Content for TS 33.310 Word version: 19.3.0
5 Architecture and use cases of the NDS/AF
5.1 PKI architecture for NDS/AF
5.1.1 General architecture
5.1.1.1 NDS/IP case
5.1.1.2 TLS case
...
...
5 Architecture and use cases of the NDS/AF p. 13
The following types of certification authority are defined:
- SEG CA: A CA that issues end entity certificates to SEGs within a particular operator's domain.
- NE CA: A CA that issues end entity IPsec certificates to NE's within a particular operator's domain. Certificates issued by an NE CA shall be restricted to the Zb-interface.
- TLS client CA: A CA that issues end entity TLS client certificates to TLS entities within a particular operator's domain.
- TLS server CA: A CA that issues end entity TLS server certificates to TLS entities within a particular operator's domain.
- Interconnection CA: A CA that issues cross-certificates on behalf of a particular operator to the SEG CAs, TLS client CAs and TLS server CAs of other domains with which the operator's SEGs and TLS entities have interconnection.
5.1 PKI architecture for NDS/AF p. 13
This chapter defines the PKI architecture for the NDS/AF. The goal is to define a flexible, yet simple architecture, which is easily interoperable with other implementations.
The architecture described below uses a simple access control method, i.e. every element which is authenticated is also provided service. More fine-grained access control may be implemented, but it is out of scope of this specification.
The architecture does not rely on bridge CAs, but instead uses direct cross-certifications between the security domains. This enables easy policy configurations in the SEGs and TLS entities.
5.1.1 General architecture p. 13
Unless the operator chooses to combine CAs, each security domain has at least one SEG CA, NE CA, TLS client CA or TLS server CA, and one Interconnection CA dedicated to it.
The SEG CA of the domain issues certificates to the SEGs in the domain that have interconnection with SEGs in other domains i.e. Za-interface. The SEG certificate can be used also in communication with an NE over the Zb-interface. An NE CA issues certificates to NE's for communication between NEs and between NE and SEGs within the responsible domain i.e. Zb interface. The TLS client CA of the domain issues certificates to the TLS clients in that domain that need to establish TLS connections with TLS servers in other domains. The TLS server CA of the domain issues certificates to the TLS servers in that domain that need to establish TLS connections with TLS clients in other domains. The Interconnection CA of the domain issues certificates to the SEG CAs, TLS client CA or TLS server CA, of other domains with which the operator's SEGs and TLS entities have interconnection. This specification describes the profile for the various certificates that are needed. Also a method for creating the cross-certificates is described.
In general, all of the certificates shall be based on the Internet X.509 certificate profile [14].
5.1.1.1 NDS/IP case |R7| p. 14
In the following, the architecture for issuing IPsec certificates using SEG CAs is described.
The SEG CA shall issue certificates for SEGs that implement the Za interface. When SEG of the security domain A establishes a secure connection with the SEG of the domain B, they shall be able to authenticate each other. The mutual authentication is checked using the certificates the SEG CAs issued for the SEGs. When an interconnect agreement is established between the domains, the Interconnection CA cross-certifies the SEG CA of the peer operator. The created cross-certificates need only to be configured locally to each domain. The cross-certificate, which Interconnection CA of security domain A created for the SEG CA of security domain B, shall be available for the domain A SEG which provides the Za interface towards domain B. Equally the corresponding certificate, which the Interconnection CA of the security domain B created for the SEG CA of security domain A, shall be available for the domain B SEG which provides Za interface towards domain A.
The general architecture for IPsec certificate based authentication of SEGs and NEs is illustrated in Figure 2.
