Content for TS 33.106 Word version: 18.0.0
5 Requirements
5.1 Description of requirements
5.2 Normal operation
5.3 Exceptional procedures
5.4 Interworking considerations
5.5 Charging aspects
5.6 Minimum service requirements
5.7 LI Requirements for encrypted services
5.8 Lawful Interception for Customized Alerting Tone (CAT)
5.9 Lawful Interception for Customized Ringing Signal (CRS)
5.10 Lawful Interception for Home Node B and Home enhanced Node B (H(e)NB)
5.11 Location information
5.12 LI requirements for IMS VoIP Service
5.13 Delivery requirements for messaging
5.14 LI requirements for management of IMS supplementary services settings
5.15 LI requirements for IMS Video Service
5.16 LI requirements for IMS based Push-to-Talk
6 Handover interface requirements
5 Requirements p. 8
5.1 Description of requirements p. 8
The present subclause gives the general description of historical lawful interception requirements for Rel-14 and earlier 3GPP networks.
5.1.1 General technical requirements p. 9
Figure 1 shows the general system for interception. Technical interception is implemented within a 3GPP network by special functionality on network elements shown in the figure. Specific lawful interception architecture and functions are found in TS 33.107.
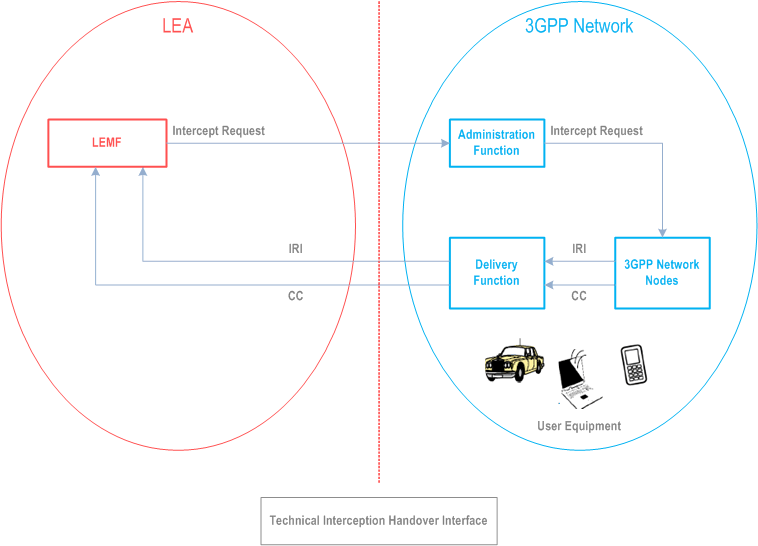
5.1.2 General principles p. 9
A 3GPP network shall provide access to the intercepted Content of Communications (CC) and the Intercept Related Information (IRI) of the mobile target and services related to the target (e.g. Call Forwarding) on behalf of Law Enforcement Agencies (LEAs).
A target of a given 3GPP network can be a user subscribed to and operating in that 3GPP network, a user equipment operating in that 3GPP network (which is either the HPLMN or a VPLMN), or a user roaming from another 3GPP network or from any other network capable of using that 3GPP network. The intercepted CC and the IRI can only be delivered for activities on that given 3GPP network.
Interception may be performed in the network access (all or selected APNs) and/or by intercepting a specific service at the application layer (e.g. VoIP). When interception is done on a per-service basis, only the IRI and CC defined for that service shall be delivered to the LEA, if authorized. To the extent that this is feasible, the intercept shall not include separated services not authorized by the warrant and provided by the same CSP. National regulations will define the service to be intercepted.
For interception, there needs to be a means of identifying the target, correspondent and initiator and related parties of any targeted communication. A means shall exist for the operator to intercept communications based on long term or permanent identifiers associated with a target service or equipment, as identified by the LEA. To achieve interception, the operator may need to translate these into further associated identifiers, in order to identify the data to be intercepted. Target identities used for interception for each domain and service are target service and equipment associated with target use or any derived IDs from such elements that are to be defined in TS 33.107 and TS 33.108. Examples of these identities are IMSI, MSISDN, NAI, Tel URI, SIP URI, for the target service and IMEI, MAC for the equipment.
