Content for TS 23.222 Word version: 19.3.0
0…
4…
5…
6…
6.3…
6.4…
7…
8…
8.5…
8.8…
8.9…
8.13…
8.17…
8.21…
8.25…
8.26…
8.28…
8.30…
9…
10…
10.4…
10.7…
11…
A
B…
B.2…
B.3…
C…
D…
8.17 CAPIF access control
8.17.1 General
8.17.2 Information flows
8.17.2.1 Service API invocation request
8.17.2.2 Service API invocation response
8.17.3 Procedure
8.18 CAPIF access control with cascaded AEFs
8.18.1 General
8.18.2 Information flows
8.18.2.1 Service API invocation request
8.18.2.2 Service API invocation response
8.18.3 Procedure
8.19 Logging service API invocations
8.19.1 General
8.19.2 Information flows
8.19.2.1 API invocation log request
8.19.2.2 API invocation log response
8.19.3 Procedure
8.20 Charging the invocation of service APIs
8.20.1 General
8.20.2 Information flows
8.20.3 Procedure
...
...
8.17 CAPIF access control p. 69
8.17.1 General p. 69
The CAPIF controls the access of service API by the API invoker based on policy or usage limits.
8.17.2 Information flows p. 69
8.17.2.1 Service API invocation request p. 69
The information flow service API invocation request from the API invoker to the AEF is service API specific and the complete detail of the service API invocation request is out of scope of the present document. Table 8.17.2.1-1 describes only the CAPIF related information elements which are included in the service API invocation request.
| Information element | Status | Description |
|---|---|---|
| API invoker identity information | M | The information that determines the identity of the API invoker |
| Authorization information | O (see NOTE) | The authorization information obtained before initiating the service API invocation request |
| Service API identification | M | The identification information of the service API for which invocation is requested. The service API identification is part of the specific service API invocation request. |
|
NOTE:
The inclusion of this information element depends on the chosen solution for authorization.
|
||
8.17.2.2 Service API invocation response p. 70
The information flow service API invocation response from the AEF to the API invoker is service API specific and the complete detail of the service API invocation response is out of scope of the present document. Table 8.17.2.2-1 describes only the CAPIF related information elements which are included in the service API invocation response.
| Information element | Status | Description |
|---|---|---|
| Result | M | Indicates the success or failure of service API invocation. |
8.17.3 Procedure p. 70
Figure 8.17.3-1 illustrates the procedure for service API access control.
Pre-conditions:
- The API invoker has performed the service API discovery and received the details of the service API which includes the information about the service communication entry point of the AEF in the CAPIF.
- The API invoker is authenticated and authorized to use the service API.
- The AEF in the CAPIF is configured with at least one access policy to be applied to the service API invocation corresponding to the API invoker and service API.
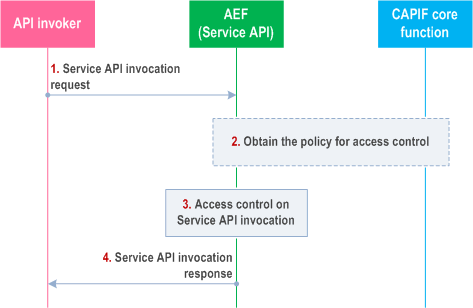
Step 1.
The API invoker performs service API invocation according to the interface of the service API by sending a service API invocation request towards the AEF which exposes the service API towards the API invoker. The AEF acts as an access control entity.
Step 2.
If the access control policy is not configured with AEF, then the AEF may obtain the access control policy configuration from the CAPIF core function.
Step 3.
Upon receiving the service API invocation request from the API invoker, the AEF checks for configuration for access control. As per the configuration for access control, the AEF performs access control on the service API invocation request as per the operator policy.
Step 4.
The API invoker receives a service API invocation response for service API invocation from the AEF providing the service API.
8.18 CAPIF access control with cascaded AEFs p. 71
8.18.1 General p. 71
The procedure in this subclause corresponds to the architectural requirements related to some common access control requirements for service API invocations. It provides access control, based on two cascaded API Exposing Function (AEF) instances. While one AEF instance provides the entry point for the service API and acts as access controller, further AEF instances deliver the functionality of the actual service APIs.
8.18.2 Information flows p. 71
8.18.2.1 Service API invocation request p. 71
The information flow service API invocation request from the API invoker to the AEF and between AEFs is service API specific and the complete detail of the service API invocation request is out of scope of the present document. Table 8.17.2.1-1 describes the CAPIF related information elements which are included in the service API invocation request.
8.18.2.2 Service API invocation response p. 71
The information flow service API invocation response from the AEF to the API invoker and between AEFs is service API specific and the complete detail of the service API invocation response is out of scope of the present document. Table 8.17.2.2-1 describes the CAPIF related information elements which are included in the service API invocation response.
