Content for TS 33.204 Word version: 18.0.0
A Guidelines for manual key management
A.1 Inter-domain Security Association and Key Management Procedures
A.2 Local Security Association Distribution
B TCAPsec message flows
C High level migration strategy
C.1 Transition phase from unprotected to protected message transfer
C.2 Transition phase from protected message transfer to unprotected message transfer.
C.3 Transition phase from protected mode to another protected mode
D Using TCAP handshake for SMS transfer
D.1 Mobile Terminated SMS
D.2 Mobile Originated SMS
$ Change History
A Guidelines for manual key management p. 15
A.1 Inter-domain Security Association and Key Management Procedures p. 15
Manual Inter-domain Security Association and Key Management procedures is subject to roaming agreements.
Some important parts of an inter-domain Security Association and Key Management agreement are:
- to define how to carry out the initial exchange of TCAPsec SAs;
- to define how to renew the TCAPsec SAs;
- to define how to withdraw TCAPsec SAs (including requirements on how fast to execute the withdrawal);
- to decide if fallback to unprotected mode is to be allowed;
- to decide on key lengths, algorithms, protection mode, and SA expiry times, etc (TCAPsec SAs are expected to be fairly long lived).
A.2 Local Security Association Distribution p. 15
Manual Local Security Association Distribution is executed entirely within one network and is consequently at the discretion of the administrative authority.
The requirement on the manual distribution procedures can be summarized as follows:
- Procedures for transporting the relevant TCAPsec SA to the SS7-SEG shall be defined. In order to ensure that the TCAPsec SA are present when needed, all valid TCAPsec SA should be distributed to all SS7-SEG as soon as they are available.
- Procedures for revocation of TCAPsec SAs shall be defined.
B (Normative) TCAPsec message flows p. 16
Imagine a network scenario with two SS7-SEG at different PLMNs (SS7-SEGa in the sending PLMN A and a SS7-SEGb in the receiving PLMN B) willing to communicate using TCAPsec. Figure B-1 presents the message flow.
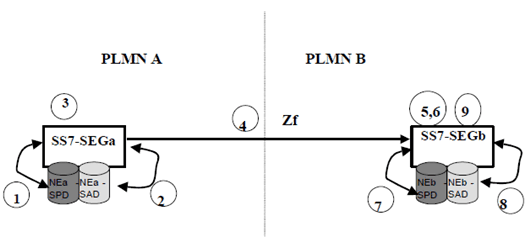
According to Figure B-1, when SS7-SEGa from PLMN A on behalf of NEa needs to send a message towards NEb within PLMN B using TCAPsec, the process is the following:
The Sending Entity SS7-SEGa performs the following actions during the outbound processing of every TCAP user message:
Step 1.
At the Receiving PLMN, an SS7-SEG (e.g. SS7-SEGb) performs the following actions during the inbound processing of every TCAP user message it received:
SS7-SEGa checks its Security Policy Database (SPD) to check if TCAPsec mechanisms shall be applied towards PLMN B:
Step 2.
- If the SPD does not mandate the use of TCAPsec for the TCAP user application part towards PLMN B, then normal TCAP communication procedures will be used and the process continues in step 4.
- If the SPD mandates the use of TCAPsec for the TCAP user application part towards PLMN B, then the process continues at step 2.
- If no valid entry in the SPD is found for PLMN B, then the communication is aborted and the message is discarded.
SS7-SEGa checks its Security Association Database (SAD) for a valid Security Association (SA) to be used towards PLMN B. In the case where more than one valid SA is available at the SAD, SS7-SEGa shall choose the one, the soft expiry time of which will be reached next.
Step 3.
- In case protection of TCAPsec messages towards PLMN B is not possible (e.g. no SA available, invalid SA…), then the message is discarded.
- If a valid SA exists then the process continues at step 3.
SS7-SEGa constructs the TCAPsec message towards NEb using the parameters (keys, algorithms) found in the SA and the protection mode from the SPD.
Step 4.
SS7-SEGa either:
- sends a TCAPsec message towards PLMN B (from step 3).
- forwards an unprotected TCAP message in the event that the SPD towards PLMN B allowed it (step 1.a).
Step 5.
END:
If a TCAP message is received for which no valid SPD entry exists (i.e. SCCP calling party address is unknown) then the message is discarded (Process goes to END).
Step 6.
If an unprotected TCAP message is received, the process continues with step 7.
Otherwise, SS7-SEGb decomposes the received TCAPsec message and retrieves SPI from the security header.
