TS 22.031
FIGS —
Fraud Information Gathering System –
Stage 1
V18.0.0 (PDF)
2024/03 … p.
V17.0.0
2022/03 13 p.
V16.0.0
2020/06 13 p.
V15.0.0
2018/06 13 p.
V14.0.0
2017/03 13 p.
V13.0.0
2015/12 14 p.
V12.0.0
2014/09 14 p.
V11.0.0
2012/09 14 p.
V10.0.0
2011/04 14 p.
V9.0.0
2009/12 14 p.
V8.0.0
2008/12 14 p.
V7.0.0
2007/06 14 p.
V6.0.0
2005/01 14 p.
V5.0.0
2003/01 14 p.
V4.0.0
2003/01 14 p.
V3.0.0
2003/01 14 p.
GSM Rel-98 v7.1.1
1999/06 14 p.
- Rapporteur:
- Mr. Bleckert, Peter
Ericsson LM
Content for TS 22.031 Word version: 18.0.0
1 Scope p. 5
This Technical Specification specifies the stage 1 description of the Fraud Information Gathering System (FIGS) feature which provides the means for the HPLMN to monitor the activities of its subscribers in a VPLMN.
The purpose of this network feature is to enable the HPLMN to monitor the activities of its subscribers while they are roaming. The VPLMN collects information about a defined set of activities on monitored subscribers and sends this information back to the HPLMN. This enables the HPLMN to clear certain types of calls and so stop fraudulent use of the GSM system.
This specification enables service providers/ network operators to use FIGS, and service limitation controls such as Operator Determined Barring (ODB) and Immediate Service Termination (IST), to limit their financial exposure to subscribers producing large unpaid bills.
HPLMNs may also choose to monitor the activities of its subscribers within the HPLMN.
2 Normative references p. 5
The following documents contain provisions which, through reference in this text, constitute provisions of the present document.
- References are either specific (identified by date of publication, edition number, version number, etc.) or non specific.
- For a specific reference, subsequent revisions do not apply.
- For a non-specific reference, the latest version applies. In the case of a reference to a 3GPP document (including a GSM document), a non-specific reference implicitly refers to the latest version of that document in the same Release as the present document.
3 Definitions and abbreviations p. 5
3.1 Definitions p. 5
For the purposes of this specification the following definitions apply:
A subscriber:
The calling mobile subscriber.
B subscriber:
The mobile subscriber originally called by the A subscriber.
C subscriber:
The subscriber to whom the B subscriber has requested that calls be forwarded. The C subscriber may be fixed or mobile.
call:
both connection-oriented and connectionless services/events.
call information:
information about a call.
call reference:
a reference number for a call that shall remain constant throughout the duration of that call and that shall be unique to that call and the switch on which the call was made for a period of at least one week.
home network:
The home PLMN including non-GSM elements such as the Fraud Detection System (FDS), customer service systems and billing.
monitored activities:
subscriber activities that shall be reported to the HPLMN. These can be call related events (e.g. call-set-up, call termination) or the invocation of call related and call independent supplementary services (e.g. Call Hold, Call Waiting, Call Transfer, Call Forwarding, Unstructured Supplementary Service Data).
3.2 Abbreviations p. 6
Abbreviations used in this specification are also listed in GSM 01.04.
For the purposes of this specification the following abbreviations apply:
FIGS
Fraud Information Gathering System
FDS
Fraud Detection System
IST
Immediate Service Termination
MO
Mobile Originated
MT
Mobile Terminated
CGI
Cell Global Identifier
4 Fraud Information Gathering System high level requirements p. 6
4.1 Description p. 6
It shall be possible for the HPLMN to request the VPLMN to supply certain information about a subscriber from the time the subscriber registers in that VPLMN to the time the last of the monitored activities is finished in that VPLMN, which can be after the subscriber's de-registration from the VPLMN. The information received by the HPLMN shall be passed to the relevant network or service providers and used to instruct the VPLMN to act in an appropriate way.
Fraud information gathering is controlled by the HPLMN and can be activated and deactivated by the HPLMN only.
The information is received in the HPLMN and is forwarded to fraud detection and control systems. Such systems are out of the scope of this standard.