In many cases, national regulation will require that LI activity is performed entirely within a particular legal jurisdiction, in line with the requirements in 5.1.2 and 5.1.4.
It is not permitted for a CSP to rely on another CSP or jurisdiction to ensure LI activity can occur. For example, a serving network shall not share LI target identities with a home network in the case of roaming or vice versa (as described in clause 5.1.4).
When encryption is provided and managed by the network, it shall be a national option as to whether the network provides the intercepted communication to the LEA decrypted, or encrypted with keys and additional information to make decryption possible. End-to-end encryption implemented in the user equipment based on encryption features provided by the operator is considered to be a network-managed encryption and is subject to the same requirements. See subclause 5.7 for additional requirements.
Encryption not provided or managed by the network, e.g. user provided end-to-end encryption, cannot be removed by the network. In the case that the Communication Service Provider (CSP) provides encryption keys to the subscriber or customer but does not provide the encryption itself, the CSP shall provide the keys to the LEA if required by national regulations.
When compression is provided and managed by the network, it shall be a national option as to whether the network provides the intercepted communication to the LEA decompressed, or compressed with information to make decompression possible.
When encoding is provided and managed by the network, it shall be a national option as to whether the network provides the intercepted communication to the LEA decoded, or encoded with capability (e.g., codec information) to make decoding possible.
Location Dependent Interception, (LDI) allows a 3GPP network to service multiple interception jurisdictions within its service area. Multiple law enforcement agencies with their own interception areas can be served by the 3GPP network. All the information or rules given for interception within a 3GPP network apply to interception within an Interception Area (IA) when LDI is invoked. A target may be marked in one or more different IAs within the same 3GPP network. Interception is neither required nor prohibited by this standard when LDI is active and the location of the target is unknown or unavailable.
National regulations may require that an operator is able to intercept any communication passing through its network based on any visible identity not connected to the operator network. It shall be based on a match between this target identity and identity type (e.g. IMPU) with the detected party fields. This identity is referred as a Non-Local Identity.
5.1.3 Applicability to telecommunication services p. 10
The requirement for lawful interception is that all telecommunications services in the 3GPP network standards should be capable of meeting the requirements within this document.
It is a national option that LI, as delivered to the LEMF, may be restricted to specific target subscribed services offered by the CSP or third party providers with a service level agreement with the CSP.
5.1.4 Interception within the Home and Visited Networks for roaming scenarios |R5| p. 10
The requirements in this clause are additional to the requirements described elsewhere in this specification which apply to the home network in a roaming scenario.
National regulations cover the definition of services and the definition of service provider categories which are subject to LI obligations. This can include how and which IMS services are considered to be covered. For the purpose of roaming, IMS VoIP Service or other 3GPP operator services (CS voice replacement) shall be considered equivalent to a CS voice service and therefore all requirements applicable to legacy CS voice (e.g. interception of voice in isolation from other services) shall be applicable to IMS VoIP Service or other equivalent services.
It shall be possible to intercept all basic voice, data and messaging services provided to a target by a network. The visited network shall be able to support the interception of all services without home network assistance or visibility, using the identifiers provided by an LEA as described in clause 5.1.2. However, the visited network is not required to be able to intercept supplementary services (e.g. voicemail, home network based call forwarding) or 3rd party services not directly provided by the visited network. However, national regulation may specify minimum LI capabilities, if such services are in the visited network then they shall be considered in scope for interception (subject to an applicable lawful authorisation). National regulations may require interception to take place in the home network for outbound roamers, where the user session is routed via the home network. There is no requirement to force traffic to the home network for this purpose.