Step 7.
The SS7-SEGb checks the SPD:
An unprotected TCAP message is received:
Step 8.
- If an unprotected TCAP message is received and fallback to unprotected mode is allowed for the specified SCCP calling party address and TCAP user application part, then the unprotected TCAP message is simply processed (Process goes to END)
- If an unprotected TCAP message is received, but the SPD mandates the use of TCAPsec and fallback to unprotected mode is NOT allowed for the specified SCCP calling party address and TCAP user application part, then the message is discarded.
- If a TCAPsec message is received, but the SPD indicates that TCAPsec is NOT to be used, then the message is discarded.
- If a TCAPsec message is received and the SPD indicates that TCAPsec is required, then the process continues at step 8.
The receiving SS7-SEG checks its SAD to retrieve the relevant SA information for processing of the TCAPsec message:
Step 9.
- If the received SPI does not point to a valid SA, then the message is discarded.
- If the received SPI points to a valid SA, and if the Source and Destination Network Id, which are retrieved via the SPI, align with those from SCCP layer, then the SS7-SEG retrieves the protection mode from the SPD and the cryptographic information (keys, algorithms) from the SAD and the process continues at step 9, otherwise the message is discarded.
Freshness of the protected message is checked by ensuring the Time Variant Parameter (TVP) is in an acceptable window. Integrity and encryption mechanisms are applied to the message according to the identified protection level, by using the information in the SA (keys, algorithms).
- If the result after applying such mechanisms is NOT successful then the message is discarded.
- If the result after applying such procedures is successful, then SS7-SEG has the cleartext TCAP message NEa originally wanted to send to NEb. The cleartext TCAP message can now be forwarded by the receiving SS7-SEG to NEb (Process goes to END)
A cleartext TCAP user message is available at the receiving SS7-SEG.
In the event the received message at NEb requires an answer to NEa (Return Result/Error), an SS7 SEG in PLMN B will, on behalf of NEb perform the process in steps 1 to 4 acting as the Sender and an SS7 SEG in PLMN A will perform the process in steps 5 to 8 acting as the Receiver and forward a successfully received message to NEa.
C High level migration strategy p. 18
This Annex describes three types of protection mode changes, which each may be performed per TCAP user application part between a pair of networks.
C.1 Transition phase from unprotected to protected message transfer p. 18
By applying a migration strategy which is coordinated between the two PLMN operators (A and B) it can be assured that protected messages are not sent from PLMN A to PLMN B (and vice versa) before operator B confirms completion of SS7-SEG introduction in his network.
In order to avoid traffic interruption during the transition phase from unprotected to protected message transfer between tw' operators' PLMNs the following course of action is recommended:
Precondition: It is assumed that neither operator A, nor operator B have activated TCAPsec for the TCAP user application part(s) that needs protection and now are going to set up use of TCAP user security for traffic to and from each other.
- Operator A negotiates Security Associations with operator B and stores the SAs in the SAD. Both operators also agree on the policy that shall be applied for the different TCAP user application parts of the messages that needs to be exchanges between the PLMNs.
- Operator A modifies the Security Policy in his gateways as follows: Messages received from operator B's PLMN should be protected according to the indicated protection mode by the SPD; however fallback to unprotected mode is allowed, i.e. unprotected messages received from'operator B's PLMN are not blocked. This means that incoming messages with an SCCP calling party address pointing to operator B are accepted by PLMN A. Operator A does not send protected messages yet.
- When Operator A has completed step 2 in all his SS7-SEGs, he informs Operator B.
- When Operator A receives confirmation that operator B also has performed step 2, Operator A modifies the Security Policy in his gateways as follows: Outgoing messages sent to operator B's PLMN shall be protected as indicated by the SPD.
- When Operator A has completed step 4 in all his SS7-SEGs, he informs Operator B which can then perform step 4 and 6 towards Operator A.
- When Operator A receives confirmation from Operator B that he has performed step 4, Operator A modifies the Security Policy in his gateways as follows: Fallback to unprotected mode is not allowed, i.e. unprotected messages received from'operator B's PLMN will be blocked.
C.2 Transition phase from protected message transfer to unprotected message transfer. p. 19
In order to avoid traffic interruption during the transition phase from protected to unprotected message transfer between two operators' PLMNs, the following course of action is recommended:
Precondition: It is assumed that operator A has already successfully set up the use of TCAP user security for traffic to and from operator B and is now going to remove use of TCAP user security for traffic to and from operator B.
