TR 33.905
Recommendations for Trusted Open Platforms
V18.0.0 (PDF)
2024/03 17 p.
V17.0.0
2022/03 17 p.
V16.0.0
2020/06 17 p.
V15.0.0
2018/06 17 p.
V14.0.0
2017/03 17 p.
V13.0.0
2016/01 17 p.
V12.0.0
2014/09 17 p.
V11.0.0
2012/09 17 p.
V10.0.0
2011/04 17 p.
V9.0.0
2009/12 17 p.
V8.0.0
2008/12 17 p.
V7.0.0
2007/03 17 p.
- Rapporteur:
- Dr. Holtmanns, Silke
Nokia Networks Oy
Content for TR 33.905 Word version: 18.0.0
0 Introduction p. 4
Securing the storage, processing, and input and output of sensitive data on an open platform are of critical importance. Also, isolation of applications that are managing (U)SIMs and (U)SIM readers, EAP-SIM and EAP-AKA protocols, and SAP applications from untrusted applications is imperative. Protecting the interface between the trusted open platform and the UICC is also of critical importance.
Therefore, it is very much desirable that the Open Platform must have secure authentication and authorization mechanisms to protect against eavesdropping, and malicious modification of sensitive data and operator applications residing on the Open Platform.
Consequently, for the diverse 3GPP usage models of the Open Platform, such as the ones described in TS 33.234, appropriate trust recommendations need to be outlined to counteract the threats. This document describes trust recommendations for the usage models described in 3GPP.
1 Scope p. 5
This technical report investigates relevant trust standards and technologies, both existing as well as the ones that are work-in-progress. It develops the recommendations for trusted open platforms for delivery of new applications and services to open platforms.
2 References p. 5
The following documents contain provisions, which, through reference in this text, constitute provisions of the present document.
- References are either specific (identified by date of publication, edition number, version number, etc.) or non-specific.
- For a specific reference, subsequent revisions do not apply.
- For a non-specific reference, the latest version applies. In the case of a reference to a 3GPP document (including a GSM document), a non-specific reference implicitly refers to the latest version of that document in the same Release as the present document.
[1]
TS 33.220: "3rd Generation Partnership Project; Technical Specification Group Services and System Aspects; Generic Authentication Architecture (GAA); Generic Bootstrapping Architecture".
[2]
TS 33.234: "3rd Generation Partnership Project; Technical Specification Group Service and System Aspects; 3G Security; Wireless Local Area Network (WLAN) interworking security".
[3]
TR 21.905: "Vocabulary for 3GPP Specifications".
3 Definitions, symbols and abbreviations p. 5
3.1 Definitions p. 5
For the purposes of the present document, the following terms and definitions given in TR 21.905 and the following apply.
Application Specific Credentials:
These are credentials e.g. keys, identifiers and related data, that are application specific and need to be protected against malicious access and only to be released to authorized applications acting as a Orpheus client. The application specific credentials might be stored or generated in the UICC or in the Persephone server. The application specific credentials can be generated from a master secret, randomly or be set by the user.
Charon Fine Grained Access Control:
The access control policy in the terminal controls which authorized applications in the terminal have access to certain application specific application credentials, i.e., only certain application in the terminal is allowed to application specific credentials that can be used with certain applications.
Coarse-grained access control policy:
In GAA context, the access control policy in the terminal controls whether an application is authorized to have access to NAF specific GAA credentials. Therefore, the application has access to all possible NAF specific GAA credentials. The coarse-grained access control policy may be stored in the UICC or in the ME.
Credential Generator:
The credential generator generates the application specific credentials and the master secret. It might also generate directly the application specific credentials without a master secret. The Credential Generator might be part of an application or co-hosted together with an application.
Fine-grained access control policy:
In GAA context, the access control policy in the terminal controls which authorized applications in the terminal have access to certain NAF specific GAA credentials, i.e., only certain application in the terminal is allowed to GAA credentials that can be used with certain NAFs. The fine-grained access control policy may be stored in the UICC or in the ME.
GAA Client:
A software component in the terminal that communicates with a NAF in the network. The GAA client uses GAA credentials to authenticate and possibly otherwise secure the communication with the NAF in the network. GAA client uses the API provided by the GAA Server to gain access to the GAA credentials.
GAA Credentials:
Consists of a bootstrapping transaction identifier (B-TID), one or two NAF specific keys, and a lifetime of those keys. If the terminal is equipped with GBA_U unaware UICC, then there is only one key (the GBA_ME NAF specific key) that derived by the GAA Server from the GAA master secret and given to the GAA client for further usage with the NAF. If the terminal is equipped with GBA_U aware UICC, then there are two keys that are derived from the GAA master secret in the UICC: one key (Ks_int_NAF) that stays and is used in the UICC, and one that is given to the ME and is used in the ME (Ks_ext_NAF similar to the GBA_U unaware key).
