Content for TS 33.310 Word version: 18.2.0
7 Detailed description of architecture and mechanisms
7.1 Repositories
7.2 Life cycle management
7.3 Cross-certification
7.4 Revoking a SEG/TLS CA cross-certificate
7.5 Establishing secure connections between NDS/IP end entities using IKE on the Za interface
7.5a Establishing secure connections using TLS
7.5b Establishing secure connections between NDS/IP entities on the Zb interface
7.6 CRL management
...
...
7 Detailed description of architecture and mechanisms p. 34
7.1 Repositories p. 34
During secure connection establishment, each NE, SEG or TLS entity has to verify the validity of its peer's certificate according to clause 5.2.2. Any certificate could be invalid because it was revoked (and replaced by a new one) or a NE, SEG, TLS entity or operator has been deregistered.
Consider secure connection establishment between PeerA in network A and PeerB in network B.
PeerB has to verify that:
a)
PeerA performs the same checks from its own perspective.
Check a) can be performed by querying the local CRL or OCSP server. For check b), a CRL or OCSP server of the PeerA's CA shall be queried. At this point of time, the secure connection is not yet available, therefore the public CRL or OCSP server of the PeerA's CA shall be accessible without relying on a secure connection.
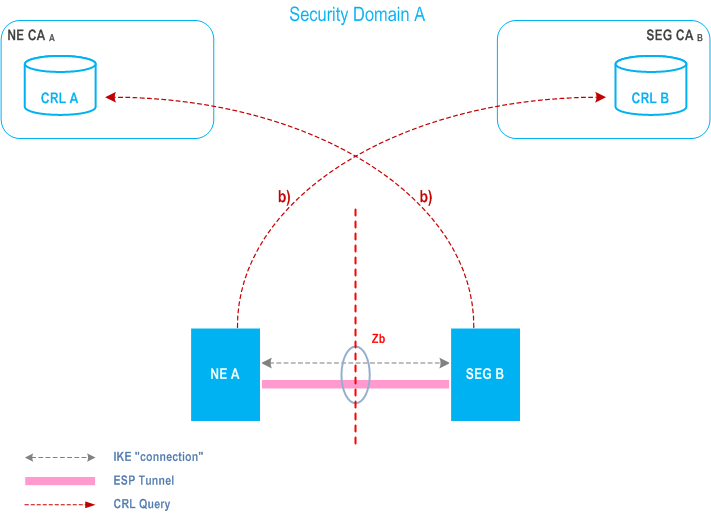
Figure 4 and Figure 5 illustrate the repositories and the above-mentioned steps a) - c). The local Certificate Repository (CR) contains cross-certificates for SEG CAs and possibly cross-certificates for TLS CAs if these are not locally stored in the TLS entities. Local CRLs contains SEG CA and TLS CA cross-certificate revocations, and the public CRL or OCSP server contain revocations of SEG, TLS entity, SEG CA, and TLS CA certificates, and can be accessed by other operators.
An operator's internal repository may contain the revocations of NE and NE CA if not contained in the Public CRL or OCSP repository.
the cross-certificate of the PeerA's CAA is still valid;
b)
the certificate of PeerA is still valid,
and be able to:
c)
fetch the cross-certificate of PeerA CAA (if not found in PeerA's cache or local store).