The subscriber is specified by the IMSI or MSISDN.
4.2 Applicability p. 6
This network feature applies to all subscribed Bearer Services and Teleservices and supplementary services of the subscriber. It is not possible to apply FIGS independently to individual Services.
The HPLMN shall be able to specify whether it would like call information on MO calls, MT calls, or both.
4.3 Normal Procedure p. 6
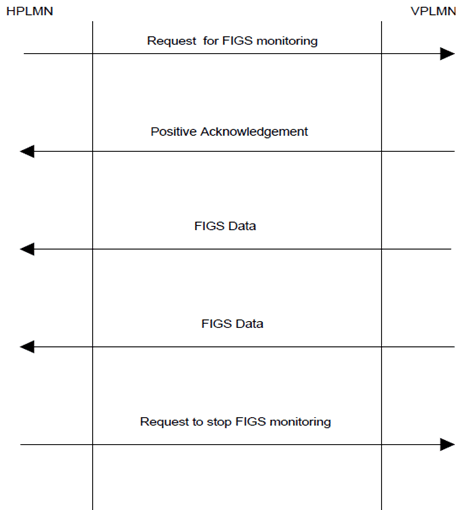
The HPLMN shall be able to request a VPLMN to monitor a subscriber.
See Annex A for the definition of the information to be sent for each call event.
If the VPLMN cannot monitor the subscriber, it shall indicate this as a response to the FIGS request.
The FDS will process this information and may then limit the activities of the subscriber using ODB or terminate the subscriber activities using IST, or may allow the subscriber to proceed.
When the home network no longer wishes the subscriber to be monitored by the VPLMN it requests the VPLMN to stop monitoring the activities of the subscriber.
Figure B.1 shows the sequence of FIGS messages passed during a normal case.
5 Service conditions p. 7
5.1 Control of monitoring of subscriber activities p. 7
The HPLMN can request a VPLMN to begin monitoring the activities of a subscriber when the subscriber has registers on that VPLMN or at any time after registration. If the VPLMN is able to monitor a subscriber as requested it shall send a confirmation of monitoring message to the HPLMN.
The HPLMN does not need to know the status of the target subscriber before initiation or subsequent termination of fraud information gathering.
Fraud information cannot be switched on or off by the subscriber or other (unauthorised) party.
Subscribers upon which fraud information gathering has been set shall not be able by interrogating the network to determine that they are subject to fraud information gathering.
Subscribers upon which fraud information gathering has been set shall not be able, for example by significant changes to normal call set up times, speech quality or general transmission characteristics, to determine that they are subject to fraud information gathering.
If the VPLMN receives a request to monitor the activities of a subscriber and an activity to be monitored is already ongoing it is not necessary for the VPLMN to send information on this particular activity to the HPLMN.
If the VPLMN receives a request to cease monitoring the activities of a subscriber and an activity is already ongoing and being monitored, the VPLMN shall immediately cease sending information on this activity to the HPLMN.
5.2 Number of calls monitored by a VPLMN p. 7
If the VPLMN has to monitor the activities of a large number of subscribers for FIGS this may degrade the performance of the VPLMN. Each VPLMN (in reality, each network entity involved in FIGS monitoring) will therefore have a maximum number of subscribers that it can monitor.
If the number of monitored subscribers has reached this upper limit the VPLMN shall reject requests for monitoring of subscribers from HPLMNs until the number of monitored subscribers decreases below the limit.
Each VPLMN may have a limit per HPLMN on the number of subscribers from that HPLMN that it will monitor. When an HPLMN has requested a VPLMN to monitor a number of subscribers equal to the limit for that HPLMN, the VPLMN can refuse any subsequent requests for FIGS monitoring from that PLMN, until the number of monitored subscribers drops below the limit. The principles behind the setting of these limits are outside the scope of this specification.
In order to minimise the number of subscribers that a VPLMN has to monitor, the HPLMN should ideally limit itself to requesting information about subscriber's monitored activities in:
- the current VPLMN;
- the last previously served VPLMN.
5.3 Interworking with non-supporting networks p. 7
If the HPLMN does not receive a positive acknowledgement to the request for FIGS monitoring sent to a VPLMN, it shall assume that the VPLMN does not support FIGS. The HPLMN may then act as appropriate (e.g. put appropriate ODB categories in place).