GAA Master Secret:
GAA master secret Ks [1] is established during the bootstrapping session between the terminal (i.e., GAA Server for GBA_ME and UICC for GBA_U) and the BSF. The GAA master secret is used as a key to derive further NAF specific keys that can be used between the GAA clients and the NAFs. If the terminal is equipped with GBA_U unaware UICC, then the GAA Master secret is stored in the GAA server and GBA_ME is used. If the terminal is equipped with GBA_U aware UICC and GBA_U is used, then the GAA Master Secret is stored in the UICC.
GAA Master Secret stored in the GAA server corresponds to GAA Master Secret established with a terminal equipped with GBA_U unaware UICC (GBA_ME procedure used).
GAA Server:
The software component in the terminal responsible for communicating with the SIM/USIM/ISIM application in the UICC, and with the BSF during bootstrapping procedure. The GAA server also functions as a public API towards the GAA clients in the terminal.
Master Secret:
The Master Secret is a master secret that servers as a basis for later key derivations. The Master Secret is established between the terminal (i.e., Persephone Server) and the network. The master secret is used as a key to derive further application specific credentials that can be used between the Orpheus clients and the application. Not every application derives its credentials from a master secret.
Orpheus Client:
A software component in the terminal that communicates with an application in the network. The Orpheus client application specific credentials to perform security functionalities. Orpheus Client uses the API provided by the Persephone Server to gain access to the Application Specific Credentials.
Persephone Server:
The software component in the terminal responsible for communicating with the SIM/USIM/ISIM application in the UICC, and with external entities for possible key generation processes. The Persephone server also functions as a public API towards the Orpheus Clients in the terminal.
Styx Coarse Grained Access Control:
The access control policy in the terminal controls whether an application is authorized to have access to application specific application credentials. Therefore, the application has access to all possible application specific credentials.
3.2 Abbreviations p. 6
4 Recommendations for trusted open platforms in 3GPP Release 7 p. 7
4.1 Recommendations from the Generic Bootstrapping Architecture p. 7
4.1.1 Study of GBA in open trusted platforms p. 7
Figure 4-1 depicts the GAA related functionalities in the terminal. In relation to the GAA architecture, the GAA server communicates with the BSF server over Ub reference point, and with the UICC through the relevant device drivers, for example. The GAA client communicates over the network with a NAF server and the GAA server to obtain the NAF specific GAA credentials. When a NAF server requests a GAA client to authenticate itself with GAA credentials, the client communicates with the GAA server for GAA credentials specific to that NAF.
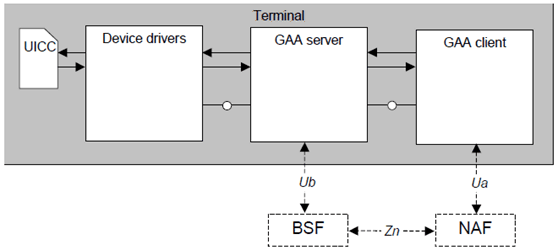
The inherent feature of open platforms is that new applications can be installed to the terminal. In relation to GAA, this poses a security threat when a malicious application is installed in a type of terminal that does not protect GAA related functionalities. The GAA related security threats are as follows:
The recommendations in Table 4-1 can be divided in to three groups the following way:
- A malicious application can access the UICC directly and therefore can function as a GAA server, which can then communicate with both the UICC and the BSF, and hence, establish the GAA master secret.
- The malicious application can access the GAA server private data, and gain access to the GAA master secret stored in the GBA_ME case, in the GAA server.
- The malicious application can access the GAA server API, and obtain NAF specific GAA credentials by requesting them from the GAA server.