National regulations may limit delivery of communications (CC and communications-associated IRI) of an outbound international roaming target by the HPLMN based on roaming specific interception constraints (e.g., roaming outside national border). To support these scenarios, it is a national option for the HPLMN to be able to support a mechanism to apply on a per-warrant/per-intercept to limit the delivery of the communications (CC and communications-associated IRI) to LE of an outbound international roaming target based on roaming specific interception constraints (e.g., roaming outside a national border). The default setting is determined based on a national option. Communications originated by the roaming target are subject to this mechanism. Communications incoming to the target that are answered by the target are subject to this mechanism. Communications incoming to the target that are not answered by the target (e.g., due to call forwarding) are not subject to this mechanism. Non-communications-associated IRI (e.g., serving system event) are not affected by this requirement.
All these requirements are based on conditions and definitions contained in national regulations.
5.2 Normal operation p. 11
This section gives the expected operation for lawful interception.
5.2.1 Intercept administration requirements p. 11
As depicted in Figure 1, the Law Enforcement Agency (LEA) provides the intercept request (e.g., lawful authorization or warrant) to the CSP. The intercept request identifies, at a minimum, the target, the type of intercept (i.e., IRI-only, or IRI and CC); the service to be intercepted (e.g. 3G PS network access(es) and/ or the services (e.g. VoIP)) that is authorized, the authorized period for interception, and the LEA delivery address(es) for the intercepted information
In other situations the CC-delivery may provide metadata not sent in the IRI. In case of a IRI only intercept the CC-delivery may take place without the actual content.
It is upon national regulations to implement any of these options.
The CSP shall securely administer the intercept (e.g., to activate, deactivate, show, or list targets) within the 3GPP network as quickly as possible. The CSP's administration function shall use appropriate authentication and audit procedures. When LDI is used, the administration function shall allow specific IAs to be associated with targets.
5.2.1.1 Activation of LI p. 11
For the specified target and based on the warrant, the 3GPP network shall activate the delivery of either IRI, or both the IRI and the CC to the designated LEA destination addresses.
5.2.1.2 Deactivation of LI p. 11
As a result of deactivation, the 3GPP network shall to stop all, or a part of, interception activities for the specified target.
5.2.1.3 Security of processes p. 12
The intercept function shall only be accessible by authorised personnel.
Only authorised personnel can be aware that an intercept function has been activated on a target. No indication shall be given to any person except authorised personnel that the intercept function has been activated on a target. To be effective, interception must take place without the knowledge of any party to the communication.
Authentication, encryption, log files and other mechanisms may be used to maintain security in the system.
CSPs shall ensure that its equipment, facilities, or services that provide a subscriber with the ability to originate, terminate, or direct communications are capable of facilitating authorized communications interceptions and access to intercept related information unobtrusively and with a minimum of interference with any subscriber's telecommunications service and in a manner that protects:
- the privacy and security of communications (both signalling and content of communication) not authorized to be intercepted; and
- information regarding the LEA's interception of communications.
5.2.2 Intercept invocation p. 12
5.2.2.0 General |R11| p. 12
The 3GPP network shall provide the means to allow correlation of different phases (e.g. changes in domains or radio access) of a target's intercepted communication.
5.2.2.1 Invocation events for lawful interception p. 12
In general, Lawful interception should be invoked when the transmission of information or an event takes place that involves the target. Examples of when Lawful interception could be invoked are when:
- A voice call request is originated from, terminated to, or redirected by the target;
- Location information related to the target facility is modified by the subscriber attaching or detaching from the network, or if there is a change in location;
- An SMS transfer is requested - either originated from or terminated to the target;
- An MMS transfer is requested - either originated from or terminated to the target;
- A data packet is transmitted to or from a target;
- A Conference Call is targeted;
- Modification and management of the target's IMS supplementary service settings (e.g., multimedia telephony supplementary service settings as defined in TS 22.173).
5.2.2.2 Invocation and removal of interception regarding services p. 12
The invocation of lawful interception shall not alter the operation of a target's services or provide indication to any party involved in a target's communication or to any others (e.g., non-authorized personnel). Lawful interception shall not alter the services available for the subscribers.
