TR 41.031
FIGS — Service Requirements
V18.0.0 (PDF)
2024/03 11 p.
V17.0.0
2022/03 11 p.
V16.0.0
2020/06 11 p.
V15.0.0
2018/06 11 p.
V14.0.0
2017/03 11 p.
V13.0.0
2016/01 11 p.
V12.0.0
2014/09 11 p.
V11.0.0
2012/09 11 p.
V10.0.0
2011/04 11 p.
V9.0.0
2009/12 11 p.
V8.0.0
2008/12 11 p.
V7.0.0
2007/06 11 p.
V6.0.0
2005/01 11 p.
V5.0.0
2002/06 11 p.
V4.0.1
2001/05 11 p.
GSM Rel-99 v8.0.0
2000/06 10 p.
GSM Rel-98 v7.0.1
1998/06 10 p.
- Rapporteur:
- Mr. Sahlin, Bengt
Ericsson LM
Content for TR 41.031 Word version: 18.0.0
1 Scope
2 Normative references
3 Definitions and abbreviations
4 Fraud Information Gathering System overview
5 The need for fraud detection systems and controls
5.1 Outline of present situation
5.2 General Principles
5.3 Capabilities
5.4 Service conditions
5.5 Information Delivery Time
5.6 Subscriber Data Volumes
6 Interface between HPLMN and FDS
7 Security of the system
$ Change History
1 Scope p. 5
This Technical Report describes the requirements (at a stage 0 level) of the Fraud Information Gathering System (FIGS). FIGS provides the means for the HPLMN to monitor a defined set of subscriber activities.
The aim is to enable service providers/network operators to use FIGS, and service limitation controls such as Operator Determined Barring (ODB) and Immediate Service Termination (IST), to limit their financial exposure to large unpaid bills produced on subscriber accounts whilst the subscriber is roaming outside their HPLMN. HPLMNs may also choose to collect information on subscriber activities whilst their subscribers are within the HPLMN.
2 Normative references p. 5
The following documents contain provisions which, through reference in this text, constitute provisions of the present document.
- References are either specific (identified by date of publication, edition number, version number, etc.) or non-specific.
- For a specific reference, subsequent revisions do not apply.
- For a non-specific reference, the latest version applies. In the case of a reference to a 3GPP document (including a GSM document), a non-specific reference implicitly refers to the latest version of that document in the same Release as the present document.
3 Definitions and abbreviations p. 5
3.1 Definitions p. 5
For the purposes of this report the following definitions apply:
monitored activities:
subscriber activities that must be reported to the HPLMN. These can be call related events (e.g. call-set-up, call termination) or the invocation of call related and call independent supplementary services (e.g. Call Hold, Call Waiting, Call Transfer, Call Forwarding, Unstructured Supplementary Service Data).
Home Network:
The home PLMN including non-GSM elements such as the Fraud Detection System (FDS), customer service systems and billing.
3.2 Abbreviations p. 5
Abbreviations used in this report are listed in GSM 01.04.
For the purposes of this report the following abbreviations apply:
FIGS
Fraud Information Gathering System
FDS
Fraud Detection System
This is not necessarily an automatic system but may be one that requires human intervention.
IST
Immediate Service Termination
4 Fraud Information Gathering System overview p. 6
A number of proposals have been suggested for a Subscriber Supervisory System (SSS) for which specifications were produced from May 1995 through to December 1996. Following joint review between SMG1 and SMG10, it was agreed that the system should be re-specified to take account of network operator and manufacturer needs for a Fraud Information Gathering System (FIGS). This report provides an outline of such a system.
This report describes a method by which the Home Network can be provided with data on the activities of its subscribers in a VPLMN. The Home Network can make inferences about what the subscriber is doing and then take decisions on what the subscriber should be allowed to do. This report does not address any Fraud Detection systems or the intelligence that is used to advise the HPLMN on the controls to be applied to a subscriber.
Figure 1 shows the flow of messages between the HPLMN and the VPLMN and between the HPLMN and the FDS.
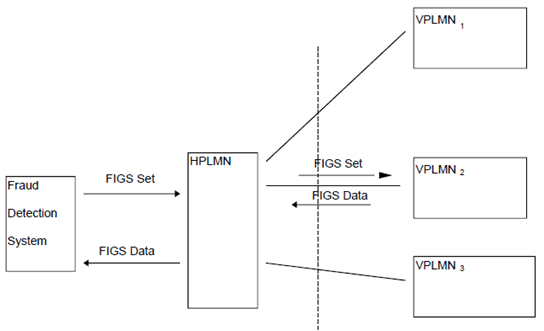
Figure 1: Flow of messages between the HPLMN and the VPLMN and between the HPLMN and the FDS
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
5 The need for fraud detection systems and controls p. 6
5.1 Outline of present situation p. 6
Modern telecommunications networks, particularly mobile networks provide the potential for fraudsters to make use of telecommunication services (Voice, Data, Fax etc.) without the intent to pay. A number of different scenarios are exploited and it is up to the network operator or service provider to detect misuse where it occurs and to stop it at the earliest possible opportunity.
