Content for TS 22.259 Word version: 18.0.1
A Use cases
A.1 Use case: Connection between PNEs of a PN
A.2 Use case of UE-PN connection
A.2a PN Access control: Parental control
...
...
A Use cases p. 17
A.1 Use case: Connection between PNEs of a PN p. 17
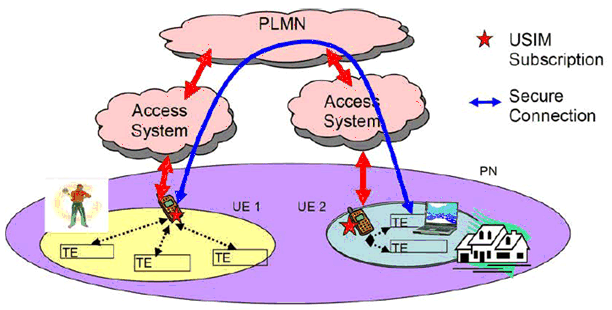
PNM allows the communication between a PNE and PNEs of other UEs/PANs belonging to the same PN. For this purpose it shall be possible to establish a secure link between the PNEs of a PN. This is enabled by establishing secure links among locally connected devices of a PAN. In the example in Figure 4 the PNEs have established a secure link. Through this secure link, a user is able to gain access from the ME in UE1 to the TE in UE2 at home and monitor the heating or burglar alarm system while away from home, therefore enabling the ME to be the active PNE for termination of the alarm service remotely. Figure 5 explains the secure PNE-PNE communications.
The TE in UE2 has an own PNE Identifier that allows the ME in UE1 to identify and to directly communicate with the TE.
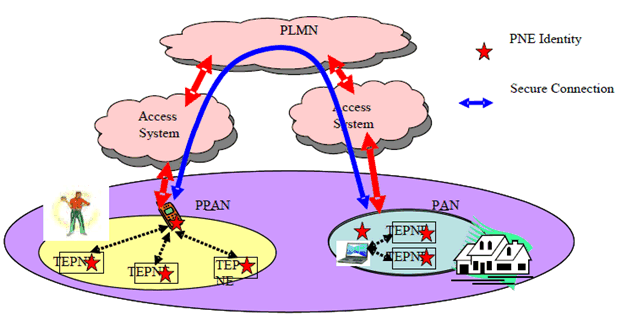
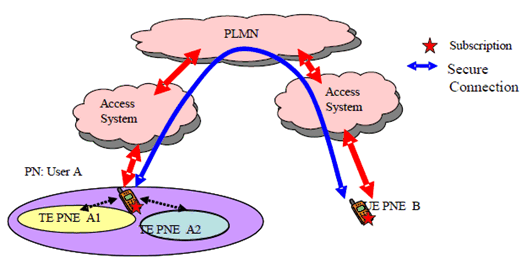
A.2 Use case of UE-PN connection p. 18
Personal UE Networks security requirements state that registration of a PNE to a PN requires the consent of the owner of the USIM associated with the PLMN. The description here concerns access of a Personal Network by a PNE external to that Personal Network. In the case of user A wishing to allow PNE B to register into his PN as a Guest UE, the user controls access to his PN, in other words PNM protects the privacy of A's PN. For example in Figure 6, PNE B (ME) may only be allowed to access TE A1 and this is controlled by the user, and enabled by procedures. PNE B may access A's PN by appropriate means, e.g. an "invite function".
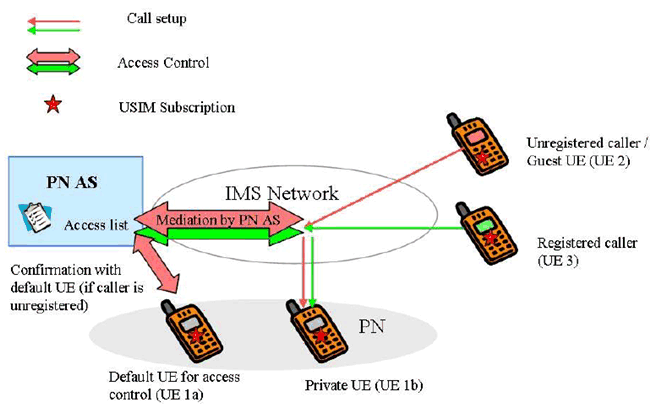
A.2a PN Access control: Parental control p. 19
Alice has subscribed to PNM private network service. She has two UEs with her in the PN - UE 1a and UE 1b. She decides to give UE 1b to her son Bob. Bob is still a young kid and Alice worries about him getting calls from strangers. So she registers her UE (UE 1a) as default UE for access control. She then creates an access list that contains a list of registered callers (Guest UEs). Any calls from the registered callers (e.g. UE 3) or Guests are allowed to go through to the private UE (Bob's UE) directly. In case of unregistered callers (e.g. UE 2), the PN AS rejects the call directly or the PN Server queries Alice (UE 1a) whether the call can be continued. Alice can respond by allowing or disallowing (cancelling) the call. In addition, she may register the unregistered caller dynamically (on the fly) during session initiation procedures itself.