Content for TS 26.531 Word version: 18.2.0
5.7 Procedures for Data Collection AF unsubscription
5.8 Procedures for event consumer authorization
5.7 Procedures for Data Collection AF unsubscription p. 28
Finally:
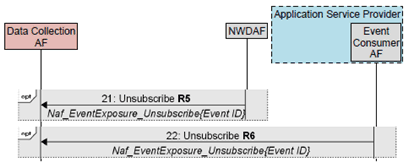
Step 21.
The NWDAF unsubscribes to events from the Data Collection AF by invoking the Naf_EventExposure_Unsubscribe service operation, as defined in clause 5.2.19.2.3 of TS 23.502.
Step 22.
The Event Consumer AF unsubscribes to events from the Data Collection AF by invoking the Naf_EventExposure_Unsubscribe service operation, as defined in clause 5.2.19.2.3 of TS 23.502.
5.8 Procedures for event consumer authorization p. 29
The procedure for authorising access to the events exposed by the Data Collection AF is depicted by the following call flow:
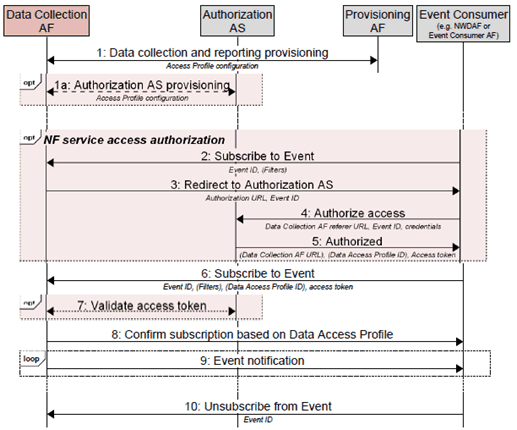
Figure 5.8-1: High-level procedures for event consumer authorization
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
The steps are:
Step 1.
The Provisioning AF provisions the data collection and the report exposure functionality at reference point R1, per the procedures in clause 5.2, including a set of Data Access Profiles.
Step 1a.
The Data Collection AF may provision the Authorization AS with a Data Access Profile configuration corresponding to step 1, including the Data Access Profile ID. The procedures used in this step are outside the scope of standardisation.
Step 2.
An event consumer sends a subscription request to the Data Collection AF to receive events via reference point R5 or R6, per the procedures in clause 5.3, indicating the Event ID of interest and any desired user-, location- and/or application-based filters (see clause 4.6.1).
Step 3.
In return, the Data Collection AF redirects the event consumer to the Authorization AS in order to obtain access.
Step 4.
The event consumer contacts the Authorization AS (according to the procedures for authorization of NF service access defined in clause 13.4 of TS 33.501) with a set of valid credentials.
Step 5.
If access is granted, the Authorization AS responds with an access token that is valid for a specific period of time. The access token may encode a Data Access Profile ID if the authorization applies narrowly. The response may redirect the event consumer to the Data Collection AF using the initial subscription request URL, enhanced with the access token and optionally with the Data Access Profile ID passed in the clear.
Step 6.
The event consumer resends the subscription request (including the Event ID and desired filters, if any) to the Data Collection AF, this time with the access token and, optionally, with the Data Access Profile ID.
Step 7.
The Data Collection AF may verify the access token with the Authorization AS, or it may verify it locally.
Step 8.
If verification is successful, the Data Collection AF approves the subscription request for the requested Access Profile
Step 9.
The Data Collection AF sends event notifications to the event consumer, per the procedures in clause 5.6.
Step 10.
The event consumer cancels its event subscription using the procedures in clause 5.7.