If lawful interception is activated during a CS service, the currently active CS service is not required to be intercepted. If lawful interception is deactivated during a CS service, all ongoing intercepted activities may continue until they are completed.
If lawful interception is activated when a packet switched (PS) service is already in use, the next packets transmitted shall be intercepted. If lawful interception is deactivated during a PS service, the next packets shall not be transmitted to the LEMF.
If lawful interception is activated during an IMS session (including IMS VoIP), the currently active IMS session is required to be intercepted. However, reporting of call information (e.g., identities of parties) by the CSP depends on its availability. If lawful interception is deactivated during an IMS session, interception should be ceased expeditiously.
5.2.2.3 Correlation of information and product p. 13
When only IRI is delivered, an unambiguous correlation shall be established between associated IRI within the single domain for the same communication or session (for example, different legs in CS).
When both IRI and CC are delivered, an unambiguous correlation shall be established between associated IRI, IRI and CC, and associated CC within the single domain (for example different legs in CS or different packets in PS).
Correlation shall be provided to the target's intercepted communications that undergo access technology change or a domain change with Service Continuity.
5.2.2.4 Timing |R11| p. 13
The IRI and CC shall be delivered in as near real time as possible.
5.3 Exceptional procedures p. 13
A failure with the establishment of the connection towards the LEMF shall not result in any interruption of the target's on-going telecommunications service.
It is a national option to have buffering of IRI and/or CC to cope with interruptions in the connection to the LEMF.
5.4 Interworking considerations p. 13
The 3GPP network, home or visited, shall not be responsible to interpret the protocol used by the target, or to remove user level compression or encryption if these were not provided by the 3GPP network.
If the target accesses the 3GPP network via another access network the 3GPP network shall provide the LEA with the identity of the access network (as known by the 3GPP operator). When the target's communications or signalling information is no longer available to the 3GPP network due to redirection or handover to another network operator, it is a national option that the 3GPP network shall provide, when available, the LEA with the identity of the network operator that has access to the target's communications or signalling information.
National regulations may require the home network to report:
- subscriber profile change events such as change of identifiers associated with a target (i.e. HLR/HSS target identity change);
-
location related events related to the target in the visited network:
- register location / registration/access control to a new serving network even if such information is coming from a non 3GPP network; or from the previous serving network, happening after the provisioning of the target by the CSP with the received warrant;
- cancel or purge location;
- location information request or query from other 3GPP networks.
5.5 Charging aspects p. 14
The 3GPP network shall be capable of producing charging data related to interception, including the following mechanisms:
- Use of network resources;
- Activation and deactivation of the target;
- Every intercept invocation;
- Flat rate charging.
5.6 Minimum service requirements p. 14
Quality of service (QoS), capacity, and, integrity of the delivered IRI and CC are the subject of bilateral agreement between the relevant authorities and the CSP. Security is an attribute of the negotiated delivery mechanism between the CSP and the LEA. The QoS towards the delivery function provided by the network must be at a minimum, the same QoS as what the network provides to the target.
The LI service's need to provide high availability and high reliability of the near-real-time transport mechanism of the LI data from the CSP to LEMF is subject to bilateral agreement between the relevant authorities and the CSP.
5.7 LI Requirements for encrypted services |R10| p. 14
Clause 5.1.2 provides a general description of requirements relating to network applied encryption. The additional requirements in this section do not apply where encryption is provided by the network between any network nodes or user equipment (e.g., hop by hop IMS signaling security or End to Access Edge radio bearer encryption), where this encryption does not affect the ability of the core network to perform interception according to the requirements provided by this specification. In addition to the general requirments, the following additonal LI requirements shall apply to network provided and/or network administered end to end or end to middle encryption, where this encryption prevents en-clair capture of communications required to be intercepted.
-
When an encryption service is provided by the PLMN, lawful interception shall take place as for an unencrypted communications.
- In addition, encrypted communications shall be decrypted, or the decryption keys and any required associated information (see Note 0) shall be provided to the LEMF;
- For the specific case where a key server based solution is used, it is a national option for the operator to make keys and any associated information (see Note 0) directly available to the LEMF to support the decryption of communications.