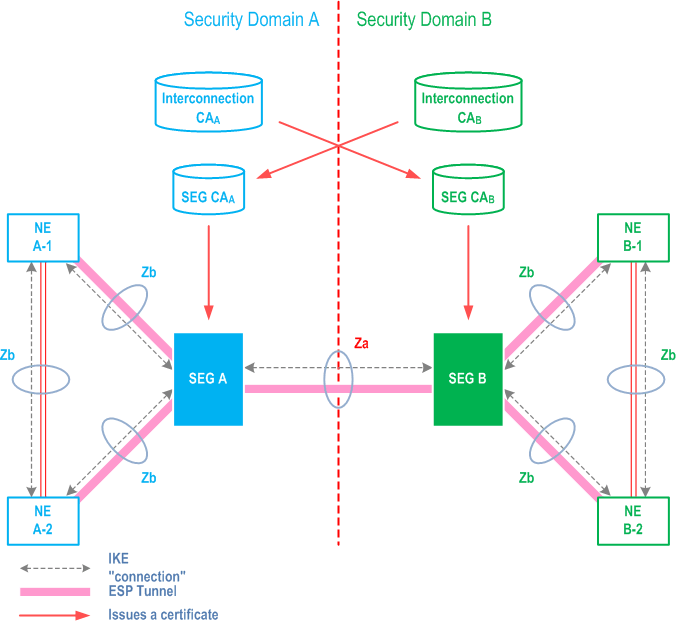
After cross-certification, the SEGa is able to verify the path: SEGb → SEG CAB → Interconnection CAA. Only the certificate of the Interconnection CAA in domain A needs to be trusted by entities in security domain A.
Equally the SEGb is able to verify the path: SEGa → SEG CAA → Interconnection CAB. The path is verifiable in domain B, because the path terminates to a trusted certificate (Interconnection CAB of the security domain B in this case).
The Interconnection CA signs the second certificate in the path. For example, in domain A, the certificate for SEG CA B is signed by the Interconnection CA of domain A when the cross-certification is done.
5.1.1.2 TLS case |R7| p. 15
In the following, the architecture for issuing TLS certificates using TLS CAs is described.
The TLS client CA shall issue certificates for TLS clients in its domain. Similarly the TLS server CA shall issue certificates for TLS servers in its domain. When a TLS entity of the security domain A establishes a secure connection with a TLS entity of the domain B, they shall be able to authenticate each other. The mutual authentication is checked using the certificates the TLS client/server CAs issued for the TLS entities. When an interconnect agreement is established between the domains, the Interconnection CA cross-certifies the TLS client/server CAs of the peer operator. The created cross-certificates need only to be configured locally to each domain. The cross-certificate, which Interconnection CA of security domain A created for the TLS client/server CAs of security domain B, shall be available for the domain A TLS entities which need to communicate with domain B. Equally the corresponding certificate, which the Interconnection CA of the security domain B created for the TLS client/server CAs of security domain A, shall be available for the domain B TLS entities which need to communicate with domain A.
The general architecture for authentication of TLS entities is illustrated in Figure 2a.
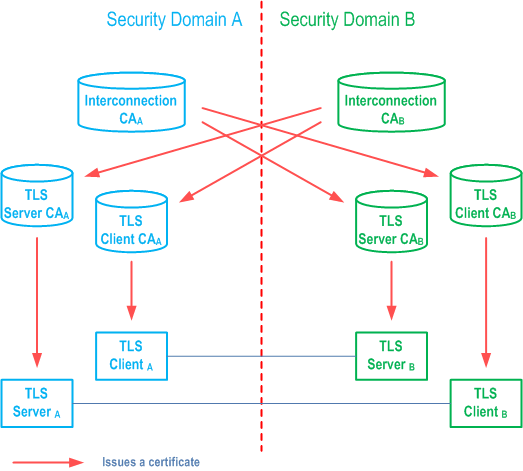
After cross-certification, the TLS client A is able to verify the path: TLS server B → TLS server CAB → Interconnection CAA. Only the certificate of the Interconnection CAA in domain A needs to be trusted by entities in security domain A.
Equally the TLS server B is able to verify the path: TLS client A → TLS client CAA → Interconnection CAB. The path is verifiable in domain B, because the path terminates to a trusted certificate (Interconnection CAB of the security domain B in this case).
The Interconnection CA signs the second certificate in the path. For example, in domain A, the certificates for TLS server CA B and TLS client CA B are signed by the Interconnection CA of domain A when the cross-certification is done.