| ID | Recommandations | Comments |
|---|---|---|
| 1 | It is possible for the platform to control access to the UICC. | Only authorized applications should have access to the UICC. Otherwise malicious application can perform the GAA server functionalities, establish the GAA master secret with the BSF server, send out the master secret (in case that the terminal is equipped with GBA_U unaware UICC), and thus generate all the GBA_ME NAF specific keys offline (outside the terminal), send out the received NAF specific key (Ks_ext_NAF) in case that the terminal is equipped with GBA_U aware UICC (online). |
| 2 | It is possible for the platform to restrict the access to GAA master secret of the GAA server. | If the GAA master secret in the GAA server in the case of GBA_ME is not protected, a malicious application can get access to it, send it out from the terminal, and the attacker can generate the GBA_ME NAF specific keys offline (outside the terminal). |
| 3 | It is possible for the platform to control general access in coarse-grained model to the GAA server so that an unauthorized application are not be able to get any NAF specific GAA credentials from the GAA server. | If a malicious application can gain access to the GAA server, it can generate all the NAF specific keys online (in the terminal) in case of GBA_ME and in the case of GBA_U it gains access to Ks_ext_NAF. |
| 4 | It is possible that an application is granted access to the GAA server by the manufacturer, or the operator. | The manufacturer or the operator must make sure that the application that is granted access to the GAA server is not malicious or have security flaws. |
| 5 | It is possible that an application is granted access to the GAA server by the user provided that such access is not prevented by manufacturer or operator policy. (See the next recommendation) | User may grant access to a malicious application simply because the application requests to have access. |
| 6 | In addition to recommendations 3, 4, and 5, it is possible to control the access to certain NAF specific GAA credentials in more fine-grained level, where access to certain NAF specific GAA credentials can be restricted to certain applications only. | This recommendation can protect against malicious applications that try to get access to certain NAF specific GAA credentials. |
| 7 | In addition to recommendation 6, the manufacturer can pre-configure the fine-grained access control policy on the terminal or the operator can pre-configure the fine-grained access control policy on the terminal or UICC. | |
| 8 | In addition to recommendation 6, the operator can update all fine-grained access control policies on the terminal or the UICC. | |
| 9 | In addition to recommendation 6, the user can add new fine-grained access control policies to the terminal or the UICC. | The user may only add and modify user's own policies. The user cannot change policies set by the manufacturer or the operator. |
- Group 1: To provide the basic GAA related security in the terminal, recommendations 1 to 4 must be enforced. The basic GAA security includes controlling access to UICC and to GAA master secret, controlling access to the GAA server, and only the manufacturer or the operator can grant access to the GAA functionality for the application.
- Group 2: If access to GAA functionality for applications can be granted by the user then the recommendation 5 must be enforced.
- Group 3: If more fine-grained access to the GAA functionality is wanted as described above, then recommendations 6 to 8 must be enforced. Recommendation 9 must be enforced if the user can grant access to GAA functionality for an application
- USIM with GBA_U aware UICC
- USIM without GBA_U aware UICC
- ISIM with GBA_U aware UICC
- ISIM without GBA_U aware UICC
- Legacy GBA
4.1.2 Recommendation p. 10
This technical report recommends that only recommendation group 1 in the previous clause is required. As user interaction on security is not desired and may cause breaches in GAA terminal security group 2 should be not be required. Recommendation group 3 is not needed as group 2 was excluded.
4.2 Recommendations from I-WLAN p. 10
The threats and recommendations described in 4.1 are also valid for I-WLAN. In I-WLAN there is a UE functionality split case, this case is also called split terminal. In this case the UICC/SIM card may reside in a 3GPP ME (acting as a (U)SIM "server") and be accessed by a WLAN-UE (acting as the (U)SIM "client") through local link (e.g. Bluetooth, Infrared or USB), and has the following additional requirements from [2]:
The recommendations in Table 4-2 can be divided in to three groups the following way:
- Whenever someone tries to remotely access a (U)SIM some sort of alert shall be sent, e.g. a message shall be displayed informing the user of the attempted access and guiding him to choose "Allow", or "Disallow". The user can then decide whether the access is authorized or not and can opt for allow or disallow the access.
- The UICC holding device shall be responsible for scheduling all (possibly concurrent) accesses to the UICC by itself, and by one additional device connected via the local interface.
- Applications/Data information could be retrieved from (U)SIM, provided that the UICC (or SIM card) is inserted in a 3GPP ME. When the (U)SIM is re-used over local interfaces, further access control on the Applications/Data information shall be applied by the 3GPP ME holding the (U)SIM.
- A malicious application can trigger the UICC and get the (Kc, IK, CK, MSK) from the UICC.
- The malicious application can access the copy of the keys (Kc, IK, CK, MSK) stored in ME.
| ID | Recommandations | Comments |
|---|---|---|
| 1 | It is possible for the platform to control access to the UICC. | Only authorized applications should have access to the UICC. |
| 2 | It is possible for the platform to restrict the access to the keys stored in the 3GPP ME. | If the keys in the 3GPP ME is not protected, a malicious application can get access to it and send it out from the terminal. |
| 3 | It is possible that an application is granted access to the keys in 3GPP ME by the manufacturer, or the operator. | The manufacturer or the operator must make sure that the application that is granted access to the keys in the 3GPP ME is not malicious or have security flaws. |
| 4 | It is possible that an application is granted access to the keys in 3GPP ME by the user provided that such access is not prevented by manufacturer or operator policy. | User may grant access to a malicious application simply because the application requests to have access. The access to the keys stored in 3GPP ME can be restricted to certain applications only. |
| 5 | The manufacturer can pre-configure the access control policy on the terminal or the operator can pre-configure the access control policy on the terminal or UICC. | |
| 6 | The operator can update all access control policies on the terminal or the UICC. | |
| 7 | The user can add new access control policies to the terminal or the UICC. | The user may only add and modify user's own policies. The user cannot change policies set by the manufacturer or the operator. |
- Group 1: To provide the basic security in the terminal, recommendations 1 to 4 must be enforced. The basic security includes controlling access to UICC and the (Kc, IK, CK, MSK) used in I-WLAN, controlling access to the derived secrets, and only the manufacturer or the operator can grant access to the secrets for the application.