5.4 Information Delivery Time p. 8
The need for up to date information is a critical part of any fraud information system. The sooner data is transferred to the HPLMN, the sooner fraud can be stopped. Therefore the prescribed information shall be transferred from the VPLMN network to the HPLMN within two minutes of the occurrence of a FIGS-monitored event, if real time implementations of FIGS are used.
The information should be transferred from the VPLMN to the HPLMN over appropriate communication links.
6 Monitored activity p. 8
The authorised party can request the VPLMN to monitor both call activity and supplementary services.
The monitoring of call activity shall take the form of transmission of call information from the VPLMN to the HPLMN, at the start and end of all calls. For long calls, the VPLMN shall also send partial call information a certain time (e.g. 15 minutes) after the call has begun.
Call information shall be sent to the HPLMN by the VPLMN on the invocation of all supplementary services, e.g.:
- call deflection;
- call forwarding;
- call hold;
- Multi Party (MPTYY);
- Explicit Call Transfer (ECT).
7 Interface between HPLMN and FDS p. 8
Information gathered by the HPLMN may be transferred to Non GSM systems, e.g. an FDS. These systems will decide if the monitored activity is fraudulent and will advise the home network to take appropriate action, e.g. send an IST command to the VPLMN, change the subscriber's ODB categories.
The contents of call information messages to be transferred on this interface shall be specified but not the transfer mechanism. This is in line with the approach used for the X-interface as specified in TS 42.033. The message formats are defined in annex A.
The system needs the ability to handle the volume of information returned to the home network.
8 Security Requirements between HPLMN and VPLMN p. 8
It is expected that there will be a need for authentication, data integrity and confidentiality of the communication made between PLMNs.
These issues are for study under other work items within the SMG 10 work programme.
A (Normative) Information transferred by the VPLMN p. 9
The reports generated by the VPLMN shall take the form of "call information" records for each monitored subscriber. The content of the call information will depend on the type of event (call start, end etc.). To simplify matters, there will be one format for both MO and MT calls with an MO/MT indicator within the call information to distinguish between the two.
A partial call information will be sent to the HPLMN when there is an mid-call invocation of a supplementary service and when a call in progress has exceeded a defined duration.
Justification is given for the content of the call information message.
| Information |
|---|
| Dialled digits |
| A subscriber |
| B subscriber |
| C subscriber |
| CGI |
| IMSI |
| IMEI |
| Call Start Time/Date |
| Call Duration |
| Call Reference |
| MO/MT indicator |
| Visited MSC address |
| Type of SS event |
| Type of Basic Service |
The Dialled digits are required as these are an important indicator in deciding if a call is fraudulent or not - certain call destinations are more likely to be called fraudulently than others.
A subscriber can be used to identify the subscriber
B, C subscriber are relevant as some call destinations are more subject to fraud than others.
Cell Global Identifier (CGI) is relevant as some cells in a PLMN are more subject to fraud than others.
The IMSI is used to reference the subscriber.
The IMEI can be used to check if a stolen handset has been used.
The Call Start Time/Date is required so that the call duration can be calculated (if the call end time and not call duration is given at call conclusion) and because the call start time can also an important indicator of fraudulency.
The Call Duration gives the duration of the call at the sending of the partial call information - call duration can be an important indicator of fraudulency. If call end is sent instead, the duration can be calculated using the call start and end times.
The Call Reference is used to reference a particular call.
The MO/MT indicator is required because call charging is different for MO and MT calls.
The Visited MSC address gives the PLMN on which the call was made.
The Type of SS event record is sent if the "call" start is actually the invocation of a supplementary service, e.g. ECT. The Type of SS event is required as this can help to indicate if the mobile is being fraudulently used or not.
The Type of Basic Service indicates whether a teleservice or bearer service is being used and which sort of teleservice or bearer service is being used and is sent if the event is a call and not a supplementary service. The Type of Basic Service is required as this can help to indicate if the mobile station is being fraudulently used or not.
B (Normative) Message flow in FIGS monitoring, normal procedure p. 11