Content for TS 33.401 Word version: 18.1.0
1…
4
5…
6…
6.2…
7…
7.2.5…
7.2.8
7.2.9…
7.3…
8…
9…
10…
11…
15…
A…
B…
C…
C.1.6
C.2…
C.2.7
C.2.8
C.3…
C.4.7
D…
E…
E.2…
E.3…
F…
G…
H…
I…
K…
4 Overview of Security Architecture p. 17
Figure 4-1 gives an overview of the complete security architecture.
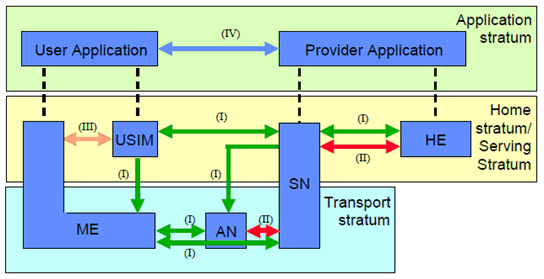
Five security feature groups are defined. Each of these feature groups meets certain threats and accomplishes certain security objectives:
- Network access security (I): the set of security features that provide users with secure access to services, and which in particular protect against attacks on the (radio) access link.
- Network domain security (II): the set of security features that enable nodes to securely exchange signalling data, user data (between AN and SN and within AN), and protect against attacks on the wireline network.
- User domain security (III): the set of security features that secure access to mobile stations.
- Application domain security (IV): the set of security features that enable applications in the user and in the provider domain to securely exchange messages.
- Visibility and configurability of security (V): the set of features that enables the user to inform himself whether a security feature is in operation or not and whether the use and provision of services should depend on the security feature.