TR 33.810
3G Security; Network Domain Security / Authentication Framework (NDS/AF);
Feasibility Study to support NDS/IP evolution
V6.0.0 (Wzip)
2002/12 27 p.
- Rapporteur:
- Mr. Sahlin, Bengt
Ericsson LM
full Table of Contents for TR 33.810 Word version: 6.0.0
0 Introduction p. 5
For 3GPP systems there is a need for truly scalable entity Authentication Framework (AF) since an increasing number of network elements and interfaces are covered by security mechanisms.
The objective is to develop a highly scalable entity authentication framework for 3GPP network nodes. This framework was developed in the context of the Network Domain Security work items, which effectively limits the scope to the control plane entities of the core network. Thus, the Authentication Framework will provide entity authentication for the nodes that are using NDS/IP.
The study specifically show the benefits of applying NDS/AF to the current NDS/IP domain. The consequences and alternatives are presented along with the pro's and con's. In the PKI-based alternative, this study analyzes how operator CA's can be organized and what are the trust relationships between them. Thus, different trust models and their effects were studied. Additionally, high-level requirements are presented for the used protocols and certificate profiles, to make it possible for operator IPsec and PKI implementations to interoperate.
It should be noted that although there is a strong trend towards PKI systems, this feasibility study does not take it as a self-evident approach for NDS/AF. In other words, the non-PKI approach is also to be studied.
1 Scope p. 6
The scope of this feasibility study is limited to authentication of network elements which are using NDS/IP, and located in the inter-operator domain.
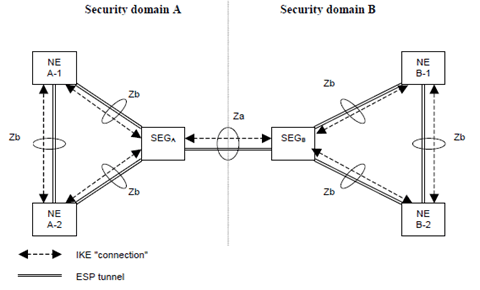
It means that this study concentrates on authentication of Security Gateways (SEG), and the corresponding Za interfaces. Authentication of elements in the intra-operator domain is considered as an internal issue for the operators. This is quite much in line with [6] which states that only Za is mandatory, and that the security domain operator can decide if the Zb-interface is deployed or not, as the Zb-interface is optional for implementation.
However, NDS/AF can easily be adapted to intra-operator use. This is just a simplification of the inter-operator case as all NDS/IP NEs and the PKI infrastructure belong to the same operator. Validity of certificates may be restricted to the operator's domain.
This work might also later be extended to provide entity authentication services to non-control plane nodes, but this has not been studied.
Possible use of multi-purpose PKI solutions (e.g. providing end-user security) for NDS/AF has not been studied. On the contrary, it is recommended to use a dedicated and profiled PKI for NE authentication in NDS/IP. Different applications make different demands on a PKI and it may make sense to build a lightweight PKI for each purpose rather than to build one that solves all problems. Complexity is one of the main impediments to PKI deployment today [11].
The NDS architecture for IP-based protocols is illustrated in Figure 1.