The scale of frauds can be many thousand of ECU per day on a single account when International or Premium rate numbers are called. The most common types of fraud that effect networks like GSM are related to the ability to sell calls at below market price using stolen air-time/equipment where the user of the equipment does not intend to pay the network operator or service provider. Fraudulent subscribers often avoid payment by obtaining a handset and a subscription to a GSM network by fraudulently giving details and justifications to the network operators/service provider. If there are not good controls within the network the subscriber can make a large volume of calls to expensive destinations and accumulate a large bill.
Roaming, in co-ordination with advanced services such as call transfer and multi-party calls, complicates the issue further, requiring control of the customer within the VPLMN. Many simultaneous calls can be set up and large bills accumulated in a short time. At present no system exists within the GSM network architecture for speedily transferring information on subscriber activity from the VPLMN to the HPLMN.
In the future, SIMs may roam to non-GSM networks, further broadening the area over which control is required. It is recognised that if FIGS is implemented in non-GSM networks that suitable inter-working units will be required to translate commands and information.
5.2 General Principles p. 7
The PLMN network should be able to supply relevant information to the HPLMN network so it can make a decision on whether to terminate a call or to change the Operator Determined Barring (ODB) configuration for the specific subscriber. This decision will be carried out by the HPLMN or service provider. It is recognised that there is a limit to the type and volume of information that can be transferred between the VPLMN and the HPLMN. Therefore the requirement for the system is that distilled and standardised information must be supplied between the VPLMN and HPLMN.
5.3 Capabilities p. 7
The following minimum capabilities are required. See Figure 1.
Within the Home Network:
- to mark a subscriber, defined by the IMSI or MSISDN, as being under FIGS control ("FIG Set");
- to receive from the VPLMN the data described below;
- to remove the monitoring of a subscriber's activities ("FIGS Unset").
-
to transmit to the HPLMN information (FIGS Data):
- at the start of a call;
- at the end of a call;
- during a call` for long calls or at the mid-call invocation of supplementary services.
5.4 Service conditions p. 7
The following service conditions shall apply:
- FIGS shall not modify the VPLMN's service;
- FIGS should not alter any standard GSM functionality seen by the customer or effect the service quality;
- If the VPLMN network does not have the resources to support a FIGS Set command it shall respond accordingly to the HPLMN.
5.5 Information Delivery Time p. 7
The need for up to date information is a critical part of any fraud information system. The sooner data is transferred to the HPLMN, the sooner fraud can be stopped. Therefore the proscribed information shall be transferred from the VPLMN to the HPLMN within two minutes of the occurrence of a FIGS-monitored event
The information shall preferably be transferred from the VPLMN to the HPLMN over existing communication links (e.g. SS7 signalling links).
5.6 Subscriber Data Volumes p. 8
If the support of FIGS is causing overload within the VPLMN the FIGS system shall not permit the marking of new subscribers. The VPLMN should therefore handle up to a realistic limit any requests for marking of subscribers and be able to support the associated data transfer. The setting of this limit is outside the scope of this report.
Each VPLMN should limit the number of subscribers that each HPLMN may request to be monitored using FIGS. Otherwise an HPLMN may take more than its "fair share" of the FIGS processing capability of a VPLMN.
A mechanism shall be required whereby a VPLMN can charge an HPLMN for the bulk data transfer made to that HPLMN.
6 Interface between HPLMN and FDS p. 8
The interface between the home network and the network's fraud detection and processing systems shall be through a specific interface. This will be used to present information to the fraud detection systems. The contents of messages sent on this interface shall be specified but not the transfer mechanism. This is in line with the approach used for the X-interface as specified in GSM 02.33.
The FDS will indicate to the HPLMN subscribers that should be subject to FIGS monitoring. This information will update the HPLMN HLR.
Information, as listed in subclause 5.3 gathered from the VPLMN will be transferred to the FDS system. Following processing of this information, the FDS system can take no action or can advise the home network to do one of the following:
- update ODB categories;
- instigate an Immediate Service Termination (IST);
- mark the subscriber as not being required to be monitored under FIGS.
7 Security of the system p. 8
It is expected that there will be a need for authentication, data integrity and confidentiality of the commands and data transferred between PLMNs.
These issues are for study under other work items within the SMG10 work programme.