Content for TR 22.848 Word version: 19.0.0
5 Use cases
5.1 Use case on Scalable SNPN Interconnect with dynamic connections
5.1.1 Description
5.1.2 Pre-conditions
5.1.3 Service Flows
5.1.4 Post-conditions
5.1.5 Existing features partly or fully covering the use case functionality
5.1.6 Potential New Requirements needed to support the use case
...
...
5 Use cases p. 6
5.1 Use case on Scalable SNPN Interconnect with dynamic connections p. 6
5.1.1 Description p. 6
This use case relates only to SNPNs that provide services in a similar way as provided by WLAN hotspots.
Today's PLMNs have a centralized database of IP addresses of all operator nodes that connect to the inter-PLMN IP backbone network, including AAA Servers/Proxies. This information is used for firewall and Border Gateway configuration. Signalling connections between VPLMN and HPLMN are long-lived (Diameter and HTTP-based N32f) and support bidirectional (inbound and outbound) signalling.
In contrast, there is no administrative entity that manages the interconnect of SNPNs on one hand and SNPN Credential Providers on the other hand. In addition, the number of interconnected SNPNs and SNPN Credential Providers is expected to be considerably greater than the number of PLMNs today. Given the large number of SNPN Credential Providers with which a SNPN needs to interconnect, it is not feasible to maintain permanently established signalling connections between them. Instead, the signalling connection needs to be established dynamically. Ideally, a signalling connection between SNPN A and SNPN Credential Provider B should be established only when a subscriber of SNPN Credential Provider B attempts to connect to SNPN A, and should be released when the last subscriber of SNPN Credential Provider B disconnects from SNPN A.
The dynamic establishment of a signalling connection between the SNPN and the SNPN Credential Provider raises several new issues, as follows:
- Outbound signalling issue: The SNPN might not know the IP address of the SNPN Credential Provider's signalling endpoints and vice versa. In some cases, the SNPN Credential Provider may be operated using a cloud provider using dynamic IP address assignment.
- Inbound signalling issue: The SNPN and/or the SNPN Credential Provider may reside behind a firewall or a Network Address Translation (NAT) device.
- End-to-end signalling issue: The SNPN and/or the SNPN Credential Provider need to have assurance that they are indeed establishing a signalling connection with each other, and that the signalling connection is secure.
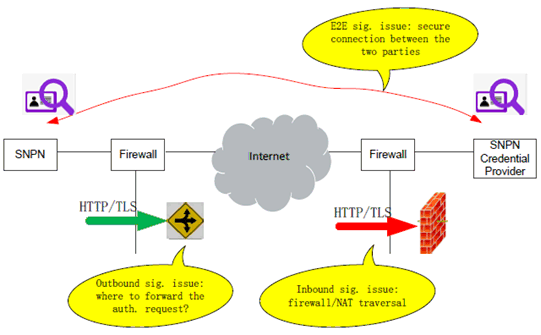
Figure 5.1.1-1: Issues with dynamic establishment of signalling connection between SNPN and SNPN Credential Provider
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
5.1.2 Pre-conditions p. 7
- NetAbove is an Internet service provider that operates SNPNs and serves as a SNPN Credential Provider. As part of the subscription contract, NetAbove allows its subscribers to connect to SNPNs owned by a variety of companies (e.g., hospitality and convention centres, airports, government institutions, schools, restaurants, coffee shops, etc.).
- NetAbove serves as a SNPN Credential Provider that can authenticate and authorize its subscriber when the subscriber attempts to connect to a SNPN.
- NetAbove does not have a direct agreement with any of these SNPNs and instead relies on a third party that assists the interconnect of entities affiliated with this third party for the purpose of subscriber authentication and authorization.
- Kaffa Koffee has launched a chain of coffee shops across the country. Each coffee shop is equipped with a small SNPN allowing customers to access Kaffa Koffee's private entertainment system, in addition to providing Internet access.
- Kaffa Koffee's customers get free access to the entertainment system on the condition that they can assert an identity that can be authenticated by a supported SNPN Credential Provider.
- A wide variety of companies can take the role of SNPN Credential Providers (e.g., mobile operators, other SNPNs). Kaffa Koffee does not have a direct agreement with any of these SNPN Credential Providers and instead relies on a third party that assists the interconnect of entities affiliated with this third party for the purpose of subscriber authentication and authorization.
