Content for TS 33.203 Word version: 18.1.0
4 Overview of the security architecture p. 14
In the PS domain, the service is not provided until a security association is established between the UE and the network. IMS is essentially an overlay to the PS-Domain and has a low dependency of the PS-domain. Consequently a separate security association is required between the multimedia client and the IMS before access is granted to multimedia services. The IMS Security Architecture is shown in Figure 1.
IMS authentication keys and functions at the user side shall be stored on a UICC. It shall be possible for the IMS authentication keys and functions to be logically independent to the keys and functions used for PS domain authentication. However, this does not preclude common authentication keys and functions from being used for IMS and PS domain authentication according to the guidelines given in clause 8.
For the purposes of the present document the ISIM is a term that indicates the collection of IMS security data and functions on a UICC. Further information on the ISIM is given in clause 8.
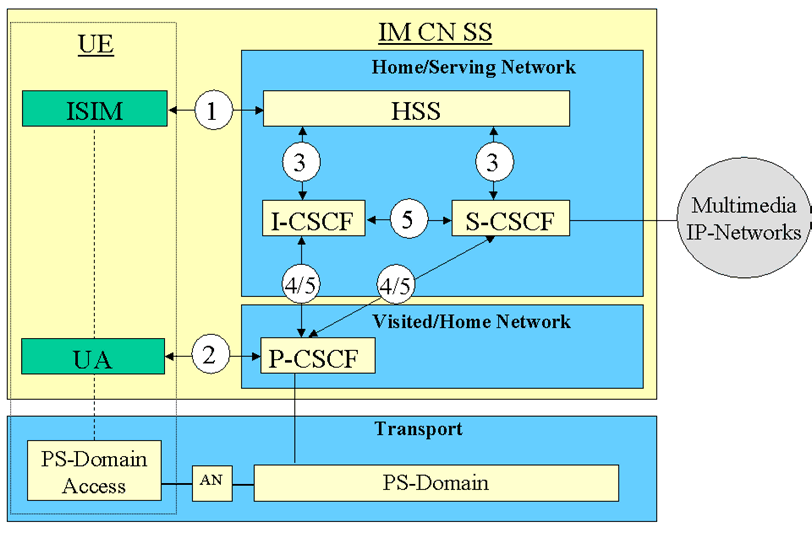
There are five different security associations and different needs for security protection for IMS and they are numbered 1, 2, 3, 4 and 5 in Figure 1 where:
1)
There exist other interfaces and reference points in IMS, which have not been addressed above. Those interfaces and reference points reside within the IMS, either within the same security domain or between different security domains. The protection of all such interfaces and reference points apart from the Gm reference point are protected as specified in TS 33.210.
Mutual authentication is required between the UE and the HN.
The mechanisms specified in this technical specification are independent of the mechanisms defined for the CS- and PS-domain.
An independent IMS security mechanism provides additional protection against security breaches. For example, if the PS-Domain security is breached the IMS would continue to be protected by its own security mechanism. As indicated in Figure 1 the P-CSCF may be located either in the Visited or the Home Network. The P-CSCF shall be co-located within the same network as the GGSN/PGW, which may reside in the VPLMN or HPLMN according to the APN and GGSN/PGW selection criteria, cf. TS 23.060 and TS 23.401.
Provides mutual authentication. The HSS delegates the performance of subscriber authentication to the S-CSCF. The long-term key in the ISIM and the HSS is associated with the IMPI. The subscriber will have one (network internal) user private identity (IMPI) and at least one external user public identity (IMPU).
2)
Provides a secure link and a security association between the UE and a P-CSCF for protection of the Gm reference point. Data origin authentication is provided i.e. the corroboration that the source of data received is as claimed. For the definition of the Gm reference point cf. TS 23.002.
3)
Provides security within the network domain internally for the Cx-interface. This security association is covered by TS 33.210. For the definition of the Cx-interface cf. TS 23.002.
4)
Provides security between different networks for SIP capable nodes. This security association is covered by TS 33.210. This security association is only applicable when the P-CSCF resides in the VN and if the P-CSCF resides in the HN then bullet point number five below applies, cf. also Figure 2 and Figure 3.