- Operator A modifies the Security Policy in his gateways as follows: Messages received from operator B's PLMN may still be protected according to the stored SA, however fallback to unprotected mode is allowed.
- When Operator A has completed step 1 in all his SS7-SEGs, he informs Operator B.
- When Operator A receives confirmation from Operator B that all SS7-SEGs in Operator B's PLMN have been set up to allow fallback to unprotected mode, Operator A changes the SPD entries to send unprotected outgoing messages via his SS7-SEGs, but allow the reception of protected messages from network B.
- When Operator A has completed step 3 in all his SS7-SEGs, he informs Operator B.
- When Operator A receives confirmation from Operator B that the SPD entries were changed to unprotected in all SS7-SEGs of Operator B's network, Operator A performs the similar change in his SS7-SEGs.
C.3 Transition phase from protected mode to another protected mode p. 19
In order to avoid traffic interruption during the phase where the used protection mode is modified in the SS7-SEGs' SPDs, the following course of action is recommended:
Precondition: It is assumed that operator A's policy is to protect all messages exchanged with operator B's PLMN with protection mode "integrity+authenticity"; now both Operators are going to modify the policy to protect messages sent to the other PLMN with protection mode "integrity+authenticity+confidentiality".
- Operator A and B both modify the SPD by adding "integrity+authenticity+confidentiality" to the acceptable protection modes, i.e. they will now allow both "integrity+authenticity+confidentiality" and "integrity+authenticity" as acceptable protection modes, but outgoing messages are still sent with "integrity+authenticity".
- When step 1 is completed in all SS7-SEGs of Operator B's PLMN, Operator A is informed. Similarly Operator A will inform Operator B after performing the actions of Step 1.
- When Operator A (or Operator B) receives confirmation from Operator B (or Operator A) that the SPDs in all SS7-SEGs have been updated to accept the new protection mode in addition to the old one, Operator A (or operator B) modifies the SPD such that outgoing messages in his SS7-SEGs towards Operator B (or operator A) are send with only with protection mode "integrity+authenticity+confidentiality".
- When step 3 is completed in all SS7-SEGs of Operator A's (or Operator B's) PLMN, he informs Operator B (or Operator A).
- When receiving confirmation that the SPDs have been updated in all SS7-SEGs of Operator A (or Operators B's) PLMN, Operator B (or Operator A) modifies the SPD by removing "integrity+authenticity" from the acceptable protection modes.
D (Normative) Using TCAP handshake for SMS transfer p. 21
The SMS Gateway/Interworking MSC operator and the serving node (MSC or SGSN) operator may agree to use the TCAP handshake as a countermeasure against SMS fraud for messages exchanged between their networks (for detailed message flows see TS 29.002). A limited level of authenticity is provided by the following mechanisms.
D.1 Mobile Terminated SMS p. 21
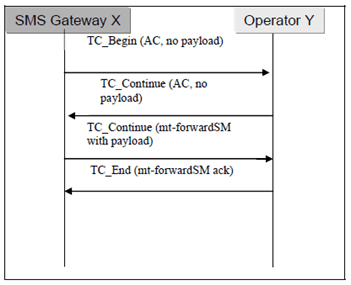
If the serving network receives an mt-forward-SM MAP message which uses the TC_Continue to transfer the MAP payload then it is guaranteed that the SCCP calling party address of the (empty) TC_Begin message is authentic, otherwise the first TC-continue message would be sent to the falsified address. The correct message flow is guaranteed by the TCAP transaction capabilities (use of Transaction ID).
Unfortunately there are some ways in which a fraudulent SMS Gateway operator (called the originator in bullets (a) and (b)) may try to circumvent the implicit SCCP address authentication provided by the TCAP handshake.
- The originator includes a falsified SMS-GMSC address as SM-RP-OA in the mt-forward-SM payload carried by the TC-continue (third message in Figure D.1)
- The originator tries to predict the TCAP transaction ID assigned by the serving node, which is to be used within the third message, and spoofs the third message without waiting for the second message. This attack has to be carried out within the right time window.
The receiving network shall verify if the received SMS-GMSC address (as SM-RP-OA in the third message) may be used from the SCCP Calling Party Address. Some operators use a single SMS-GMSC address for a range of SCCP Calling Party Addresses and this will need to be taken into consideration.
If TCAP handshake is to be used, at least one of the following measures shall be taken within the network of the serving node in order to counteract the spoofing possibilities of a malicious mt-Forward-SM originator.