- BananaFed is a third party that assists the interconnect of entities affiliated with this third party for the purpose of subscriber authentication and authorization.
- NetAbove and Kaffa Koffee both are affiliated with BananaFed.
5.1.3 Service Flows p. 8
- Roy is a subscriber of NetAbove.
- Roy is visiting a Kaffa Koffee shop and wants to access Kaffa Koffee's famous entertainment system using his 5G-capable laptop.
- Using the connection manager on his laptop, Roy selects his NetAbove subscription credentials for connection to Kaffa Koffee's SNPN.
- Kaffa Koffee's SNPN has no direct signalling connection with NetAbove. In order to authenticate the request coming from Roy's laptop, Kaffa Koffee's SNPN turns to BananaFed, a third party, for assistance. Both NetAbove and Kaffa Koffee are affiliated with BananaFed.
- NetAbove's SNPN Credential Provider server resides in NetAbove's administrative IP domain and is located behind a firewall.
- With BananaFed's assistance, the Kaffa Koffee's SNPN is able to forward the outbound authentication request to a SNPN Credential Provider server that is owned by NetAbove, even though Kaffa Koffee's SNPN has no prior knowledge of the IP address of any NetAbove's SNPN Credential Provider servers.
- With BananaFed's assistance, the NetAbove's SNPN Credential Provider server is able to receive the inbound authentication request originated by Kaffa Koffee's SNPN even though it is located behind a firewall.
- With BananaFed's assistance, the Kaffa Koffee's SNPN and NetAbove's SNPN Credential Provider server get assurance that they are establishing a secure connection with the intended remote party.
- Kaffa Koffee's SNPN succeeds in authenticating Roy with the SNPN Credential Provider server at NetAbove.
- NetAbove's SNPN Credential Provider server desires to be informed when Roy disconnects from Kaffa Koffee's SNPN. With BananaFed's assistance, NetAbove's SNPN Credential Provider server is able to forward the outbound subscription request to the SNPN operated by Kaffa Koffee, even though Kaffa Koffee's SNPN is located behind a NAT device.
5.1.4 Post-conditions p. 8
- Once Roy's laptop is connected to the Kaffa Koffee's SNPN network, Roy can enjoy access to Kaffa Koffee's entertainment system and access to the Internet.
- After some time, Roy disconnects gracefully from Kaffa Koffee's SNPN and the disconnection event is signalled to NetAbove's SNPN Credential Provider server.
5.1.5 Existing features partly or fully covering the use case functionality p. 8
None. The existing interface for interconnect between SNPN and SNPN Credential Provider (aka Credentials Holder) relies on permanent signalling connection between the SNPN and the SNPN Credential Provider.
5.1.6 Potential New Requirements needed to support the use case p. 8
[PR 5.1.6-001]
Based on the Standalone Non-Public Network (SNPN) configuration, the 5G system shall support a mechanism for a SNPN to be able to interconnect with a large number of SNPN Credential Providers with which the SNPN might not have preconfigured information detailing the IP addresses used by these SNPN Credential Providers to interconnect with the SNPN.
[PR 5.1.6-002]
Based on the Standalone Non-Public Network (SNPN) configuration, the 5G system shall support a mechanism for a SNPN Credential Provider to be able to interconnect with a large number of Standalone Non-Public Networks (SNPNs) with which the SNPN Credential Provider might not have preconfigured information detailing the IP addresses used by these SNPNs to interconnect with the SNPN Credential Provider.
[PR 5.1.6-003]
Based on the Standalone Non-Public Network (SNPN) configuration, the 5G system shall support a mechanism for a SNPN to be able to determine how to connect to a SNPN Credential Provider capable of verifying the identity presented by a user attempting to connect to that SNPN.
[PR 5.1.6-004]
Based on the Standalone Non-Public Network (SNPN) configuration, the 5G system shall support a mechanism for a SNPN to be able to securely interconnect with a SNPN Credential Provider in deployments where the required security information is not preconfigured.
[PR 5.1.6-005]
Based on the Standalone Non-Public Network (SNPN) configuration, the 5G system shall support a mechanism for a SNPN to enable a SNPN Credential Provider to securely notify events (e.g., a user's subscription ending) to the Standalone Non-Public Network (SNPN).