5)
Provides security within the network internally between SIP capable nodes. This security association is covered by TS 33.210. Note that this security association also applies when the P-CSCF resides in the HN.
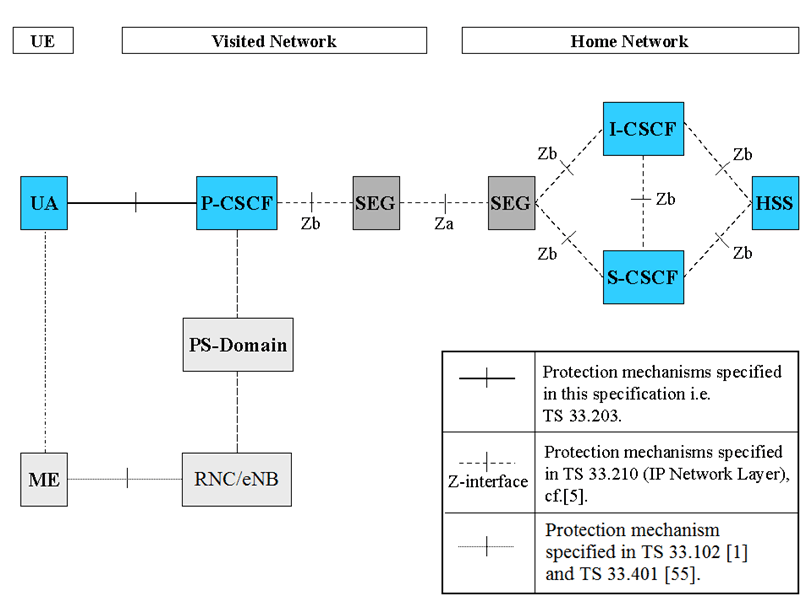
This Figure gives an overview of the security architecture for IMS and the relation with Network Domain security, cf. TS 33.210, when the P-CSCF resides in the VN.
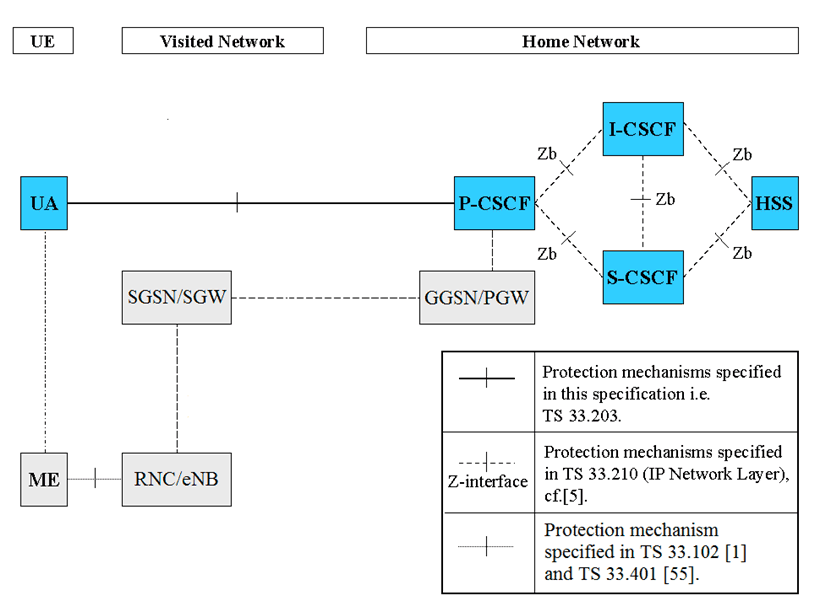
This Figure gives an overview of the security architecture for IMS and the relation with Network Domain security, cf. TS 33.210, when the P-CSCF resides in the HN.
The confidentiality and integrity protection for SIP-signalling is provided in a hop-by-hop fashion, cf. Figure 2 and Figure 3. The first hop i.e. between the UE and the P-CSCF is specified in this technical specification. The other hops, inter-domain and intra-domain are specified in TS 33.210.