- Group 2: If access to keys for applications can be granted by the user then the recommendation 4 must be enforced.
- Group 3: If more fine grained access control is wanted as described above, then recommendations 5 and 6 must be enforced. Recommendation 7 must be enforced if the user can grant access to keys for an application.
4.3 Generalized recommendations p. 12
4.3.1 Study of credential security in open trusted platforms p. 12
The inherent feature of open platforms is that new applications can be installed to the terminal. In relation to shared secret credential management, this poses a security threat when a malicious application is installed in a type of terminal that does not protect the shared secret properly. The security threats are as follows:
The recommendations in Table 4-5 can be divided in to three groups the following way:
- A malicious application can access the UICC directly and therefore can then communicate with both the UICC and a credential generator and hence establish master secrets and application specific credentials.
- The malicious application can access the Persephone server private data, and gain access to the master secret.
- The malicious application can access the Persephone server API, and obtain the application specific credentials by requesting them from the Persephone server.
| ID | Recommandations | Comments |
|---|---|---|
| 1 | It is possible for the platform to control access to the UICC. | Only authorized applications should have access to the UICC. Otherwise malicious application can establish a master secret, depending on storage and access mechanisms having access to application specific credentials or, in case of master secret stored outside the UICC, being able to generate application specific credential offline (outside the terminal). |
| 2 | It is possible for the platform to restrict the access to master secret of the Persephone server. | If the master secret of the Persephone server is not protected, a malicious application can get access to it, send it out from the terminal, and the attacker can generate all the application specific keys offline (outside the terminal). The attack does not apply in case of master secret stored in the UICC. |
| 3 | It is possible for the platform to control general access in coarse-grained model to the Persephone server so that an unauthorized application is not be able to get any application specific credentials from the Persephone server. | If a malicious application can gain access to the Persephone server and the master secret is stored there, then it can generate all the application specific keys online (in the terminal). In case of master secret stored on the UICC the attacker cannot generate application keys derived from the master secret. |
| 4 | It is possible that an application is granted access to the Persephone server by the manufacturer, or the operator. | The manufacturer or the operator must make sure that the application that is granted access to the Persephone server is not malicious or have security flaws. |
| 5 | It is possible that an application is granted access to the Persephone server by the user provided that such access is not prevented by manufacturer or operator policy. (See the next recommendation) | User may grant access to a malicious application simply because the application requests to have access. |
| 6 | In addition to recommendations 3, 4, and 5, it is possible to control the access to certain application specific credentials in more fine-grained level, where access to certain application specific credentials can be restricted to certain applications only. | This recommendation can protect against malicious applications that try to get access to certain application specific credentials. |
| 7 | In addition to recommendation 6, the manufacturer can pre-configure the fine-grained access control policy on the terminal or the operator can pre-configure the fine-grained access control policies on the UICC. | |
| 8 | In addition to recommendation 6, the operator can update all fine-grained access control policies on the terminal or UICC. | |
| 9 | In addition to recommendation 6, the user can add new fine-grained access control policies to the terminal or UICC. | The user may only add and modify user's own policies. The user cannot change policies set by the manufacturer or the operator. |
- Group 1: To provide the basic application credential related security in the terminal, recommendations 1 to 4 must be enforced. The basic credential security includes controlling access to UICC and to the master secret, controlling access to the Persephone server, and only the manufacturer or the operator can grant access to the credential functionality for the application.
- Group 2: If access to credential functionality for applications can be granted by the user then the recommendation 5 must be enforced.
- Group 3: If more fine-grained access to the credential functionality is wanted as described above, then recommendations 6 to 8 must be enforced. Recommendation 9 must be enforced if the user can grant access to credential functionality for an application
4.3.2 Recommendation p. 14
This technical report recommends that only recommendation group 1 in the previous clause is required. As user interaction on security is not desired and may cause breaches in credential terminal security group 2 should be not be required. Recommendation group 3 is not needed as group 2 was excluded.