MEAS-2a:
The receiving node shall use mechanisms to ensure that the destination TCAP transaction ID which needs to be used within the third message is predictable with a probability of less than 1 / 210 for a third party knowing all previous TCAP transaction ID values.
MEAS-2b:
The receiving network shall wait n seconds before it processes the third message (TC-continue(mt-forwardSM with payload)). This should ensure that the TC_abort from the spoofed network is processed at the destination node earlier than a TC_continue including a successfully guessed TCAP Transaction ID value.
The following grouping method may be used for an operator to gradually introduce the TCAP handshake for mt-Forward-SM messages. Define an 'operator group-1' as a trusted operator group and 'operator group-2' as an un-trusted operator group. Agree that group-1 uses the TCAP handshake, while group-2 does not use the TCAP handshake. As specified by TS 29.002 this requires that the SMS Gateway operators belonging to group-1 shall either use application context2 or 3 for mt-Forward-SM. The management of the two groups requires that the serving network shall implement a policy table of SCCP Calling Party Addresses for which a TCAP handshake is required.
If the above described grouping method is used then the following measure shall be taken at the serving network in order to counteract the spoofing possibilities of a malicious mt-Forward-SM originator that tries to circumvent the policy table checks.
MEAS-3:
The serving network shall verify that the SCCP Calling Party Address of a first message with a payload (i.e. not using the TCAP handshake) is not from an SMS-GMSC-address as SM-RP-OA that shall use the TCAP handshake.
The benefit gained for operators that belong to group-1 is that spoofing of their SMS-GMSC-addresses is practically difficult if the policy table has been administrated accurately.
D.2 Mobile Originated SMS p. 22
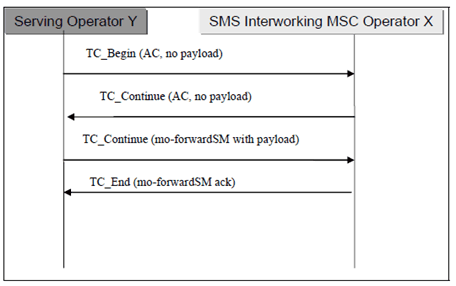
If the serving network sends an mo-forward-SM MAP message which uses the TC_Continue to transfer the MAP payload then it is guaranteed that the SCCP calling party address of the (empty) TC_Begin message is authentic, otherwise the first TC-continue message would be sent to the falsified address. The correct message flow is guaranteed by the TCAP transaction capabilities (use of Transaction ID).
Unfortunately there are some ways in which a fraudulent serving (MSC or SGSN) operator (called the originator in bullets (a) and (b)) may try to circumvent the implicit SCCP address authentication provided by the TCAP handshake.
- The originator includes a falsified MSISDN as SM-RP-OA within the mo-forward-SM payload carried by the TC-continue (third message in Figure D.2)
- The originator tries to predict the TCAP transaction ID assigned by the serving node, which is to be used within the third message, and spoofs the third message without waiting for the second message. This attack has to be carried out within the right time window.
The receiving node (i.e. SMS interworking MSC) may query the HLR to verify if the received SCCP Calling Party Address of the mo-forward-SM is from the same network which is currently serving the subscriber (MSISDN contained in SM-RP-OA in the third message).
If the TCAP handshake is to be used, then at least one of MEAS-2a and MEAS-2b of clause D.1 shall also be applied.
The following grouping method may be used for an operator to gradually introduce the TCAP handshake for mo-Forward-SM messages. Define an 'operator group-1' as a trusted operator group and 'operator group-2' as an un-trusted operator group. Agree that group-1 uses the TCAP handshake, while group-2 does not use the TCAP handshake. As specified by TS 29.002 this requires that the MSC operators belonging to group-1 shall either use application context2 or 3 for mo-Forward-SM. The management of the two groups requires that the network of the SMS Interworking MSC shall implement a policy table of originating SCCP-addresses for which a TCAP handshake is required.
If the above described grouping method is used then the following measure shall be taken at the network of the SMS Interworking MSC in order to counteract the spoofing possibilities of a malicious mo-Forward-SM originator that tries to circumvent the policy table checks.
MEAS-3:
The SMS Interworking MSC shall verify that the SCCP Calling Party address of a first message with a payload (i.e. not using the TCAP handshake) is not from an address that shall use the TCAP handshake.
The benefit gained for operators that belong to group-1 is that mo-Forward-SM spoofing for their subscribers, while roaming within group-1, becomes practically difficult if the policy table has been administrated accurately.