCC} pair for further handovers and remove other existing unused stored {NH, NCC} pairs if any.
7.2.8.4.3 S1-Handover p. 46
Upon reception of the HANDOVER REQUIRED message the source MME shall increase its locally kept NCC value by one and compute a fresh NH from its stored data using the function defined in Annex A.4. The source MME shall store that fresh pair and send it to the target MME in the S10 FORWARD RELOCATION REQUEST message. The S10 FORWARD RELOCATION REQUEST message shall in addition contain the KASME that is currently used to compute {NH, NCC} pairs and its corresponding eKSI.
The target MME shall store locally the {NH, NCC} pair received from the source MME.
The target MME shall then send the received {NH, NCC} pair to the target eNB within the S1 HANDOVER REQUEST.
Upon receipt of the S1 HANDOVER REQUEST from the target MME, the target eNB shall compute the KeNB to be used with the UE by performing the key derivation defined in Annex A.5 with the fresh{NH, NCC} pair in the S1 HANDOVER REQUEST and the target PCI and its frequency EARFCN-DL. The target eNB shall associate the NCC value received from MME with the KeNB. The target eNB shall include the NCC value from the received {NH, NCC} pair into the HO Command to the UE and remove any existing unused stored {NH, NCC} pairs.
For S1-handover, the source eNB shall include AS algorithms used in the source cell (ciphering and integrity algorithms) in the source to target transparent container that shall be sent to the target eNB. The AS algorithms used by in the source cell are provided to the target eNB so that it can decipher and integrity verify the RRCReestablishmentComplete message on SRB1 in the potential RRCConnectionRe-establishment procedure.
7.2.8.4.4 UE handling p. 47
The UE behaviour is the same regardless if the handover is S1, X2 or intra-eNB. The UE behaviour is also same in case of Conditional Handover, as specified in TS 36.300, i.e., the UE shall use the parameters of the selected target cell in KeNB* derivations.
If the NCC value the UE received in the HO Command message from target eNB via source eNB is equal to the NCC value associated with the currently active KeNB, the UE shall derive the KeNB* from the currently active KeNB and the target PCI and its frequency EARFCN-DL using the function defined in Annex A.5.
If the UE received an NCC value that was different from the NCC associated with the currently active KeNB, the UE shall first synchronize the locally kept NH parameter by computing the function defined in Annex A.4 iteratively (and increasing the NCC value until it matches the NCC value received from the source eNB via the HO command message. When the NCC values match, the UE shall compute the KeNB* from the synchronized NH parameter and the target PCI and its frequency EARFCN-DL using the function defined in Annex A.5.
The UE shall use the KeNB* as the KeNB when communicating with the target eNB.