Content for TS 33.102 Word version: 18.0.0
6.5 Access link data integrity
6.5.1 General
6.5.2 Layer of integrity protection
6.5.3 Data integrity protection method
6.5.4 Input parameters to the integrity algorithm
6.5.5 Integrity key selection
6.5.6 UIA identification
...
...
6.5 Access link data integrity p. 36
6.5.1 General p. 36
Most control signalling information elements that are sent between the MS and the network are considered sensitive and must be integrity protected. A message authentication function shall be applied on these signalling information elements transmitted between the ME and the RNC.
After the RRC connection establishment and execution of the security mode set-up procedure, all dedicated MS <-> network control signalling messages (e.g. RRC, MM, CC, GMM, and SM messages) shall be integrity protected. The Mobility Management layer in the MS supervises that the integrity protection is started (see clause 6.4.5).
All signalling messages except the following ones shall then be integrity protected:
- HANDOVER TO UTRAN COMPLETE
- PAGING TYPE 1
- PUSCH CAPACITY REQUEST
- PHYSICAL SHARED CHANNEL ALLOCATION
- RRC CONNECTION REQUEST
- RRC CONNECTION SETUP
- RRC CONNECTION SETUP COMPLETE
- RRC CONNECTION REJECT
- RRC CONNECTION RELEASE (CCCH only)
- SYSTEM INFORMATION (BROADCAST INFORMATION)
- SYSTEM INFORMATION CHANGE INDICATION
- TRANSPORT FORMAT COMBINATION CONTROL (TM DCCH only)
6.5.2 Layer of integrity protection p. 36
Integrity protection shall be applied at the RRC layer.
6.5.3 Data integrity protection method p. 36
Figure 16 illustrates the use of the integrity algorithm f9 to authenticate the data integrity of a signalling message.
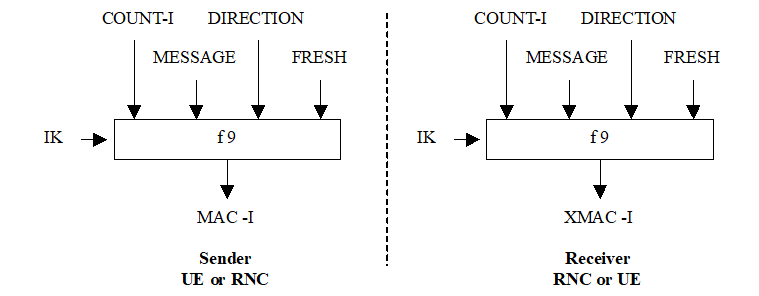
The input parameters to the algorithm are the Integrity Key (IK), the integrity sequence number (COUNT-I), a random value generated by the network side (FRESH), the direction bit DIRECTION and the signalling data MESSAGE. Based on these input parameters the user computes message authentication code for data integrity MAC-I using the integrity algorithm f9. The MAC-I is then appended to the message when sent over the radio access link. The receiver computes XMAC-I on the message received in the same way as the sender computed MAC-I on the message sent and verifies the data integrity of the message by comparing it to the received MAC-I.
6.5.4 Input parameters to the integrity algorithm p. 37
6.5.4.1 COUNT-I p. 37
The integrity sequence number COUNT-I is 32 bits long.
For signalling radio bearers (RB 0-4) there is one COUNT-I value per up-link signalling radio bearer and one COUNT-I value per down-link signalling radio bearer.
COUNT-I is composed of two parts: a "short" sequence number and a "long" sequence number. The "short" sequence number forms the least significant bits of COUNT-I while the "long" sequence number forms the most significant bits of COUNT-I. The "short" sequence number is the 4-bit RRC sequence number (RRC SN) that is available in each RRC PDU. The "long" sequence number is the 28-bit RRC hyper frame number (RRC HFN) which is incremented at each RRC SN cycle.
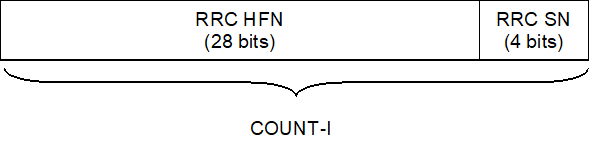
The RRC HFN is initialised by means of the parameter START, which is described in clause 6.4.8. The ME and the RNC then initialise the 20 most significant bits of the RRC HFN to START; the remaining bits of the RRC HFN are initialised to 0.