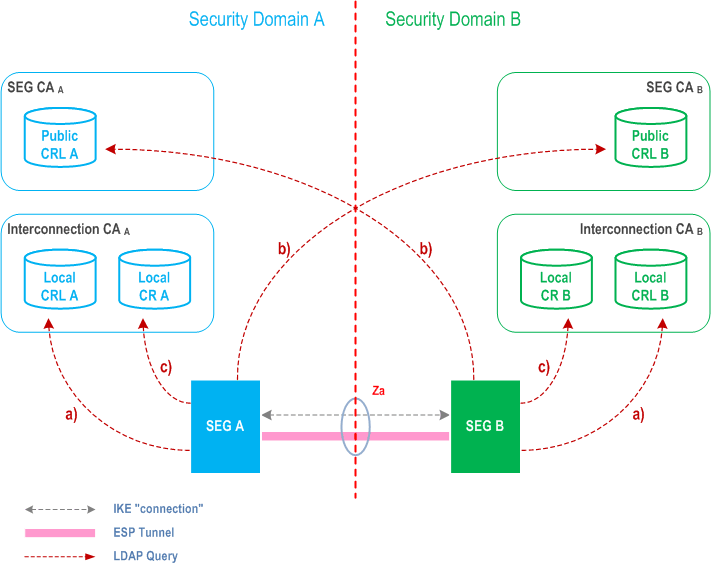
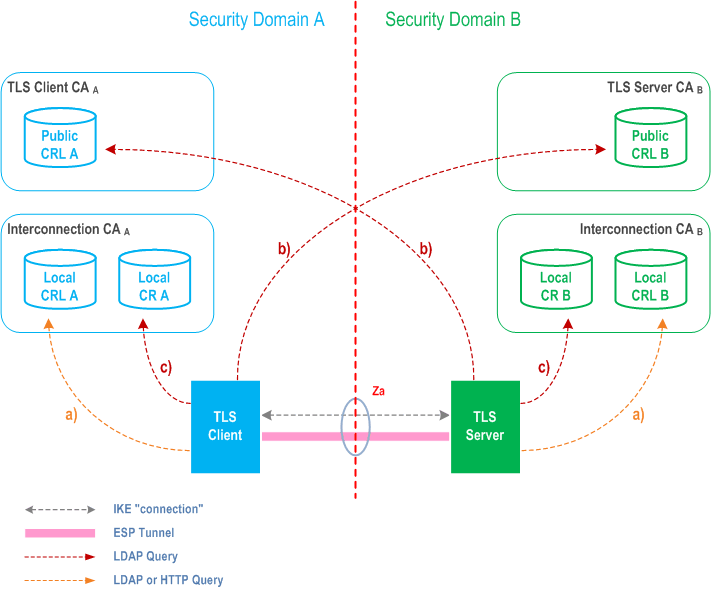
If the SEG CA, TLS CA or Interconnection CA are combined then the public and local repositories of the CA may be implemented as separate databases or as a single database which is accessible via two different interfaces. Access to the "public" CRL or OCSP server is public with respect to the interconnecting transport network (e.g. GRX). The public CRL should be adequately protected (e.g by a firewall) and the owner of the public CRL or OCSP may limit access to it according to his interconnect agreements. Access to a public CRL or OCSP server database does not need to be secured.
SEGs shall use LDAP to access the CRL and cross-certificate repositories. TLS entities shall use LDAP or HTTP to access the CRL repositories. TLS entities may use LDAP to access the cross-certificate repositories, if the cross certificates are not stored locally in the TLS entity. NE's may use LDAP or HTTP to access the CRL repositories. OCSP servers shall always be accessed via HTTP.
7.2 Life cycle management p. 37
Certificate Management Protocol v2 (CMPv2) [4] shall be the supported protocol to provide certificate lifecycle management capabilities for SEGs. All SEGs and SEG CAs shall support initial enrolment by the SEG to the SEG CA via CMPv2, i.e. receiving a certificate from the SEG CA, and updating the key of the certificate via CMPv2 before the certificate expires.
Certificate Management Protocol v2 (CMPv2) [4] should be the supported protocol to provide certificate lifecycle management capabilities for TLS entities. All TLS entities and TLS CAs should support initial enrolment by the TLS entity to the TLS CA via CMPv2, i.e. receiving a certificate from the TLS CA, and updating the key of the certificate via CMPv2 before the certificate expires.
Certificate Management Protocol v2 (CMPv2) [4] shall be the supported protocol to provide certificate lifecycle management capabilities for NEs. All NEs and NE CAs shall support initial enrolment by the NE to the NE CA via CMPv2, i.e. receiving a certificate from the NE CA, and updating the key of the certificate via CMPv2 before the certificate expires.
Enrolling a certificate to a SEG, NE or TLS entity is an operation that may be done more often than inter-operator cross-certifications, thus more automation could be required by the operator than is possible with a PKCS#10 approach. However, also manual SEG and NE certificate installation using PKCS#10 formats shall be supported. It should be also noted that the lifetime of a SEG CA cross-certificate is considerably longer than the lifetime of a SEG certificate.