8.18.3 Procedure p. 71
Figure 8.18.3-1 illustrates the procedure for CAPIF access control.
Pre-conditions:
- The API invoker has performed the service discovery and received the details of the service API which includes the information about the service communication entry point of the AEF-1 in the CAPIF.
- The API invoker is authenticated and authorized to use the service API.
- The AEF-1 in the CAPIF is configured with at least one access policy to be applied to the service API invocation corresponding to the API invoker and service API.
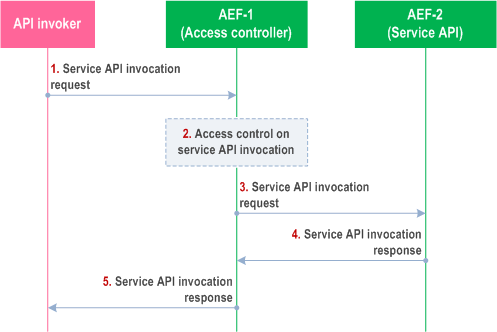
Step 1.
The API invoker performs service API invocation according to the interface of the service API by sending a service API invocation request towards the AEF-1 which exposes the service API towards the API invoker, and acts as access control entity.
Step 2.
Upon receiving the service API invocation request from the API invoker, the AEF-1 checks for configuration for access control. As per the configuration for access control, the AEF-1 performs access control on the service API invocation as per the operator policy.
Step 3.
The AEF-1 forwards the incoming service API invocation request to the service API provided by AEF-2.
Step 4.
The AEF-1 receives a service API invocation response for service API invocation from AEF-2.
Step 5.
The AEF-1 resolves the destination API invoker address and modifies the source address information of AEF-2 within the service API invocation response and forwards the service API invocation response to the API invoker.
8.19 Logging service API invocations p. 72
8.19.1 General p. 72
The procedure in this subclause corresponds to the architectural requirements for logging service API invocations at AEF. The AEF can be within PLMN trust domain or within 3rd party trust domain.
8.19.2 Information flows p. 72
8.19.2.1 API invocation log request p. 72
Table 8.19.2.1-1 describes the information flow API invocation log request from the API exposing function to the CAPIF core function.
| Information element | Status | Description |
|---|---|---|
| API exposing identity information | M | Identity information of the AEF logging service API(s) invocations |
| API invocation log information | M | API invocation log information such as API invoker's ID, IP address, service API name, version, invoked operation, input parameters, invocation result, time stamp information, Network Slice Info |
8.19.2.2 API invocation log response p. 73
Table 8.19.2.2-1 describes the information flow API invocation log response from the CAPIF core function to the API exposing function.
| Information element | Status | Description |
|---|---|---|
| Result | M | Indicates the success or failure of API(s) invocation log request |
8.19.3 Procedure p. 73
Figure 8.19.3-1 illustrates the procedure for logging service API invocations at AEF.
Pre-conditions:
- The API invoker(s) has invoked certain service API(s).
- Authorization details of the AEF are available with the CAPIF core function.
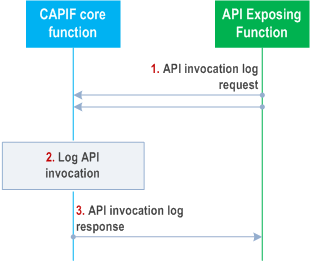
Step 1.
Upon invocation of service API(s) from one more API invokers, the AEF triggers API invocation log request towards the CAPIF core function.
Step 2.
The CAPIF core function makes a log entry and stores the information e.g. for charging purposes, for access by authorized users and entities.
Step 3.
AEF receives the API invocation log response from the CAPIF core function.
8.20 Charging the invocation of service APIs p. 73
8.20.1 General p. 73
The procedure in this subclause corresponds to the architectural requirements for charging the invocation of service APIs. The AEF can be within PLMN trust domain or within 3rd party trust domain.
8.20.2 Information flows p. 74
8.20.3 Procedure p. 74
Figure 8.20.3-1 illustrates the procedure for charging the invocation of service APIs.
Pre-condition:
- Authorization details of the AEF are available with the CAPIF core function.
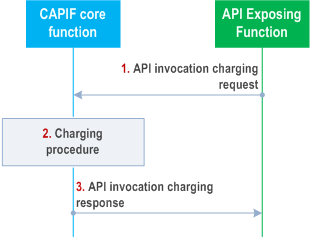
Step 1.
Upon invocation of service API(s) from one more API invokers, the AEF triggers an API invocation charging request and includes API invoker information (e.g. invoker's ID and IP address, location, timestamp) and service API information (e.g. service API name and version, invoked operation, input parameters, invocation result), Network Slice Info of the service API towards the CAPIF core function.
Step 2.
The CAPIF core function performs a charging procedure which includes storing the information for access by authorized API management.
Step 3.
The AEF receives the API invocation charging response from the CAPIF core function.