-
Interception shall be performed in such a manner as to avoid detectability by the Target or others. In particular:
- There shall be no significant difference in latency during call setup or during communications compared to a non-intercepted communications;
- Interception of a Target shall not prevent the use of key exchange applications which provide a user key confirmation mechanism;
- Should interception fail during a call (or during call setup), the call shall be unaffected.
- Where the CSP provides decryption of the communication, it is the operator's choice where in the network this decryption is performed. However, following decryption, all IRI and CC shall be provided to the LEMF using handover mechanisms as per an unencrypted communication.
- An encryption solution shall not prohibit commencement of Interception and decryption of an existing communication.
- If key material and any associated information are available, it shall be possible to retrospectively decrypt encrypted communications.
5.8 Lawful Interception for Customized Alerting Tone (CAT) |R10| p. 15
CAT is a service defined in TS 22.182, TR 23.872, TS 24.182, and TR 29.882. The target may participate in the service as either the calling or the called party. The CSP providing the CAT service, and doing the interception, should report the following:
- When the target activates, modifies (e.g., changes to content, content descriptors, and timing descriptors), and deactivates CAT settings;
- When the target invokes the function of copying of another subscriber's CAT;
- When the target invokes the up loading or down loading CAT and is not part of CAT delivery to the calling party, the CAT should be delivered to the LEMF;
- The identity whose CAT is played to the target.
- The CAT sent to the calling party;
- When another subscriber copies the target's CAT;
- When available, the access method (e.g., via UE or web) the target used to activate, modify, and deactivate their CAT settings.
- "played" as part of the CC, during a call set up or;
- Delivered as a file in the IRI Record.
5.9 Lawful Interception for Customized Ringing Signal (CRS) |R10| p. 15
CRS is a service defined in TS 22.183 and TS 24.183. The target may participate in the service as either the calling or the called party. The CSP providing the CRS service, and doing the interception, should report the following:
- The CRS, when invoked by the target, is sent to the called party;
- When the target activates, modifies (e.g., changes to content, content descriptors, and timing descriptors), and deactivates their CRS settings;
- When the target invokes the function of copying another subscriber's CRS;
- When the target invokes the up loading or down loading CRS, and is not part of CRS delivery to the called party the CRS should be delivered;
- The identity whose CRS is played to the target.
- When another subscriber copies the target's CRS;
- When available, the access method (e.g., via UE or web) the target used to activate, modify, and deactivate their CRS settings.
- "played" as part of the CC, during a call set up or;
- Delivered as a file in the IRI Record.
5.10 Lawful Interception for Home Node B and Home enhanced Node B (H(e)NB) |R10| p. 16
HNB and HeNB are jointly referred to as H(e)NB, as defined in TS 22.220. The location of the H(e)NB is the location information used by the operator to verify the location for H(e)NB activation.
For the purpose of LI, a target may be a user or user equipment attached to a H(e)NB, a Closed Subscriber Group (CSG), or it is a national option to allow targeting a H(e)NB itself.
The LI requirements for H(e)NB local routing, selected IP traffic offload (SIPTO) or local IP access (LIPA) are FFS.
Interception should be done in such a manner to avoid detectability by the target or others.
When a target receives service from the PLMN via a H(e)NB, the following applies:
- the interception capabilities shall take place as for normal PLMN use;
- H(e)NB information (e.g., location and identification) shall also be provided to the LEMF;
- If available, the location reported for the target attached to a H(eNB) is the H(e)NB's location;
- Target attachment to the H(e)NB and handovers to/from the H(e)NB shall be reported to the LEMF;
- There may be national requirements to identify specific information that is required to be reported.