7.3 Cross-certification p. 38
Both operators use the following procedure to create a SEG CA or TLS CA cross-certificate:
- The SEG CA or TLS CA creates a PKCS#10 certificate request, and sends it to the other operator;
- The Interconnection CA receives a similar request from the other operator;
- The Interconnection CA accepts the request and creates a new cross-certificate;
- The SEG CA cross-certificate is stored once into the local CR of the Interconnection CA and LDAP is used to fetch cross-certificates. The TLS CA cross-certificate may be stored once into the local CR of the Interconnection CA and LDAP is used to fetch cross-certificates. Alternatively the TLS CA cross certificate may be locally stored in the TLS entities.
7.4 Revoking a SEG/TLS CA cross-certificate p. 38
The following procedure is used to revoke a SEG CA cross-certificate:
- The cross-certificate is added into the Interconnection CA's CRL or OCSP server;
- The cross-certificate is removed from the Interconnection CA's CR.
- The cross-certificate is added into the Interconnection CA's CRL or OCSP server;
- If the TLS CA cross certificates are stored in the Interconnection CA's CR, then the cross-certificate is removed.
- If the TLS CA cross-certificates are stored locally in the TLS entities, then the locally stored cross-certificates are deleted in the TLS entities.
7.5 Establishing secure connections between NDS/IP end entities using IKE on the Za interface p. 38
Certificate based authentication during the IKEv2 IKE_INIT_SA/IKE_AUTH exchanges is shown in Figure 4 above. The SEGa uses the following procedure to authenticate SEGb:
- SEGa requests SEGb's certificate using the CERTREQ payload;
- SEGa receives SEGb's certificate inside the CERT payload;
- SEGa authenticates SEGb (verifies signatures);
- SEGa performs a revocation check with CRL or OCSP to verify the status of SEGb's certificate. If the locally cached CRL has expired, SEGa fetches a CRL from the (public) CRL database of SEC CAb before using CRL.
- SEGa uses either the locally cached cross-certificate or fetches the cross-certificate from the (local) Interconnection CAa CR to verify SEGb's certificate;
- SEGa performs a revocation check with CRL or OCSP to verify the status of the SEG CA cross-certificate. If the locally cached CRL has expired, SEGa fetches a CRL from the (local) Interconnection CAa CRL database before using CRL;
- SEG A verifies the cross-certificate for Operator B's SEG CA using Operator A's Interconnection CA's certificate. SEGa verifies the status of the Interconnection CAa certificate if the Interconnection CAa is not a top-level CA, otherwise Interconnection CAa is implicitly trusted;
7.5a Establishing secure connections using TLS |R7| p. 39
The procedure for establishing secure connections using TLS is specified in detail in clause 5.2.2.
7.5b Establishing secure connections between NDS/IP entities on the Zb interface |R8| p. 39
The procedure for establishing secure connections using NDS/IP on the Zb interface is specified in detail in clause 5.2.2.
7.6 CRL management p. 39
NDS/AF compliant SEGs and NEs shall not send an IKEv2 CERTREQ where the Certificate Type is "Certificate Revocation List (CRL)". Receiving NEs and SEGs may ignore this request as clause 6.1.3 specifies that CRLs shall be retrieved via a CRL distribution point.
The CRL issuer (which is in most cases the CA) shall only issue full CRLs. The use of delta CRLs is not allowed because of possible interoperability problems and because in the NDS/AF environment the full CRL is not expected to grow too large. The full CRL shall only contain revoked certificates applicable for use within NDS/AF. The CRL issuer shall issue a CRL also in cases that there are no revoked certificates. A SEG, NE or TLS entity is not obliged to query for a CRL via the CRL Distribution Point if a cached one is still available and valid. If no valid cached CRL is available, the NE, SEG or TLS entity shall fetch a new CRL. If no valid CRL can be fetched, the NE, SEG or TLS entity shall treat this as an error and cancel tunnel establishment.