Content for TS 28.314 Word version: 18.0.0
0 Introduction
1 Scope
2 References
3 Definitions of terms, symbols and abbreviations
3.1 Terms
3.2 Symbols
3.3 Abbreviations
4 Concepts and background
4.1 Plug and Connect Concept
...
...
0 Introduction p. 5
The present document is part of a TS family covering the 3rd Generation Partnership Project Technical Specification Group Services and System Aspects, Management and orchestration; as identified below:
TS 28.314:
"Plug and Connect; Concepts and requirements".
TS 28.315:
"Plug and Connect; Procedure flows".
TS 28.316:
"Plug and Connect; Data formats".
1 Scope p. 6
The present document specifies concepts, use cases and requirements for Plug and Connect NE in 3GPP systems.
2 References p. 6
The following documents contain provisions which, through reference in this text, constitute provisions of the present document.
- References are either specific (identified by date of publication, edition number, version number, etc.) or non-specific.
- For a specific reference, subsequent revisions do not apply.
- For a non-specific reference, the latest version applies. In the case of a reference to a 3GPP document (including a GSM document), a non-specific reference implicitly refers to the latest version of that document in the same Release as the present document.
[1]
TR 21.905: "Vocabulary for 3GPP Specifications".
[2]
TS 33.310: "Network Domain Security (NDS); Authentication Framework (AF)".
[3]
RFC 4210: "Internet X.509 Public Key Infrastructure Certificate Management Protocol".
[4]
RFC 4211: "Internet X.509 Public Key Infrastructure Certificate Request Message Format (CRMF)".
3 Definitions of terms, symbols and abbreviations p. 6
3.1 Terms p. 6
For the purposes of the present document, the terms given in TR 21.905 and the following apply. A term defined in the present document takes precedence over the definition of the same term, if any, in TR 21.905.
Plug and Connect:
The procedure by which a NE gets basic connectivity information after it is powered up and gets connected to its management system.
Software and Configuration Server (SCS):
A server that provides software and configuration functions for each connected network element.
3.2 Symbols p. 6
Void.
3.3 Abbreviations p. 6
For the purposes of the present document, the abbreviations given in TR 21.905 and the following apply. An abbreviation defined in the present document takes precedence over the definition of the same abbreviation, if any, in TR 21.905.
CA
Certification Authority
CMP
Certificate Management Protocol
DHCP
Dynamic Host Configuration Protocol
DNS
Domain Name System
FQDN
Fully Qualified Domain Name
NAT
Network Address Translation
NE
Network Element
PnC
Plug and Connect
RA
Registration Authority
SCS
Software and Configuration Server
SeGW
Security Gateway
VLAN
Virtual LAN
4 Concepts and background p. 7
4.1 Plug and Connect Concept p. 7
4.1.1 General description p. 7
Plug and connect is a list of procedures for connecting the NE to its management system. The basic steps of Plug and Connect are described in clause 6.1.1.
The entities involved in the PnC concept are NE, DHCP server, DNS Server, Certification Authority server, SCS (including the Initial and Serving SCS that could be the same in certain deployment scenarios), Security Gateway.
4.1.2 Network Scenarios p. 7
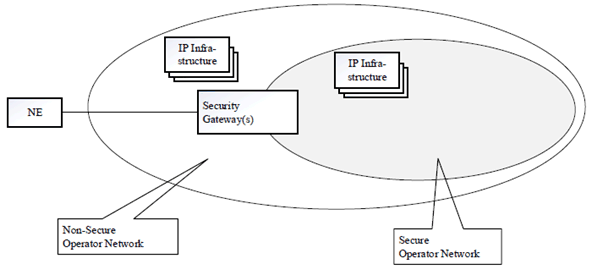
4.1.2.1 NE connected via a Non-Secure, Operator Controlled Network p. 7
An NE is typically connected to the operator's network according to one of the following scenarios:
In Figure 4.1.2.1-1, the NE is connected directly to a network controlled by the operator. The NE can use IP Infrastructure services (DHCP Server, DNS Server, etc.) in the Non-secure Operator Network. The Operator has full control of these nodes. One or more Security Gateways protect the Secure Operator Network from malicious NEs. Within the Secure Operator Network, there are also IP Infrastructure nodes.
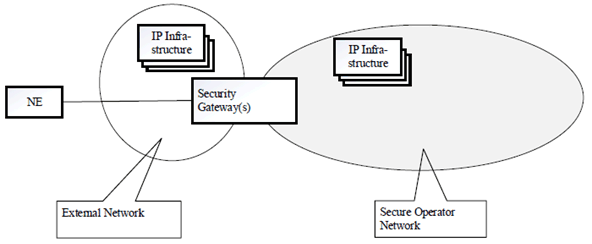
4.1.2.2 NE connected via an External Network p. 7
In Figure 4.1.2.2-1, the NE is connected to a network controlled by an entity external to the Operator. In contrast to the first scenario, the IP Infrastructure nodes in the External Network are not fully controlled by the operator. In both cases, the NE needs to traverse the Security Gateway(s) to access the nodes in the Secure Operator Network.
4.1.3 Security Aspects p. 8
4.1.3.1 Root Certificate Acquisition: p. 8
In accordance to clause 9.2 of TS 33.310 there are two options how to obtain the operator root certificate:
Option 1:
The required pre-provisioning in option 1 is against the basic idea of PnC to minimize pre-provisioning. Therefore from the PnC perspective Option 2 is more interesting. From a security point of view the following considerations are relevant:
The operator root certificate is provisioned in the NE prior to the CMPv2 protocol run.
Option 2:
The operator root certificate is provisioned in the NE during the CMPv2 protocol run (as part of the Initialisation Response).
- Option 2 has the risk that during the CMP initialisation a man-in the middle attack could take place. In order to be successful, such an attack happens timely during the actual CMP initialization run and the attacker has access to the access network between NE and RA/CA. This risk can be assessed as acceptable, given (a) the risks which are present at Options 1's prior provisioning - see below, (b) the short time window of vulnerability, (c) the closed access networks of many operators. In addition, most attacks will only lead to inability of the NE to connect to the network, or to misuse of the new NE by the attacker. The operator should notice it soon if the NE does not connect and will investigate the issue.
- Option 1 avoids the above "time window of vulnerability". On the other hand, it requires pre-provisioning of the operator root certificate, either in factory or on-site by service personnel. There is the risk of a security leak during the provisioning of the root certificate within the vendor / commissioning environment.
4.1.3.2 Number of CA servers p. 8
There could be one or more RA/CA server, e.g. one per NE vendor. If more than one RA/CA server is deployed with one RA/CA server per vendor then the vendor identification would be needed either in the FQDN of the RA server or in the information from the IP AutoConfiguration Service carrying the information about RA/CA server.
4.1.3.3 Number of OAM SeGWs p. 9
There could be one or more OAM SeGW, e.g. one per NE vendor. If more than one OAM SeGW is deployed with one OAM SeGW per vendor then the vendor identification would be needed either in the FQDN of the OAM SeGW or in the information from the IP AutoConfiguration Service carrying the information about OAM SeGW.