6.5.4.2 IK p. 37
The integrity key IK is 128 bits long.
There may be one IK for CS connections (IK CS), established between the CS service domain and the user and one IK for PS connections (IK PS) established between the PS service domain and the user. Which integrity key to use for a particular connection is described in 6.5.5.
For UMTS subscribers IK is established during UMTS AKA as the output of the integrity key derivation function f4, that is available in the USIM and in the HLR/AuC. For GSM subscribers, that access the UTRAN, IK is established following GSM AKA and is derived from the GSM cipher key Kc, as described in 6.8.2.
IK is stored in the USIM and a copy is stored in the ME. IK is sent from the USIM to the ME upon request of the ME. The USIM shall send IK under the condition that a valid IK is available. The ME shall trigger a new authentication procedure if the current value of STARTCS or STARTPS in the USIM are not up-to-date or STARTCS or STARTPS have reached THRESHOLD. The ME shall delete IK from memory after power-off as well as after removal of the USIM.
IK is sent from the HLR/AuC to the VLR/SGSN and stored in the VLR/SGSNas part of a quintet. It is sent from the VLR/SGSN to the RNC in the (RANAP) security mode command.
At handover, the IK is transmitted within the network infrastructure from the old RNC to the new RNC, to enable the communication to proceed, and the synchronisation procedure is resumed. The IK remains unchanged at handover, with the exception of SRVCC handover and reverse SRVCC handover.
6.5.4.3 FRESH p. 37
The network-side nonce FRESH is 32 bits long.
There is one FRESH parameter value per user. The input parameter FRESH protects the network against replay of signalling messages by the user. At connection set-up the RNC generates a random value FRESH and sends it to the user in the (RRC) security mode command. The value FRESH is subsequently used by both the network and the user throughout the duration of a single connection. This mechanism assures the network that the user is not replaying any old MAC-Is.
At handover with relocation of the S-RNC, the new S-RNC generates its own value for the FRESH parameter and sends it to the ME in the RRC message that indicates a new UTRAN Radio Network Temporary Identity due to a SRNC relocation (see TS 25.331).
6.5.4.4 DIRECTION p. 38
The direction identifier DIRECTION is 1 bit long.
The direction identifier is input to avoid that the integrity algorithm used to compute the message authentication codes would use an identical set of input parameter values for the up-link and for the down-link messages. The value of the DIRECTION is 0 for messages from UE to RNC and 1 for messages from RNC to UE.
6.5.4.5 MESSAGE p. 38
The signalling message itself with the radio bearer identity. The latter is appended in front of the message. Note that the radio bearer identity is not transmitted with the message but it is needed to avoid that for different instances of message authentication codes the same set of input parameters is used.
6.5.5 Integrity key selection p. 38
There may be one IK for CS connections (IK CS), established between the CS service domain and the user and one IK for PS connections (IK PS) established between the PS service domain and the user.
The data integrity of radio bearers for user data is not protected.
The signalling radio bearers are used for transfer of signalling data for services delivered by both CS and PS service domains. These signalling radio bearers are data integrity protected by the IK of the service domain for which the most recent security mode negotiation took place. This may require that the integrity key of an (already integrity protected) ongoing signalling connection has to be changed, when a new connection is established with another service domain, or when a security mode negotiation follow a re-authentication during an ongoing connection. This change should be completed by the RNC within five seconds after receiving the security mode command from the VLR/SGSN.
6.5.6 UIA identification p. 38
Each UMTS Integrity Algorithm (UIA) will be assigned a 4-bit identifier. Currently, the following values have been defined:
"00012":
The remaining values are not defined.
UEs and RNCs shall implement UIA1 and UIA2.
The use of Kasumi for the integrity protection function f9 is specified in TS 35.201 and TS 35.202. Implementers' test data and design conformance data is provided in TS 35.203 and TS 35.204.
The use of SNOW 3G for the integrity protection function f9 is specified in TS 35.215 and TS 35.216. Implementers' test data and design conformance data is provided in TS 35.217 and TS 35.218.
UIA1, Kasumi.
"00102":
UIA2, SNOW 3G.