- modifications (e.g., additions, deletions, changes in time limits for temporary CSG Members) of the CSG list for the H(e)NB;
- When available, the access method (e.g. via UE or web) the H(e)NB Hosting Party used to modify the CSG list, if multiple access methods are allowed;
- CSG member's handovers to/from the H(e)NB;
- CSG members attachments to the H(e)NB;
- CSG members communications via the H(e)NB;
- It is a national option whether interception on CSG members' communications continues after handover occurs from the H(e)NB.
- activation and deactivation of the targeted H(e)NB;
- IP address information regarding the secure tunnel endpoints between the H(e)NB and the Femto Security Gateway in the home network;
- modifications (e.g., additions, deletions, changes in time limits for temporary CSG Members) of the CSG list for the H(e)NB;
- When available, the access method (e.g. via UE or web) the target used for the modification of the CSG list, if multiple access methods are allowed;
- handovers to/from the H(e)NB;
- UE registrations on the H(e)NB;
- communications via the H(e)NB;
- It is a national option whether interception on H(e)NB communications continues after handover occurs from the H(e)NB.
5.11 Location information |R11| p. 17
5.11.1 General |R13| p. 17
Depending on national requirements, the CSP may be required to report the location of the Target at the beginning and end of CS calls and PS and IMS sessions on a per warrant or per intercept basis. It may also be a national requirement for the CSP to report the location of the Target :
- during on-going communications;
- for any mobility management event detected in the 3GPP core network which includes a target's location change or update.
5.11.2 Location Services |R13| p. 17
In addition to the 3GPP network derived or verified location information as described in 5.11.1. target location information from Location Services (LCS, as described in TS 22.071 and TS 23.271) may be used additionally to provide location information to the LEMF if available. Additional requirements applicable are in Annex B.
5.12 LI requirements for IMS VoIP Service |R11| p. 18
The 3GPP network shall be able to support the delivery of IMS VoIP, and the IMS VoIP supplementary services (e.g., call forwarding), to the LEMF via one of the following two methods:
- Intercepted IMS VoIP communications (e.g. IRI or IRI/CC) are delivered separately from other IMS services;
- Intercepted IMS VoIP communications are delivered as part of all other services.
- Location information shall be able to be reported to the LEMF;
- If for a given implementation, the IRI related to the CC is not delivered in near real time (within the time delay allowance defined by national regulation), then the media related information (e.g. SDP) shall be delivered along with the CC to allow the CC content to be decoded or interpreted,without needing to wait for the IRI;
- If available, activation or modifications of IMS supplementary services shall be reported to LEMF (if authorized).
5.13 Delivery requirements for messaging |R12| p. 18
The 3GPP network shall be able to support the separate delivery of intercept information (IRI or IRI/CC) for messaging services, to the LEMF from other targeted services. This requirement is applicable for the following messaging services:
- SMS (TS 23.040); and
- MMS ([22]).
5.14 LI requirements for management of IMS supplementary services settings |R12| p. 18
The IMS network and related service platforms shall be able to support the reporting of IRI for the modification and management of the target's IMS supplementary services settings.
5.15 LI requirements for IMS Video Service |R14| p. 18
In case of IMS video service, all clause 5.12 requirements shall apply.
5.16 LI requirements for IMS based Push-to-Talk |R14| p. 18
The 3GPP network shall be able to support interception of IMS based Push-to-Talk (PTT).
- Services as defined in TS 22.179 or OMA PoC System Description [27] and shall support Location reporting of the target;
- Intercepted IMS PTT communications (e.g. IRI or IRI/CC) shall be able to be delivered separately from other IMS services;
- Intercepted IMS PTT communications media types such as PTT Speech, PTT Audio (e.g. music), Video and Discrete Media (e.g. still image, formatted and non-formatted text, file) shall be able to be delivered as separated services.
6 Handover interface requirements p. 19
This specification is replaced by TS 33.126 from Rel-15 onwards and should only be used as a historical reference to pre Rel-15 LI requirements.
Handover interface requirements are defined in TS 33.108. There may be national or regional specifications (e.g. see ETSI ES 201 671 [4], ETSI ES 201 671 [4][18], ETSI TS 102 232-7 [20] and J STD 025 A [8].